North Korean hackers have begun exploiting a newly discovered Linux variant of FASTCash malware to infiltrate the payment switch systems of financial institutions, enabling unauthorized cash withdrawals.
While earlier FASTCash versions focused on Windows and IBM AIX (Unix) systems, a recent report by security researcher HaxRob uncovers an undetected Linux variant that specifically targets Ubuntu 22.04 LTS distributions.
Money-stealing history
CISA first issued a warning about the FASTCash ATM cash-out scheme in December 2018, linking the operations to the state-sponsored North Korean hacking group, ‘Hidden Cobra.’
Their investigations revealed that these cybercriminals have been deploying FASTCash since at least 2016, executing simultaneous ATM withdrawal attacks across 30 or more countries, with each operation resulting in tens of millions of dollars stolen.
In 2020, the U.S. Cyber Command reiterated the threat, connecting the resurgence of FASTCash 2.0 activity to APT38, also known as Lazarus.
By 2021, indictments were announced against three North Koreans accused of orchestrating these schemes, responsible for stealing over $1.3 billion from financial institutions worldwide.
Cashing out from Linux
The latest variant discovered by HaxRob was first uploaded to VirusTotal in June 2023, exhibiting significant operational similarities to earlier Windows and AIX variants.
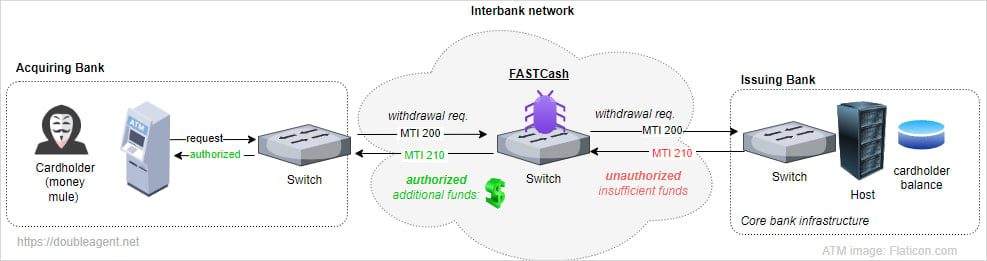
This malware is delivered as a shared library that’s injected into a running process on a payment switch server using the ‘ptrace‘ system call, allowing it to hook into network functions.
Payment switches act as intermediaries, facilitating communication between ATMs/PoS terminals and the bank’s central systems by routing transaction requests and responses.
The malware intercepts and alters ISO8583 transaction messages, which are standard in the financial industry for debit and credit card processing.
It specifically targets transaction messages related to insufficient funds, replacing the “decline” response with “approve.”
FASTCash operational overview
Source: doubleagent.net
Additionally, the manipulated message includes a random sum between 12,000 and 30,000 Turkish Lira ($350 – $875) to authorize the fraudulent transaction.
Once the tampered message is sent to the bank’s central systems with approval codes (DE38, DE39) and the amount (DE54), the transaction is approved, and a money mule working with the hackers withdraws cash from an ATM.
At the time of its discovery, the Linux variant of FASTCash was undetected on VirusTotal, enabling the hackers to carry out their transactions unnoticed by typical security tools.
HaxRob also noted a new Windows version was submitted to VirusTotal in September 2024, indicating the hackers are actively updating their malware toolkit.
Source: BleepingComputer, Bill Toulas