Since 2022, a sophisticated Linux malware known as ‘sedexp‘ has been successfully avoiding detection by leveraging a persistence technique not yet recognized in the MITRE ATT&CK framework.
Discovered by Stroz Friedberg, a risk management firm under Aon Insurance, the malware grants its operators the ability to establish reverse shells, facilitating remote access and advancing the attack.
“At the time of this writing, the persistence technique employed (udev rules) has yet to be documented by MITRE ATT&CK,” the researchers pointed out, underscoring that sedexp represents a highly advanced threat, capable of concealing itself in plain sight.
Persisting via udev rules
‘udev’ is a device management system within the Linux kernel that manages device nodes located in the /dev directory. This directory holds files representing the hardware components available on the system, such as storage drives, network interfaces, and USB drives.
Node files are dynamically created or removed as devices are connected or disconnected. In addition, udev is responsible for loading the appropriate drivers.
Udev rules, which are text-based configuration files, define how the device manager should handle certain devices or events. These rules are typically found in ‘/etc/udev/rules.d/’ or ‘/lib/udev/rules.d/.’
Each rule consists of three key parameters: the action to trigger the rule (ACTION==”add”), the device name (KERNEL==”sdb1″), and the command to execute when the specified conditions are met (RUN+=”/path/to/script”).
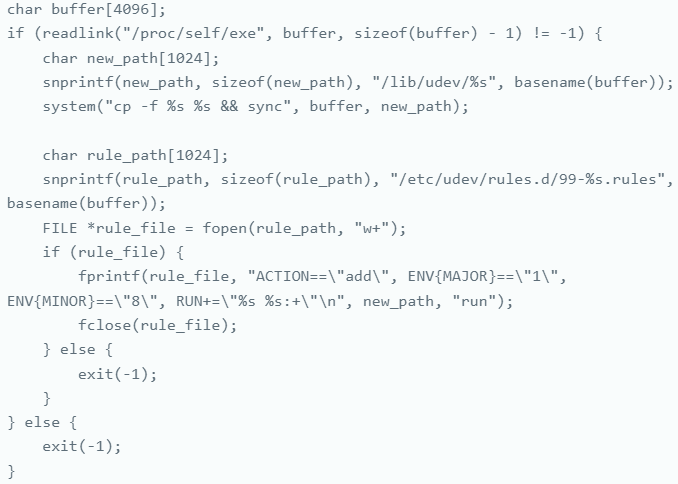
In compromised systems, the sedexp malware adds the following udev rule:
ACTION==”add”, ENV{MAJOR}==”1″, ENV{MINOR}==”8″, RUN+=”asedexpb run:+”
This rule activates whenever a new device is added, verifying whether its major and minor numbers correspond to ‘/dev/random,’ a device initialized during system boot and used as a random number generator by numerous applications and system processes.
The final part of the rule (RUN+= “asedexpb run:+”) runs the malware’s script, ‘asedexpb.’ By linking the script execution to /dev/random, the attackers ensure the malware is frequently executed.
Crucially, /dev/random is a critical system component that is not typically monitored by security solutions, making it an ideal target for evasion, allowing the malware to remain undetected.
Establishing persistence on the system
Source: Aon
Primary operational capabilities
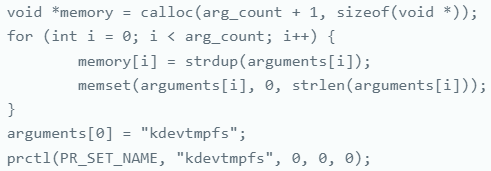
The malware disguises its process as ‘kdevtmpfs,’ mimicking a legitimate system process, which allows it to blend in with regular activities and evade detection by conventional methods.
Process naming to blend with system operations
Source: Aon
In terms of its functionality, the malware leverages either forkpty or pipes in combination with a forked process to establish a reverse shell, providing the attacker with remote access to the compromised device.
Sedexp also uses memory manipulation techniques to obscure any files containing the string “sedexp” from standard commands like ‘ls’ or ‘find,’ effectively hiding its presence within the system.
Furthermore, it has the capability to modify memory contents, allowing it to inject malicious code or alter the behavior of existing applications and system processes.
Researchers noted that sedexp has been actively used in the wild since at least 2022, and its presence has been detected in multiple online sandboxes. Despite this, detection remains minimal—on VirusTotal, only two antivirus engines flagged the three sedexp samples mentioned in the report as malicious.
According to Stroz Friedberg, the malware has been used to conceal credit card scraping code on compromised web servers, suggesting its involvement in financially motivated attacks.
Source: BleepingComputer, Bill Toulas
Read more news at our blog