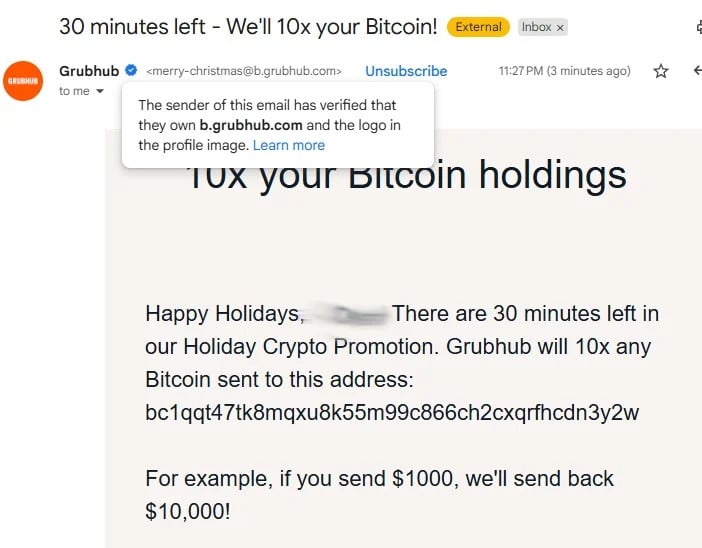
Grubhub users received fraudulent messages that appeared to come from a company email address and promised a tenfold bitcoin payout in exchange for a transfer to a specified wallet.
Specifically, the emails claimed to be part of a ‘Holiday Crypto Promotion’ and originated from an address on ‘b.grubhub.com’. Notably, this domain is a legitimate subdomain that Grubhub uses to communicate with its merchant partners and restaurants.
“There are 30 minutes left in our Holiday Crypto Promotion. Grubhub will 10x any Bitcoin sent to this address […]. For example, if you send $1000, we’ll send back $10,000,” reads the fraudulent message.
Scam Emails Use Legitimate-Looking Addresses
Moreover, some of the emails arrived from the ‘[email protected]’ and ‘[email protected]’ addresses starting December 24. In addition, the messages included the recipient’s name, which made the scam appear more credible.
Crypto scam message from Grubhub
Source: RazMusk
Overall, this scheme follows a classic crypto reward scam pattern, in which attackers lure victims into sending funds by falsely promising a larger return.
Meanwhile, some users speculate [1, 2] that a DNS takeover attack enabled the scam. Such an attack could allow threat actors to send emails that pass authenticity checks. However, the company has not provided details explaining exactly how the incident occurred.
In a statement to BleepingComputer, however, a Grubhub spokesperson said the company isolated the problem and is working to prevent a recurrence.
“We’re aware of unauthorized messages that appear to have been sent by Grubhub to some of our merchant partners. We immediately investigated, contained the issue, and are taking steps to ensure it doesn’t happen again,” Grubhub said.
Prior Security Incident Raises Concerns
Earlier this year, the food delivery company announced that a threat actor accessed names, email addresses, and phone numbers belonging to its customers, merchants, and drivers.
The intrusion originated from an account that a third-party used to provide support services to Grubhub.
Source: BleepingComputer, Ionut Ilascu
Read more at Impreza News