Ransomware group activity in Latin America has increased this year, with a more significant boost in attacks targeting corporate and government sectors in the region.
According to ESET’s “Security Report”, 96% of organizations expressed concern about ransomware as a latent threat, with 21% admitting to having suffered an attack of this type in the last two years. Of this last group, 77% were able to recover their information due to the backup policies they have in place, while 4% said they had paid to recover their data. Of the organizations surveyed, 84% denied being willing to negotiate data ransom payments.
“One of the main challenges to face in the near future will be the increase in spear phishing campaigns — directed at a specific target. The increased risks associated with the greater use of technologies in the post-pandemic period and the need to improve the level of awareness of company employees at all levels must be taken into account”, comments David González Cuautle, cybersecurity researcher at ESET Latin America.
“The implementation of cybersecurity in Latin America depends on the type of organization and, according to the ESET report, there are issues in which there is a convergence, regardless of the sector: the theft or leakage of information in companies is the biggest concern, with 66 %, and is associated with improper access to systems, that is, the increase in attacks that aim to exploit a vulnerability through targeted phishing campaigns (spear phishing) or the installation of malicious codes such as ransomware or remote access trojans”, he adds Cuautle.
The most active ransomware groups in the Latin America region so far this year, according to ESET, are:

SiegedSec: known for its motto of harassing the victim’s safety, hence its name, in English “siege”, which can be translated as harass or besiege. Its modus operandi is to extort the victim to the point of leaving them with only the option of paying for the ransom of their information or, in the worst case, selling it on dark web forums or Telegram.
Since the beginning of its activities in February 2022, linked to the GhostSec ransomware group, it has demonstrated that it has no preference for its targets, managing to affect sectors around the world, such as healthcare, information technology, insurance, accounting, rights and finance. Regarding its activity in Latin America, SiegedSec was able to obtain intranet documents, databases, user information and details of breached organizations across multiple sectors in Colombia, with government and healthcare entities among the most affected.
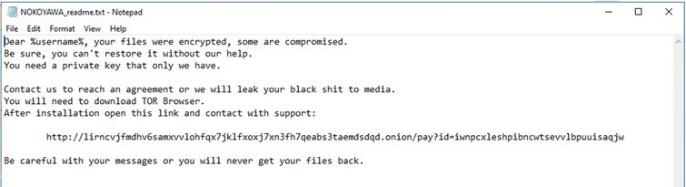
Nokoyawa: of Russian origin and starting its activities in February last year, this group is characterized by being the only one to use highly sophisticated encryption — elliptic curve cryptography, or ECC, in English —, adding its own homonymous file extension (Nokoyawa) . This group managed to obtain a significant amount of information from a laboratory in Brazil’s healthcare sector by the third quarter of 2023.

ALPHV/BlackCat: the way this group has operated since its appearance in November 2021 is through ransomware-as-a-service (RaaS), as its attacks do not occur randomly or through spam campaigns, but rather, its targets are determined by the associates they count on. In other words, they join forces to carry out attacks on already identified targets. This makes its modus operandi specific to each use case, as are the techniques used during its attacks.
In mid-2023, ALPHV released confidential information about the exfiltration of data from one of Mexico’s largest companies through its Telegram channel. Likewise, the public sector was not exempt from this attack.

Stormous and his alliance with GhostSec: the Stormous group emerged in mid-2021. Initially, the group, of Arab origin, publicized attacks on the United States through its Telegram channels and dark web forums. Due to the Russia-Ukraine conflict, their objectives were modified and, in mid-July this year, they officially announced a partnership with the hacktivist group GhostSec to attack not only the United States, but also countries in Latin America, including the government of Cuba. .

Vice Society: one of the most active in late 2022 and early 2023. Most incidences have occurred in the education and healthcare industries, but there is also evidence that another sector this ransomware group is targeting is the manufacturing sector in countries such as Brazil, Argentina , Switzerland and Israel. It is worth noting that they developed their own custom ransomware generator, opting for more robust encryption methods, which indicates that the group is preparing for its own ransomware-as-a-service (RaaS) operation.
Look this
Royal ransomware gang claimed more than 350 victims in 12 months
LockBit ransomware gang leaks 43GB of Boeing data
From ESET Latin America, we share some recommendations that can help protect information:
- Have a policy to perform periodic backups: This will allow data, if affected by ransomware, to be restored. According to the ESET Security Report in Latin America, 88% of organizations surveyed have implemented this recommendation.
- Establish a policy for updates and corrections for each asset (operational and network): By having all systems, applications and devices up to date, the vulnerability for cybercriminals to exploit software flaws or obsolete protocols is considerably reduced. In the ESET Security Report in Latin America, 45% of organizations stated that they carry out security updates more than twice a year, indicating that there is still a lot of effort to be made.
- Education and awareness: Continuous training of employees at all levels on best security practices and attack vector trends in the region is essential to prevent a cybercriminal from succeeding. One area of opportunity for organizations where many ransomware attacks are successful is the lack of a training and awareness program (only 28% of respondents in the ESET Security Report of Latin America claimed to have this program).
- Have a policy on the principle of least privilege: By establishing only the privileges necessary for the employee to carry out their activities, the ransomware’s ability to spread to other systems or applications is limited.
- Network security: Firewalls, network segmentation along with access rules and VPN usage limit the possibility of any malware spreading.
- Incident response and business continuity plan: It is important to know how to respond to any incident or contingency that may occur in the organization, minimizing the impact on the business and ensuring that it continues to function. 42% of respondents indicated they have an incident response plan, while 38% do not have a business continuity plan.
- Count on advanced security solutions: implementing security solutions that detect and block anomalous or suspicious behavior, such as an EDR (endpoint detection and response) and anti-malware solutions, would enable business continuity, providing a commercial advantage by gaining the trust of customers by knowing that their information is adequately protected.
See the original post at: CisoAdvisor






















