Cybercriminals are capitalizing on the significant business disruption caused by CrowdStrike’s flawed update on Friday, targeting companies with data wipers and remote access tools.
As businesses seek help to repair affected Windows hosts, researchers and government agencies have observed a surge in phishing emails attempting to exploit the situation.
Official channel communication
In an update today, CrowdStrike announced it is “actively assisting customers” affected by the recent content update that crashed millions of Windows hosts worldwide.
The company advises customers to verify they are communicating with legitimate representatives through official channels, warning that adversaries and bad actors will try to exploit events like this.”
“I encourage everyone to remain vigilant and ensure that you’re engaging with official CrowdStrike representatives. Our blog and technical support will continue to be the official channels for the latest updates,” said George Kurtz, CrowdStrike CEO.
The U.K. National Cyber Security Center (NCSC) also warned of an increase in phishing messages attempting to exploit the outage.
Automated malware analysis platform AnyRun noted “an increase in attempts at impersonating CrowdStrike that can potentially lead to phishing” [1, 2, 3].
Malware cloaked as fixes and updates
On Saturday, cybersecurity researcher g0njxa reported a malware campaign targeting BBVA bank customers, offering a fake CrowdStrike Hotfix update that installs the Remcos RAT.
The fake hotfix was promoted through a phishing site, portalintranetgrupobbva[.]com, which posed as a BBVA Intranet portal.
The malicious archive included instructions for employees and partners to install the update to avoid errors when connecting to the company’s internal network.
“Mandatory update to avoid connection and synchronization errors to the company’s internal network,” read the ‘instrucciones.txt’ file in Spanish.
AnyRun, who also tweeted about the campaign, stated that the fake hotfix delivers HijackLoader, which then drops the Remcos remote access tool on the infected system.
In another warning, AnyRun announced that attackers are distributing a data wiper under the guise of a CrowdStrike update.
“It decimates the system by overwriting files with zero bytes and then reports it over #Telegram,” AnyRun reported.
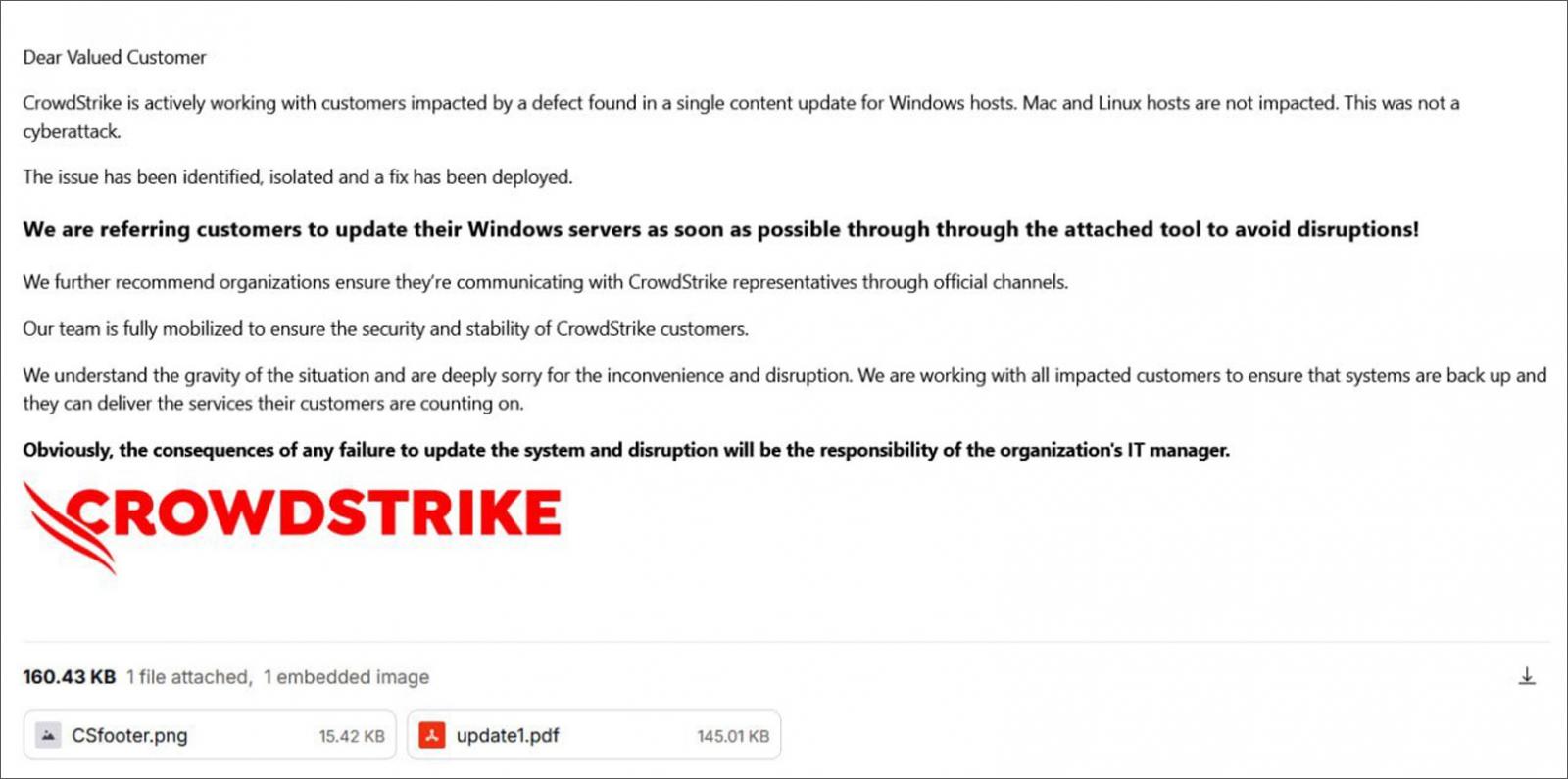
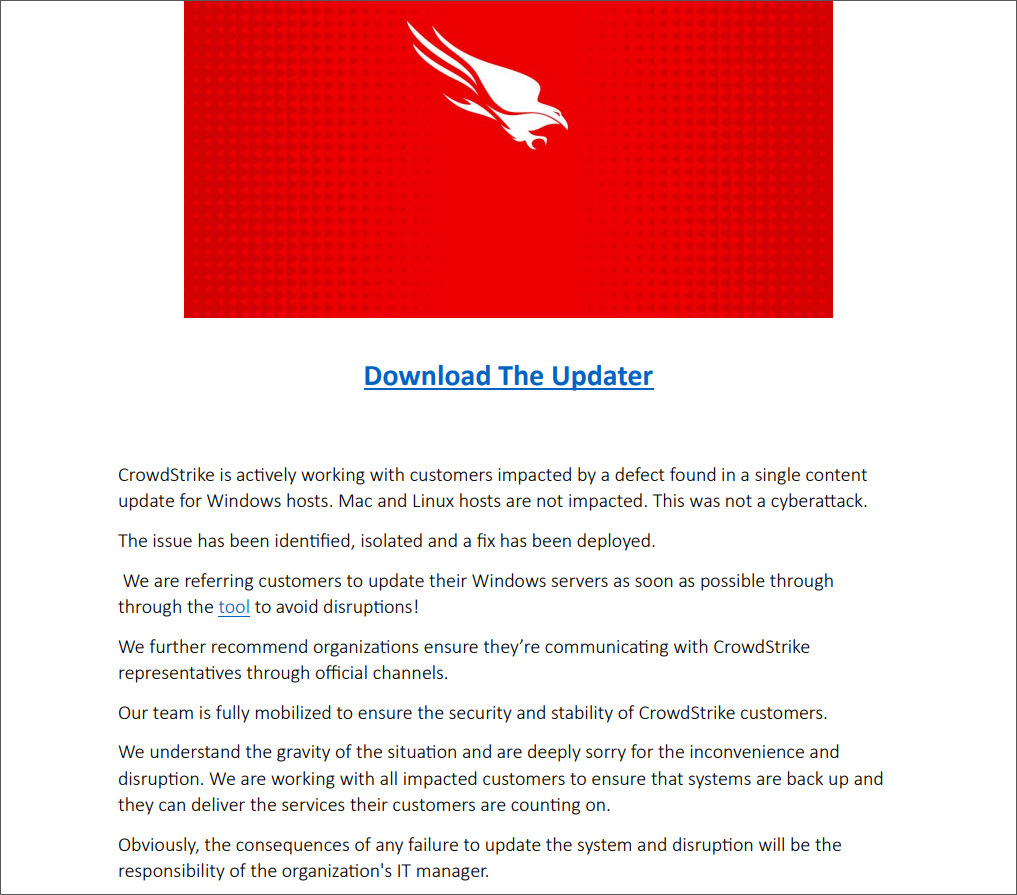
This campaign was claimed by the pro-Iranian hacktivist group Handala, who stated on Twitter that they impersonated CrowdStrike in emails to Israeli companies to distribute the data wiper.
The threat actors used the domain ‘crowdstrike.com.vc‘ to send emails, telling customers that a tool was created to bring Windows systems back online.
Phishing email send by the Handala threat actors
The emails include a PDF, seen by BleepingComputer, with further instructions on running the fake update, as well as a link to download a malicious ZIP archive from a file hosting service. This ZIP file contains an executable named ‘Crowdstrike.exe.’
Malicious attachment pushing data wiper
Source: BleepingComputer
Once the fake CrowdStrike update is executed, the data wiper is extracted to a folder under %Temp% and launched to destroy data stored on the device.
Millions of Windows hosts crashed
The defect in CrowdStrike’s software update had a massive impact on Windows systems at numerous organizations, making it too good an opportunity for cybercriminals to pass up.
According to Microsoft, the faulty update “affected 8.5 million Windows devices, or less than one percent of all Windows machines.”
The damage occurred within 78 minutes, between 04:09 UTC and 05:27 UTC.
Despite the low percentage of affected systems and CrowdStrike’s swift efforts to correct the issue, the impact was significant.
Computer crashes led to thousands of flight cancellations, disrupted activity at financial companies, brought down hospitals, media organizations, railways, and even affected emergency services.
In a post-mortem blog post on Saturday, CrowdStrike explained that the cause of the outage was a channel file (sensor configuration) update to Windows hosts (version 7.11 and above) that triggered a logic error, leading to a crash.
While the channel file responsible for the crashes has been identified and no longer causes problems, companies still struggling to restore systems to normal operations can follow CrowdStrike’s instructions to recover individual hosts, BitLocker Keys, and cloud-based environments.
Source: BleepingComputer, Ionut Ilascu