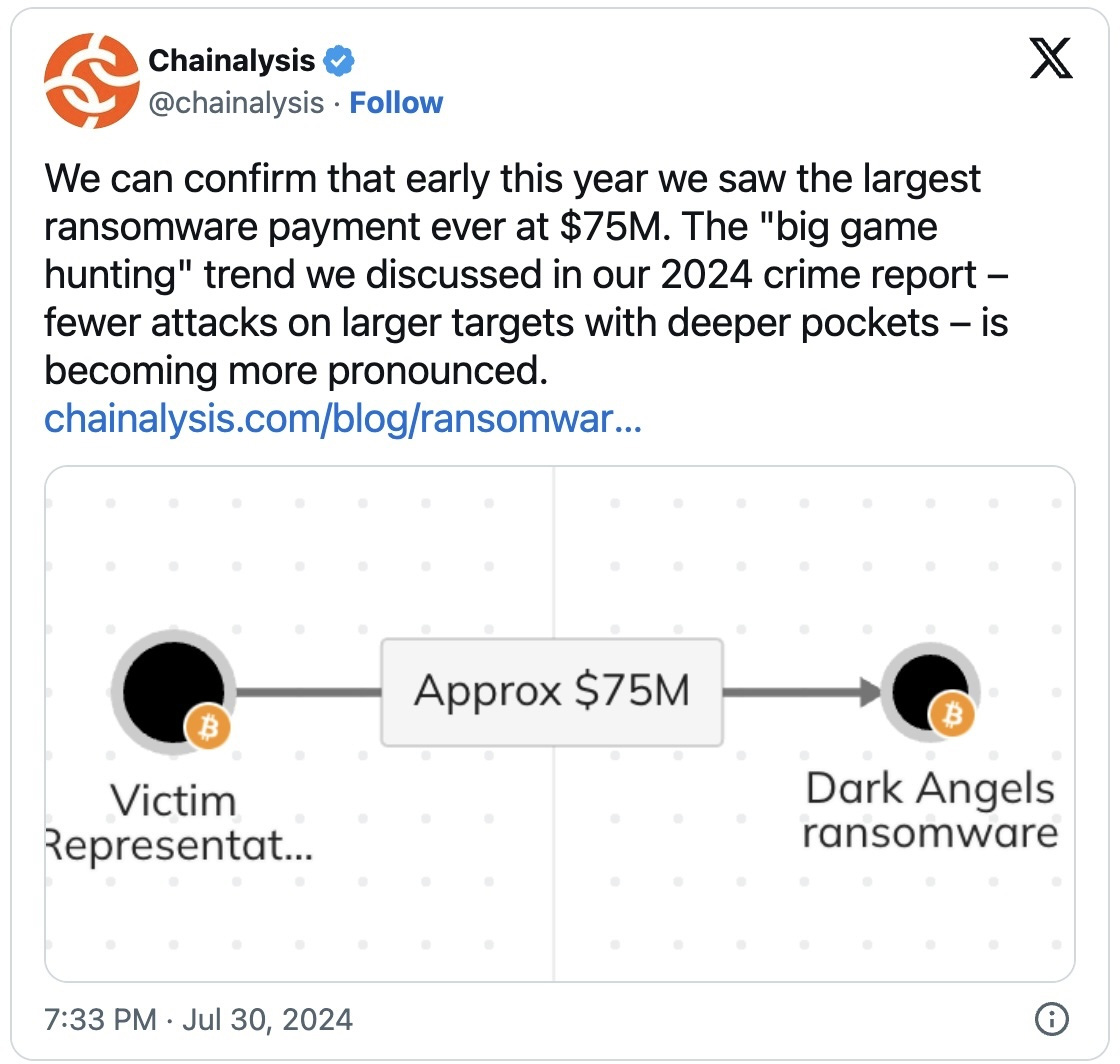
A Fortune 50 company reportedly paid a staggering $75 million ransom to the Dark Angels ransomware group, as detailed in a report by Zscaler ThreatLabz.
“The early 2024 victim paid Dark Angels a record-breaking $75 million, surpassing any previously known amounts. This unprecedented sum is likely to inspire other attackers to emulate the group’s successful tactics, which we outline below,” states the 2024 Zscaler Ransomware Report.
This record ransom was corroborated by Chainalysis, a crypto intelligence firm, which confirmed the payment in a post on X.
Before this incident, the largest known ransom payment was $40 million, paid by insurance giant CNA after an Evil Corp ransomware attack.
Zscaler did not reveal the identity of the company that paid the $75 million ransom but confirmed it was a Fortune 50 company targeted in early 2024.
One notable cyberattack on a Fortune 50 company in February 2024 involved Cencora, a pharmaceutical giant ranked #10. No ransomware group publicly claimed responsibility, suggesting a possible ransom payment.
BleepingComputer reached out to Cencora to inquire about a possible payment to Dark Angels but has yet to receive a response.
Who are the Dark Angels
Dark Angels is a ransomware operation that emerged in May 2022, quickly becoming a global threat by targeting companies worldwide.
Similar to other human-operated ransomware groups, Dark Angels infiltrates corporate networks and moves laterally to gain administrative privileges. During this process, they also exfiltrate sensitive data from compromised servers, which they use to increase pressure on their victims during ransom negotiations.
Once they gain control of the Windows domain controller, the attackers deploy their ransomware to encrypt all connected devices within the network.
Initially, the group utilized Windows and VMware ESXi encryptors based on the leaked Babuk ransomware source code. However, they later transitioned to a Linux encryptor, previously used by Ragnar Locker since 2021. Ragnar Locker’s operations were disrupted by law enforcement in 2023.
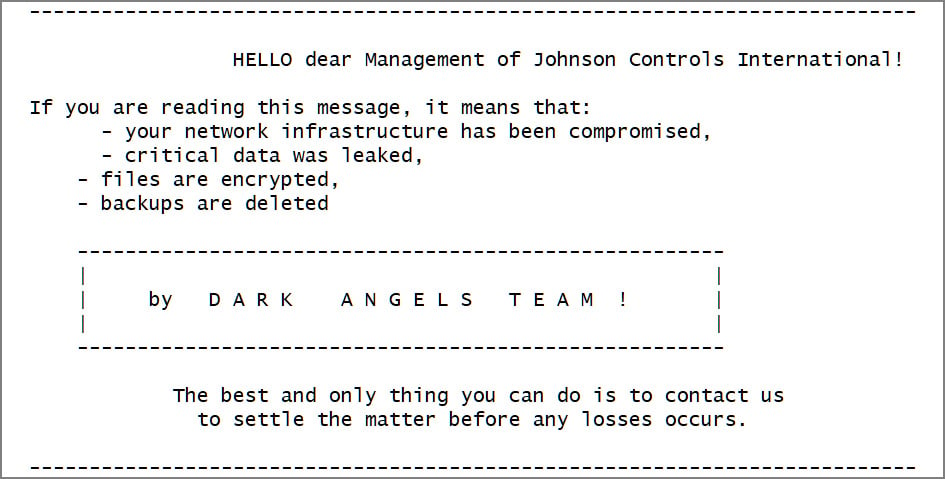
Dark Angels employed this Linux encryptor in an attack on Johnson Controls, encrypting the company’s VMware ESXi servers. During this incident, they claimed to have stolen 27TB of data and demanded a $51 million ransom.
Dark Angels ransom note
Source: BleepingComputer
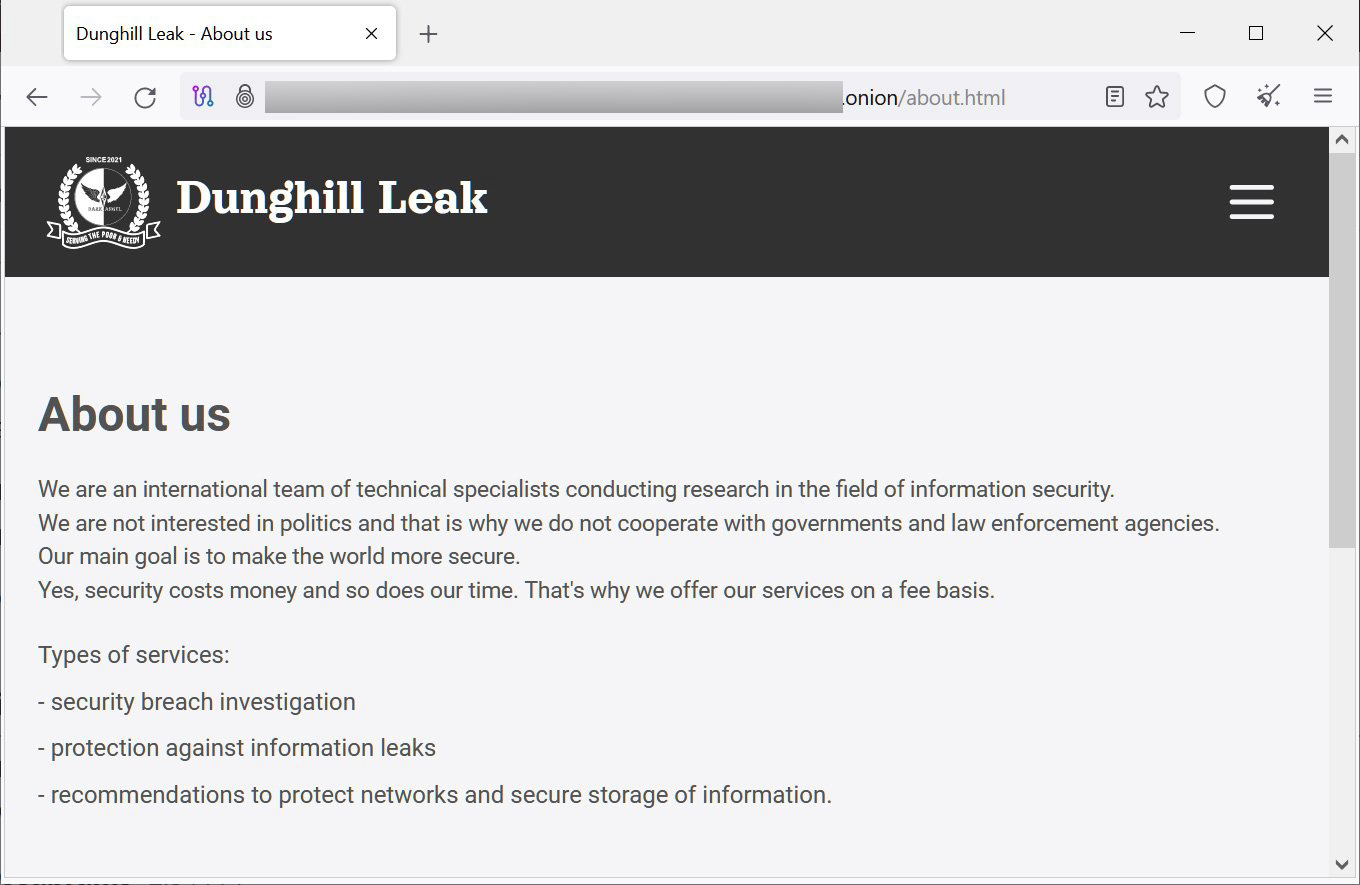
The group also runs a data leak site called ‘Dunghill Leaks‘, where they threaten to publish stolen data if a ransom is not paid.
Dark Angel’s ‘Dunghill’ Leaks data leak site
Source: BleepingComputer
According to Zscaler ThreatLabz, Dark Angels follows a “Big Game Hunting” strategy, focusing on a few high-value targets to secure substantial ransoms rather than attacking numerous smaller entities.
“The Dark Angels group adopts a highly targeted strategy, typically attacking one large organization at a time,” note the researchers at Zscaler ThreatLabz.
This approach contrasts sharply with the methods of most ransomware groups, which often target victims indiscriminately and rely on affiliate networks of initial access brokers and penetration testers.”
Chainalysis notes that the Big Game Hunting tactic has become increasingly prevalent among ransomware gangs in recent years.
Source: BleepingComputer, Lawrence Abrams