This development suggests that the group could be broadening its attacks across the Linux platform, leading to an expanded victim pool and more successful ransom negotiations.
This has been a known trend for years now, with most ransomware groups shifting focus towards ESXi virtual machines after enterprises switched to using them for data storage and hosting critical applications due to their much more efficient resource handling.
Taking down an organization’s ESXi VMs will lead to major business operations disruptions and outages, while encrypting files and backups drastically reduces the victims’ options to recover impacted data.
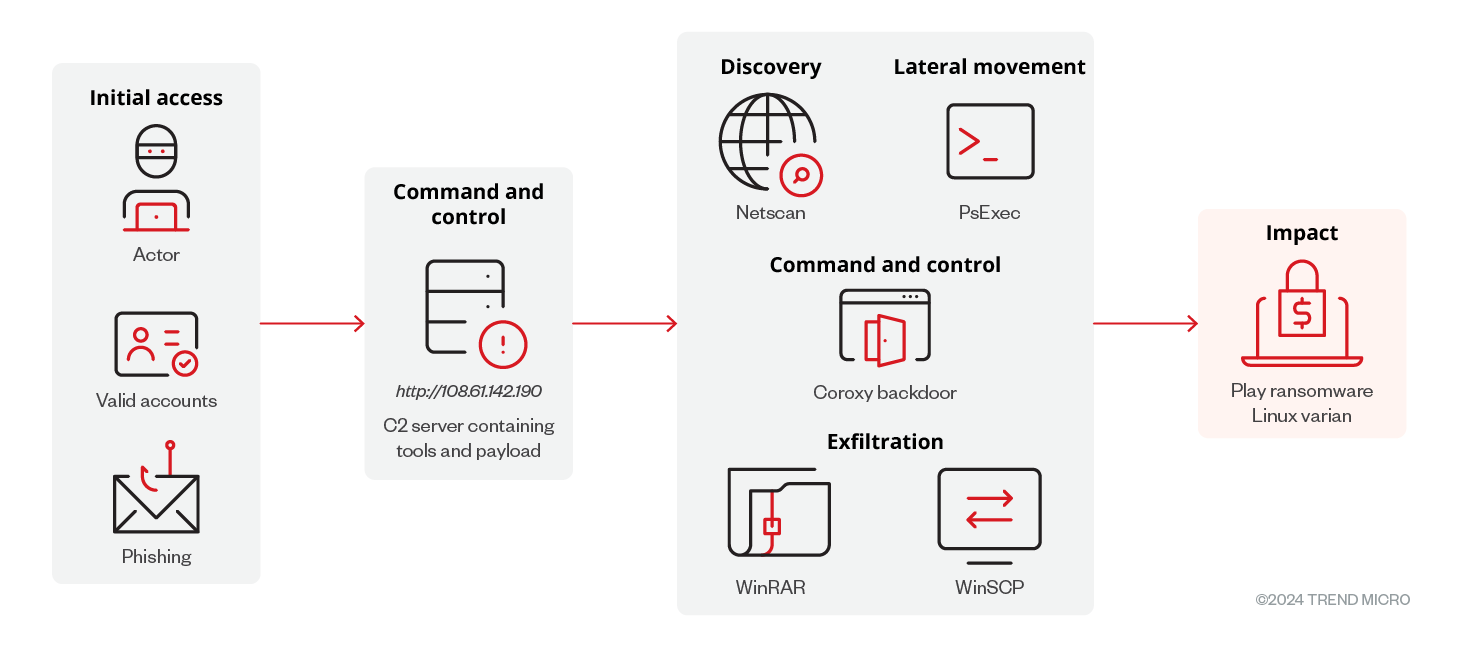
Play ransomware Linux attack flow (Trend Micro)
While investigating this Play ransomware sample, Trend Micro also found that the ransomware gang uses the URL-shortening services provided by a threat actor tracked as Prolific Puma.
After successfully launching, Play ransomware Linux samples will scan and power off all VMs found in the compromised environment and start encrypting files (e.g., VM disk, configuration, and metadata files), adding the .PLAY extension at the end of each file. To power off all running VMware ESXi virtual machines so that they can be encrypted, Trend Micro says the encryptor will execute the following code:
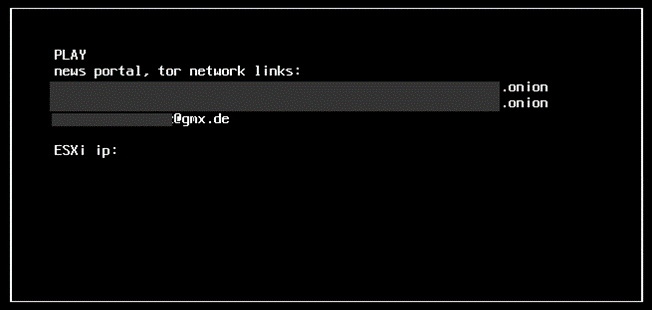
/bin/sh -c "for vmid in $(vim-cmd vmsvc/getallvms | grep -v Vmid | awk '{print $1}'); do vim-cmd vmsvc/power.off $vmid; done"As BleepingComputer found while analyzing it, this variant is designed to specifically target VMFS (Virtual Machine File System), which is used by VMware’s vSphere server virtualization suite. It will also drop a ransom note in the VM’s root directory, which will be displayed in the ESXi client’s login portal (and the console after the VM is rebooted).
Play ransomware Linux console ransom note (Trend Micro)
Source: BleepingComputer, Sergiu Gatlan