Ransomware has become extremely common over the past few years, being one of the easiest ways that cybercriminals have found to snatch money from unprotected companies. However, a group of hacktivists decided, in an unprecedented way, to use this type of malware not for their own profit, but to demonstrate support for the various protests of Indian farmers that have been taking place in the country since November 2020.
The strain, which was identified by researchers at cybersecurity company Quick Heal, is called Sarbloh and is being disseminated via infected Microsoft Word files. The targets are mostly government agencies and private companies that are directly involved with the issue; however, experts preferred not to disclose the names of the victims detected so far.
After installing itself on the machine, the ransomware uses “military-grade encryption” to encrypt all of its files and change its extension to .sarbloh. Then, a hijacking screen is displayed confirming that there is no point in opening the wallet – the attackers do not want any amount of money and they only intend to release the decryption key when “the farmers’ demands are met”.
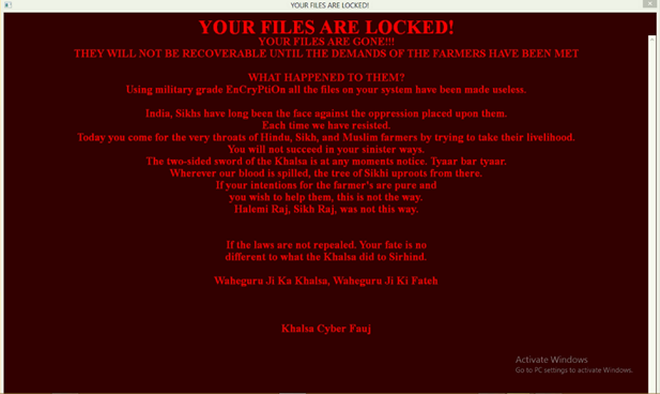
It is worth remembering that the protests call for the annulment of a series of laws aimed at reforming the Indian agrarian market; farmers, however, fear that the new rules will weaken their dealings with the government, which culturally acquires commodities of farmers at fixed prices. According to the protesters, there is a great chance that the country’s agricultural market ends up dominated by large corporations.
Sarbloh’s methodology is somewhat innovative. As much as ransomware is increasingly accessible (it is possible to acquire “ready-made kits” to infect targets on specialized forums on the dark web), there is no other record of this type of malware being used for digital activism. This sets precedents for other groups around the world do the same for their own social or political struggles.

“Malicious actors have demonstrated innovation through their constantly evolving attack strategies. We will continue to analyze the threat environment and implement security measures for our users. Avoid clicking on suspicious links found in spam emails, “said Quick Heal.
“In addition, back up the data so that it can be recovered in case of compromise and continue to update antivirus solutions to remain protected,” he concludes.
Source: The Quint, Tribune India























