The Mad Liberator, a newly tracked data extortion group, is specifically targeting AnyDesk users by running a counterfeit Microsoft Windows update screen to divert attention while siphoning data from the target device.
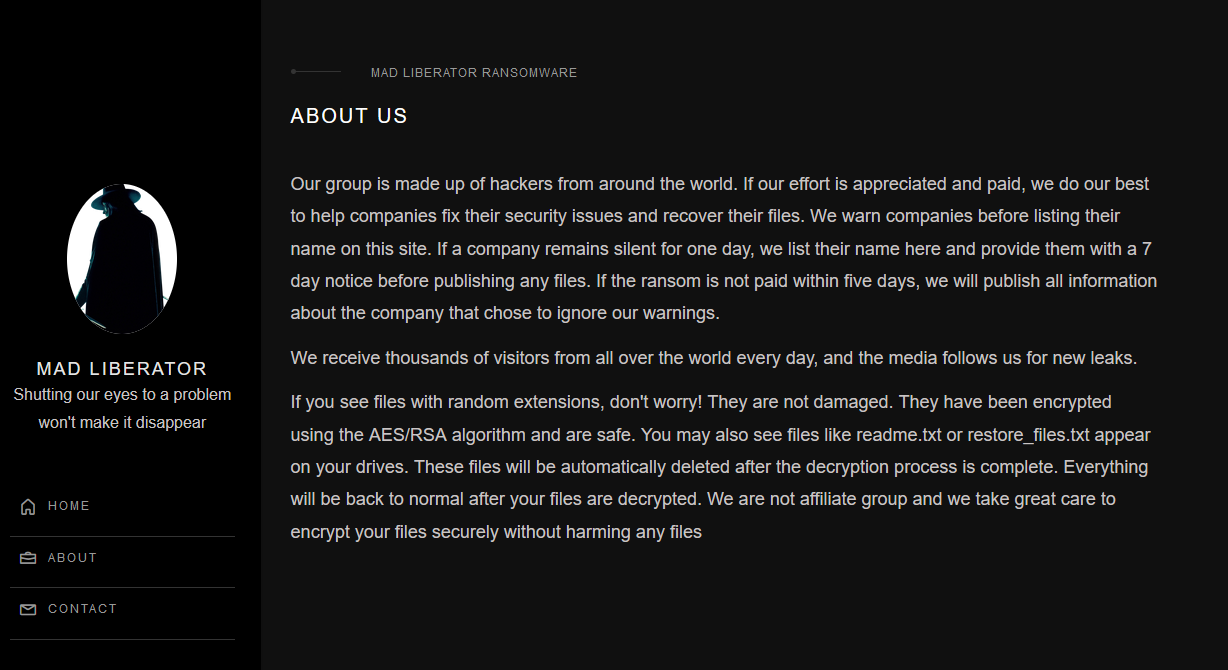
The group’s operations surfaced in July, and although researchers have yet to observe any data encryption incidents, the gang claims on their leak site to employ AES/RSA algorithms to lock files.
Mad Liberator “About” page
Source: BleepingComputer
Targeting AnyDesk users
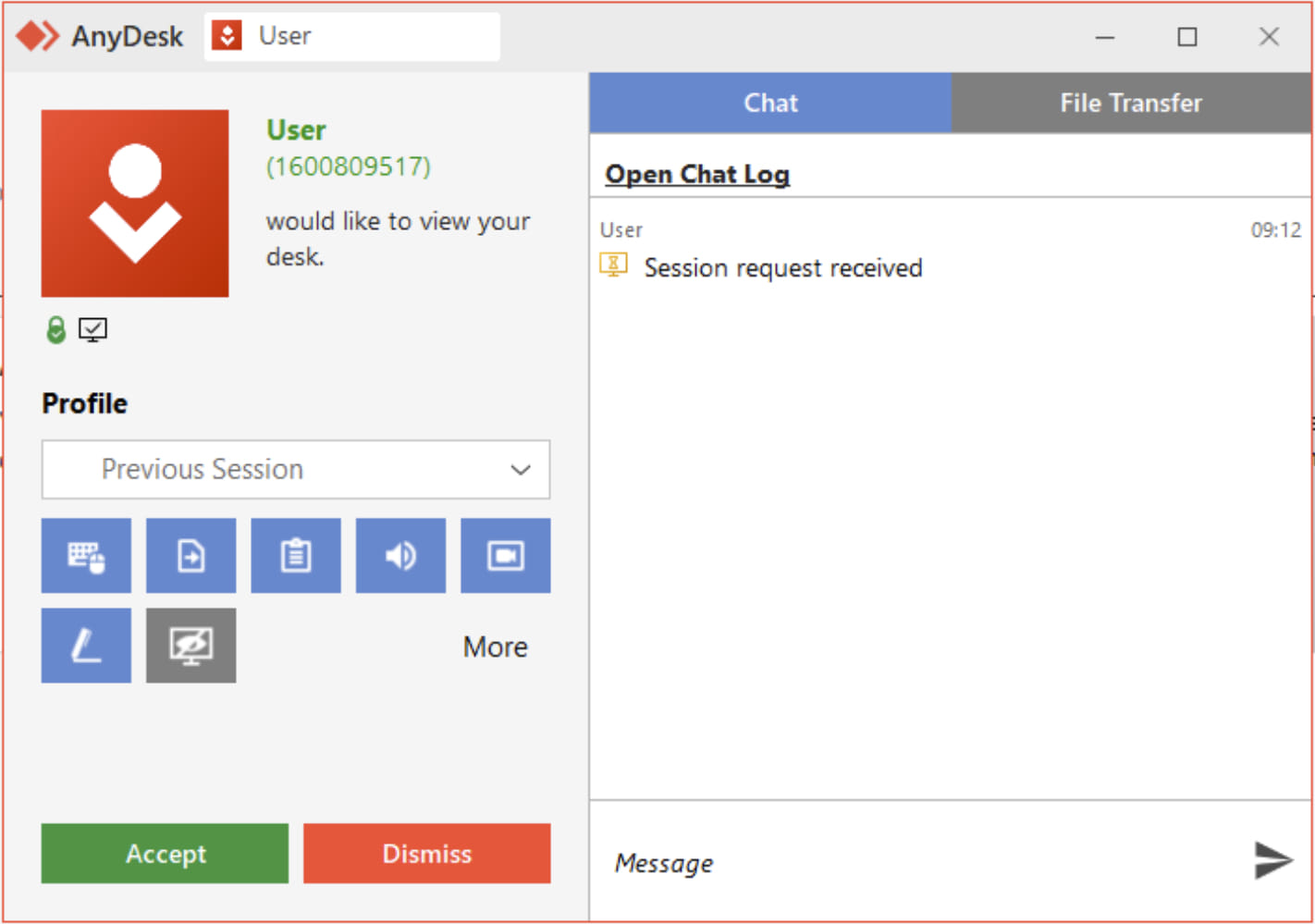
In a detailed report by cybersecurity company Sophos, researchers outline how the Mad Liberator gang begins their attacks by initiating an unsolicited connection to a computer through the AnyDesk remote access application, which is widely used by IT teams to manage corporate environments.
Although the method by which Mad Liberator selects its targets remains unclear, one theory is that the gang randomly tries AnyDesk connection IDs until a connection request is accepted. However, this theory has not been definitively proven.
Connection request on AnyDesk
Source: Sophos
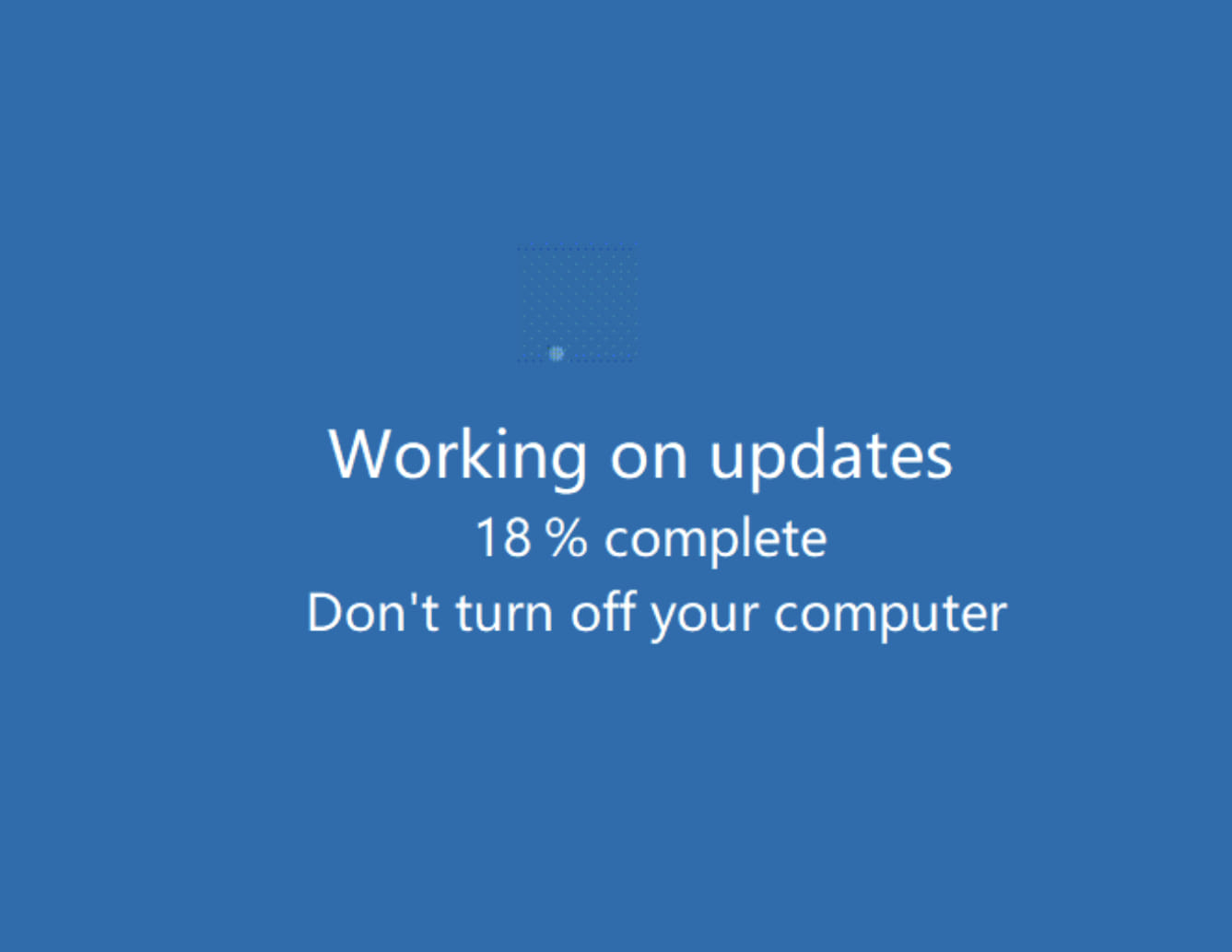
Once the connection is approved, the attackers deploy a binary named ‘Microsoft Windows Update’, which triggers a counterfeit Windows Update splash screen designed to deceive the victim.
Fake Windows update splash screen
Source: Sophos
The sole purpose of this ruse is to distract the user while the threat actors utilize AnyDesk’s File Transfer tool to exfiltrate data. The stolen data typically includes information from OneDrive accounts, network shares, and local storage.
During this staged Windows update, the victim’s keyboard is deliberately disabled to prevent any disruption to the exfiltration process.
Sophos researchers observed that, in attacks lasting approximately four hours, Mad Liberator did not encrypt any data post-exfiltration.
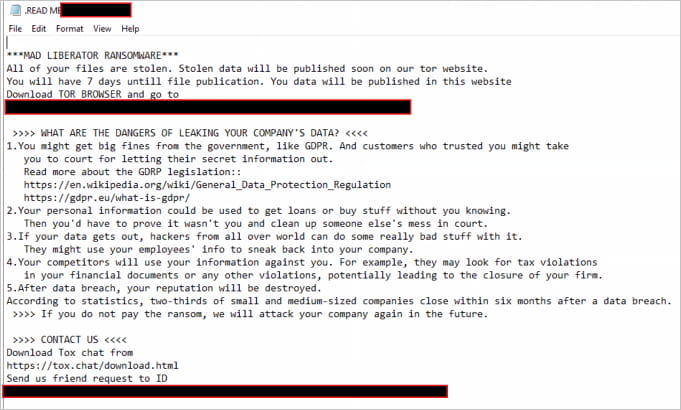
Nevertheless, the attackers left ransom notes on shared network directories, likely to ensure that their presence was noticed, especially within corporate environments.
Ransom note dropped on breached devices
Source: Sophos
The report also mentions that Sophos has found no evidence of prior interaction between the gang and their targets before the AnyDesk connection is established, and no phishing attempts were observed supporting these attacks.
Regarding Mad Liberator’s extortion tactics, the group claims on its darknet website that it contacts breached companies directly, offering to “assist” them in resolving security issues and recovering encrypted files—provided the companies meet their financial demands.
If the targeted organization does not respond within 24 hours, the gang publicly lists the company’s name on their extortion site. The victim is then given an additional seven days to reach out to the attackers.
If the company fails to comply within five days after the ultimatum is issued, Mad Liberator publishes the stolen files on their website. As of now, their leak site lists nine victimized companies.
Source: BleepingComputer