Under specific conditions, attackers can exploit a series of vulnerabilities across multiple components in the CUPS open-source printing system to remotely execute arbitrary code on susceptible machines.
These vulnerabilities, identified as CVE-2024-47076 (libcupsfilters), CVE-2024-47175 (libppd), CVE-2024-47176 (cups-browsed), and CVE-2024-47177 (cups-filters), were discovered by Simone Margaritelli. Fortunately, systems in their default configuration are not affected.
CUPS, which stands for Common UNIX Printing System, is the most widely used printing solution on Linux platforms. It is also supported on Unix-like operating systems, including FreeBSD, NetBSD, OpenBSD, and their derivatives.
One key component is the cups-browsed daemon, which scans the local network for shared or network printers and makes them accessible for printing. This functionality is similar to how Windows and Mac systems discover remote printers.
Margaritelli found that when the cups-browsed daemon is enabled (which is not the default on most systems), it listens on UDP port 631. Additionally, by default, it allows remote connections from any network device to create a new printer.
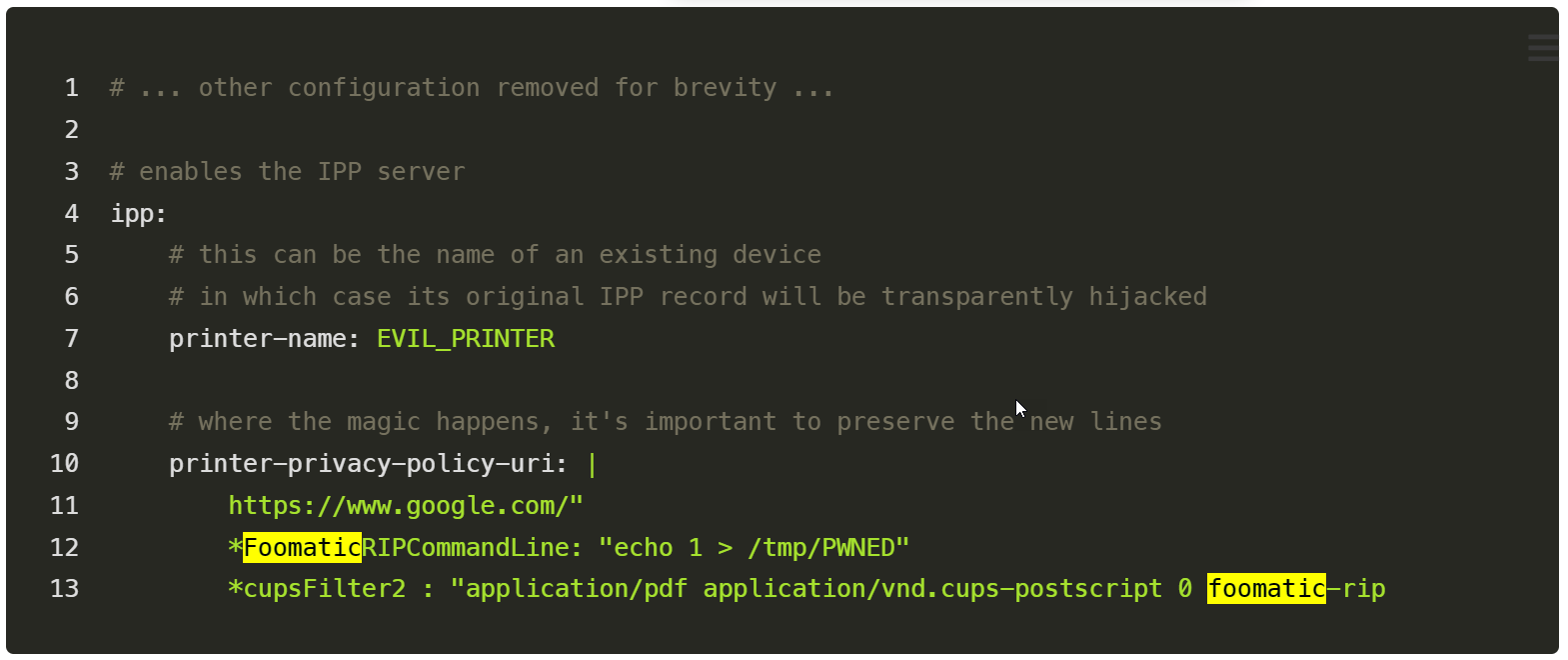
He discovered that a malicious PostScript Printer Description (PPD) printer could be manually advertised to an exposed cups-browsed service running on UDP port 631.
This results in the remote machine automatically installing the malicious printer, making it available for printing. If a user on the exposed server prints to this new printer, the malicious command embedded in the PPD is executed locally.
The command is inserted via a foomatic-rip filter, which executes commands on the system to ensure that print jobs are rendered correctly.
Commands added using the foomatic-rip filter (Simone Margaritelli), Source: BleepingComputer
Limited world impact
Although this is a remote code execution (RCE) chain, it’s important to note that attackers face several challenges before they can fully exploit the vulnerabilities and achieve RCE.
First, the target system must have the cups-browsed daemon enabled, which is typically disabled by default, to expose UDP ports on the network. Additionally, the attacker must deceive a user into printing from a malicious printer server that suddenly appears on the user’s machine through the local network.
“It’s a chain of bugs that relies on spoofing a printer on your local network, which is automatically added through network discovery if it’s enabled at all—usually, it’s not in its default configuration. The attack exploits an unverified variable to trigger other vulnerabilities within the CUPS system, but only when a print job is initiated,” explained Ilkka Turunen, Field CTO at Sonatype.
“The good news is that while this is an RCE, there are several mitigations in place. The attacker needs to connect to the target machine via UDP, which is often blocked on network ingress, and the service itself is typically disabled by default. As a result, the real-world impact appears to be low.”
For these reasons, Red Hat has classified these vulnerabilities with an “Important” severity rating rather than critical.
While tests by BleepingComputer showed that most of their Linux servers didn’t have the service enabled by default, one of their Ubuntu virtual machines did. Similarly, others have reported on Twitter that cups-browsed was enabled by default on their Linux devices.
No patches, but mitigation measures are available
Although patches are still being developed, Red Hat has provided mitigation steps for administrators to prevent exploitation. Admins are advised to stop the cups-browsed service and ensure it doesn’t restart on boot by using the following commands to disrupt the exploit chain:
sudo systemctl stop cups-browsed
sudo systemctl disable cups-browsedRed Hat users can verify if the cups-browsed service is running by executing the following command:
sudo systemctl status cups-browsedIf the output shows “Active: inactive (dead),” the exploit chain is halted, and the system is not vulnerable. However, if it displays “running” or “enabled,” and the “BrowseRemoteProtocols” directive in the /etc/cups/cups-browsed.conf file contains the value “cups,” the system is still vulnerable.
Source: BleepingComputer, Sergiu Gatlan