Threat intelligence observations show that a single threat actor drives most of the active exploitation targeting two critical vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM), tracked as CVE-2026-21962 and CVE-2026-24061.
Moreover, Ivanti flagged the security issues as actively exploited in zero-day attacks in its security advisory and, at the same time, announced hotfixes.
Both flaws carry a critical severity rating and allow attackers to inject code without authentication, which leads to remote code execution (RCE) on vulnerable systems.
GreyNoise Links Majority of Activity to Single Bulletproof IP
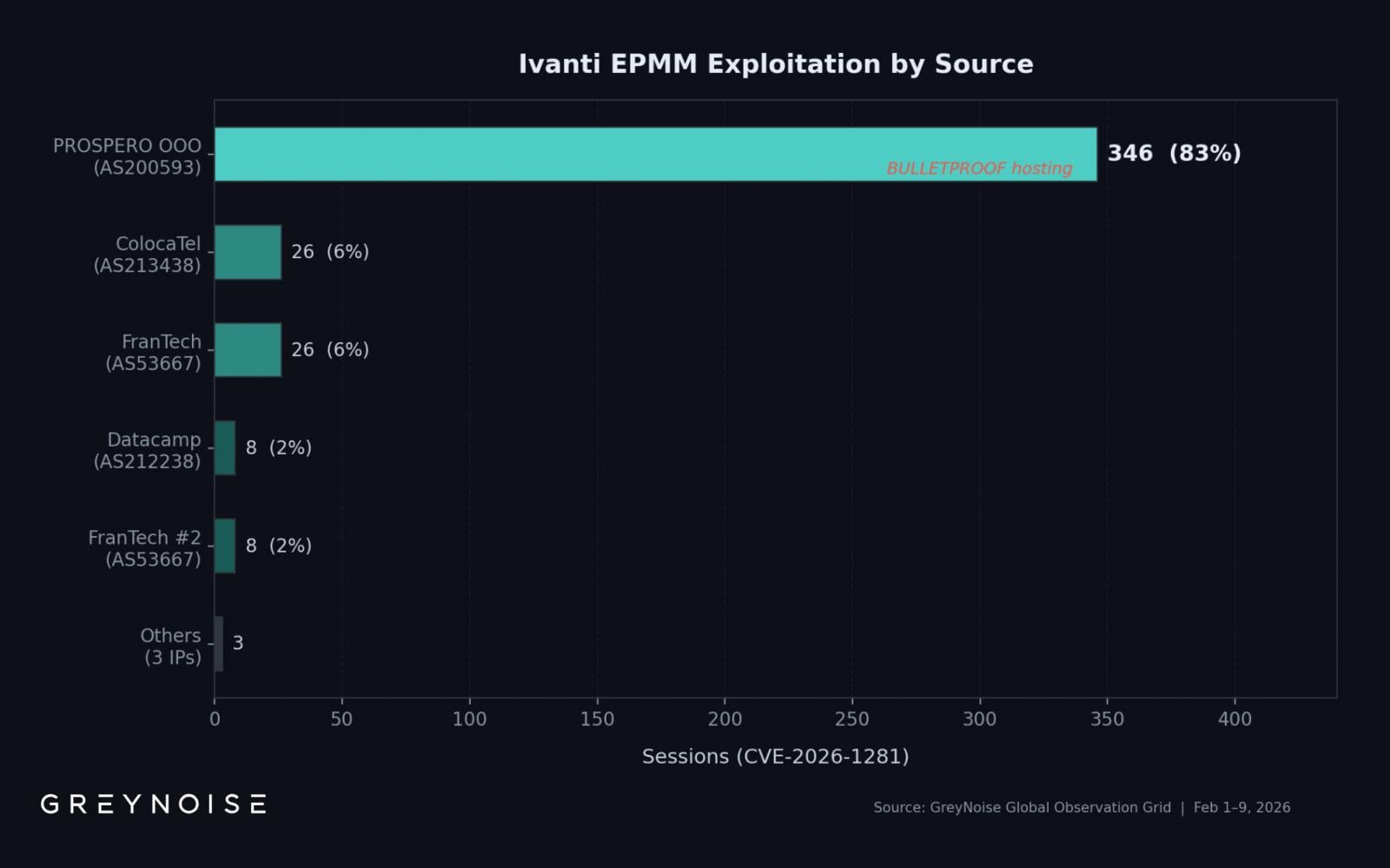
Furthermore, one IP address hosted on bulletproof infrastructure accounts for over 83% of exploitation activity related to the two vulnerabilities, according to threat-focused internet intelligence company GreyNoise.
Between February 1st and 9th, the monitoring platform recorded 417 exploitation sessions originating from eight unique source IP addresses and focused on CVE-2026-21962 and CVE-2026-24061.
Notably, 83% of the activity comes from 193[.]24[.]123[.]42, hosted by PROSPERO OOO (AS200593), which Censys analysts marked as a bulletproof autonomous system used to target various software products.
Attack source IPs
Source: GreyNoise
In addition, a sharp spike occurred on February 8, when attackers generated 269 sessions in a single day. This figure stands at nearly 13 times the daily average of 22 sessions, GreyNoise noted.
Out of the 417 exploitation sessions, 354 (85%) relied on OAST-style DNS callbacks to verify command execution capability, which points to initial access broker activity.
Interestingly, several published indicators of compromise (IoCs) list IP addresses for Windscribe VPN (185[.]212[.]171[.]0/24) that appear in GreyNoise telemetry as scanning Oracle WebLogic instances; however, researchers observed no Ivanti exploitation activity tied to those addresses.
The researchers note that the PROSPERO OOO IP address they saw “is not on widely published IOC lists, meaning defenders blocking only published indicators are likely missing the dominant exploitation source.”
Infrastructure Also Targets Oracle, Telnetd, and GLPI Flaws
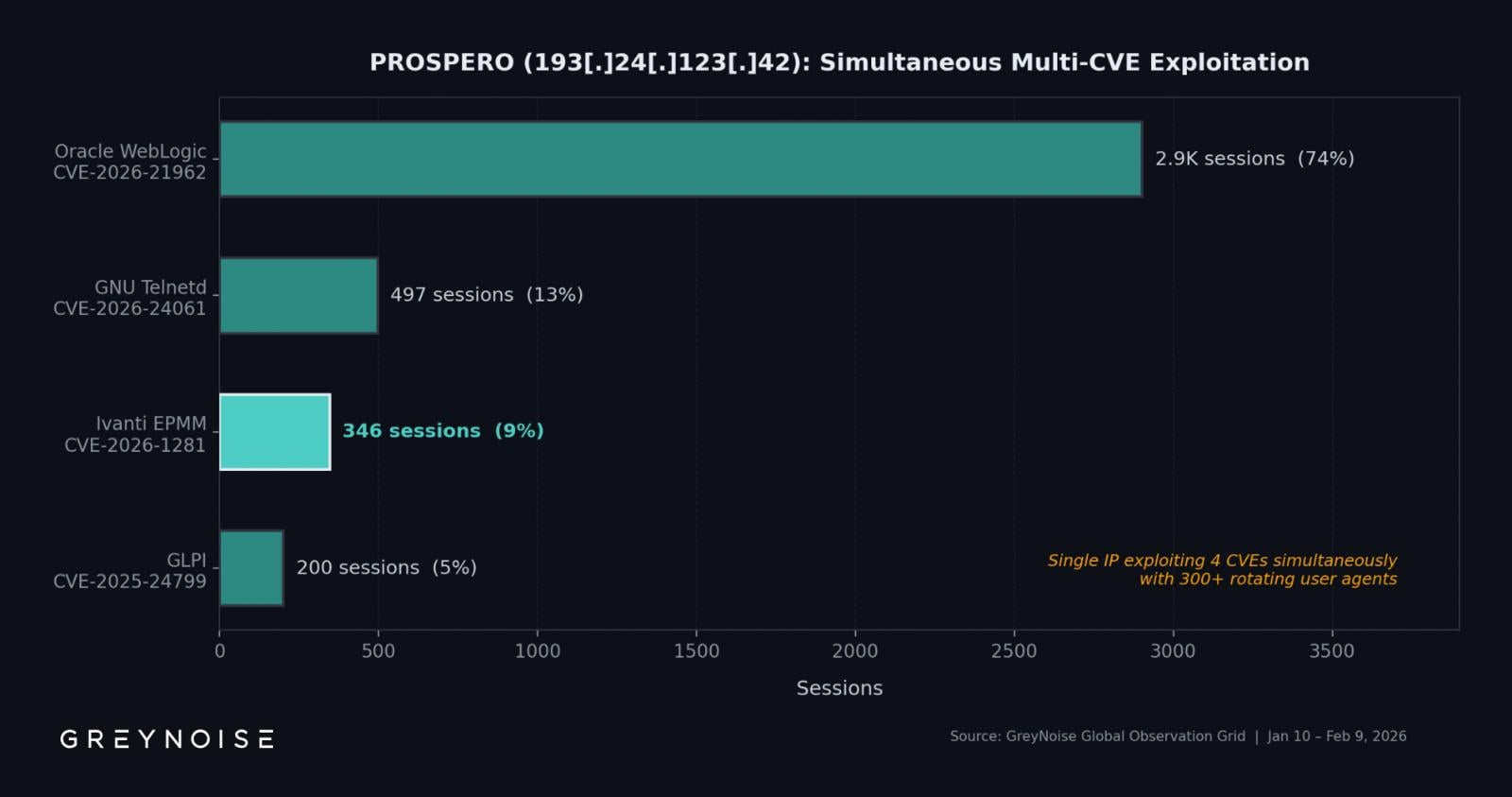
Additionally, this IP does not limit its activity to Ivanti targeting. Instead, it simultaneously exploits three more vulnerabilities: CVE-2026-21962 in Oracle WebLogic, CVE-2026-24061 in GNU Inetutils Telnetd, and CVE-2025-24799 in GLPI.
Among these, the Oracle WebLogic flaw holds the lion’s share in session volumes, dwarfing the rest with 2,902 sessions, followed by the Telnetd issue with 497 sessions.
Overall, exploitation activity appears fully automated and rotates between three hundred user agents.
Targeted vulnerabilities
Source: GreyNoise
Ivanti Mitigation Guidance and Patch Roadmap
Meanwhile, Ivanti clarified that its fixes for CVE-2026-1281 and CVE-2026-1340 do not provide a permanent solution. The company promised to release complete patches in the first quarter of this year alongside EPMM version 12.8.0.0.
Until then, Ivanti recommends using RPM packages 12.x.0.x for EPMM versions 12.5.0.x, 12.6.0.x, and 12.7.0.x, as well as RPM 12.x.1.x for EPMM versions 12.5.1.0 and 12.6.1.0.
Additionally, the vendor states that the most conservative approach involves building a replacement EPMM instance and migrating all data there. Instructions on how to complete that process are available here.
Ivanti Statement
“Ivanti’s recommendation remains the same: customers who have not yet patched should do so immediately, and then review their appliance for any signs of exploitation that may have occurred prior to patching. Applying the patch is the most effective way to prevent exploitation, regardless of how IOCs change over time, especially once a POC is available. The patch requires no downtime and takes only seconds to apply. Ivanti has provided customers with high fidelity indicators of compromise, technical analysis at disclosure, and an Exploitation Detection script developed with NCSC NL, and continues to support customers as we respond to this threat.” – Ivanti spokesperson
Source: BleepingComputer, Bill Toulas
Read more at Impreza News