Mandiant has discovered a new method that uses QR codes to bypass browser isolation technology and enable command-and-control operations.
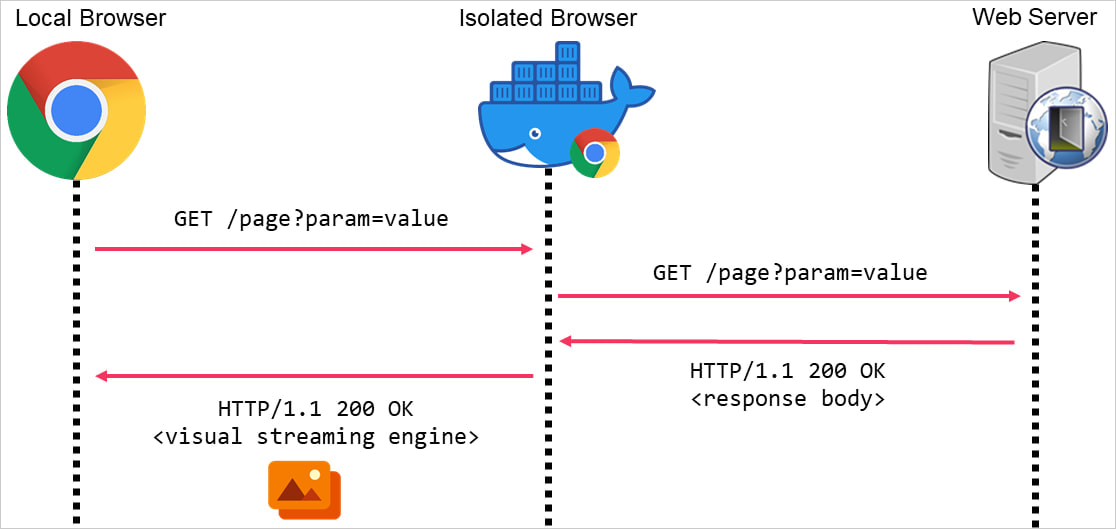
Browser isolation, a growing security technology, directs all local web browser requests through remote web browsers hosted in a cloud environment or virtual machines.
The remote browser executes any scripts or content on the visited web page, and it sends the rendered pixel stream of the page back to the local browser. This approach displays the page’s appearance while shielding the local device from malicious code.
Command-and-control servers often rely on HTTP for communication, which prompts remote browser isolation to filter the malicious traffic, rendering these communication methods ineffective.
Mandiant’s new technique bypasses these restrictions. Despite some practical limitations, it highlights the imperfections in existing browser security protections and underscores the need for “defense in depth” strategies that incorporate additional security measures.
Background on C2s and browser isolation
C2 channels facilitate malicious communications between attackers and compromised systems, allowing remote actors to control breached devices, execute commands, exfiltrate data, and more.
Browsers, designed to continuously interact with external servers, trigger isolation measures in security-critical environments to block attackers from accessing sensitive system data.
Security teams achieve this by running the browser in a separate sandboxed environment hosted on the cloud, a local virtual machine, or on-premises.
When isolation is active, the isolated browser processes incoming HTTP requests and streams only the visual content of the page to the local browser. This ensures that scripts or commands in the HTTP response never reach the target.
By preventing attackers from directly accessing HTTP responses or injecting malicious commands, isolation complicates covert C2 communications.
Overview of browser isolation
Source: Mandiant
Mandiant’s bypass trick
Mandiant researchers have developed a new technique to bypass existing isolation mechanisms in modern browsers.
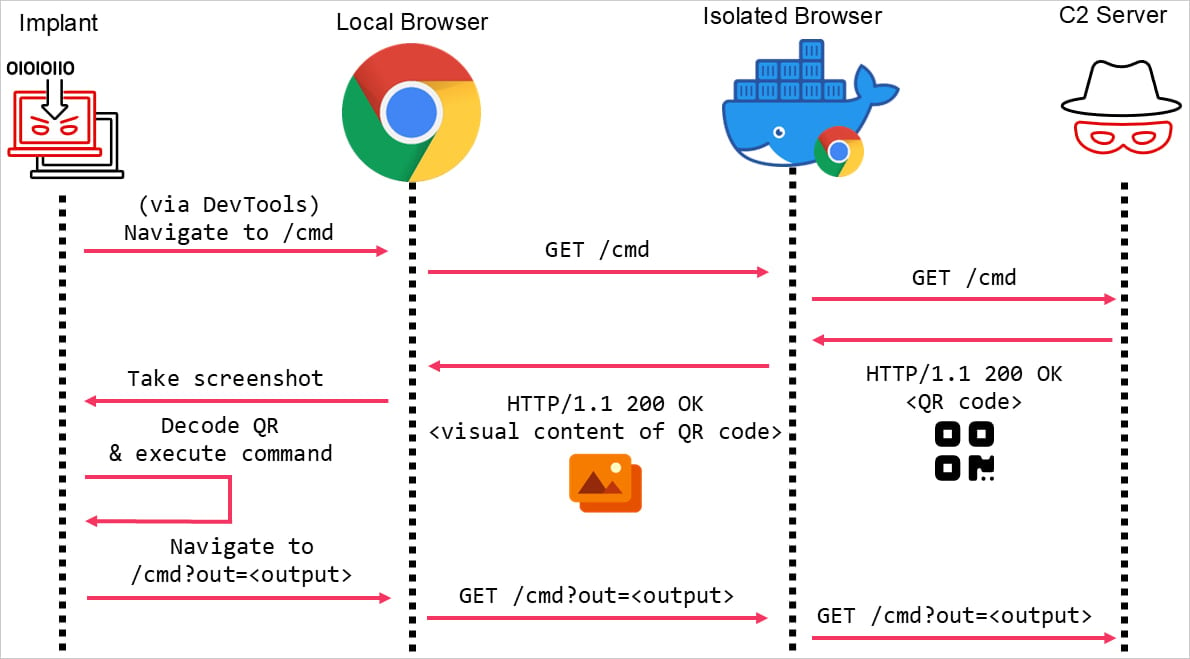
Instead of embedding commands in HTTP responses, attackers encode them in a QR code displayed visually on a webpage. Because browser isolation does not strip the visual rendering of a webpage, the QR codes reach the client that initiated the request.
In Mandiant’s study, malware controlling the “victim’s” local browser—a headless client previously infected—captures the retrieved QR code and decodes it to extract the instructions.
Bypassing browser isolation using a QR code
Source: Mandiant
Mandiant’s proof-of-concept showcases the attack on the latest Google Chrome web browser, leveraging Cobalt Strike’s External C2 feature, a widely abused pen-testing tool, to integrate the implant.
Not perfect
The PoC demonstrates that the attack is Feasible, but the technique has flaws that limit its real-world applicability.
First, the data stream is restricted to a maximum of 2,189 bytes—about 74% of the maximum capacity of QR codes. Packet sizes must shrink further if the Malware’s Interpreter encounters issues reading the QR codes.
Second, latency poses a challenge, as each request takes roughly 5 seconds. This reduces data transfer rates to around 438 bytes per second, making the technique Unsuitable for sending large payloads or Enabling SOCKS Proxying.
Finally, Mandiant acknowledges that its study did not account for additional security measures, such as domain reputation checks, URL Scanning, data loss prevention, and request heuristics, which could block or Neutralize the attack in some cases.
Despite being low bandwidth, Mandiant’s QR-code-based C2 technique remains a potential threat if left Unaddressed. Admins in critical environments are advised to monitor for abnormal traffic patterns and headless browsers running in automation mode.
Source: BleepingComputer, Bill Toulas