GitHub is currently being misused to distribute the Lumma Stealer, an information-stealing malware, through fake fixes posted in project comments.
The campaign was at first identified by a contributor to the teloxide Rust library, who reported on Reddit that they had received five comments on their GitHub issues that appeared to be fixes but were actually spreading malware.
Further investigation by BleepingComputer uncovered thousands of similar comments across various GitHub projects, all offering fake fixes in response to user questions.
The malicious comments direct users to download a password-protected archive from mediafire.com or via a bit.ly URL, with instructions to run an executable inside it. In this campaign, the password used in the comments has consistently been “changeme.”
Reverse engineer Nicholas Sherlock informed BleepingComputer that over 29,000 such comments had been posted within a 3-day period.

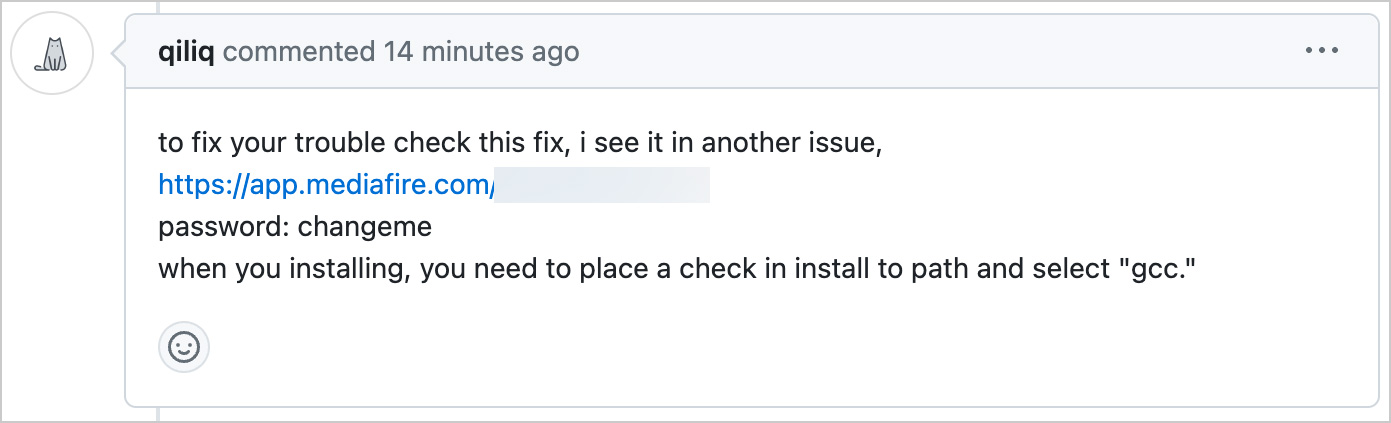
Fake answer to a GitHub issue pushing the Lumma Stealer malware
Source: Andrey Brusnik
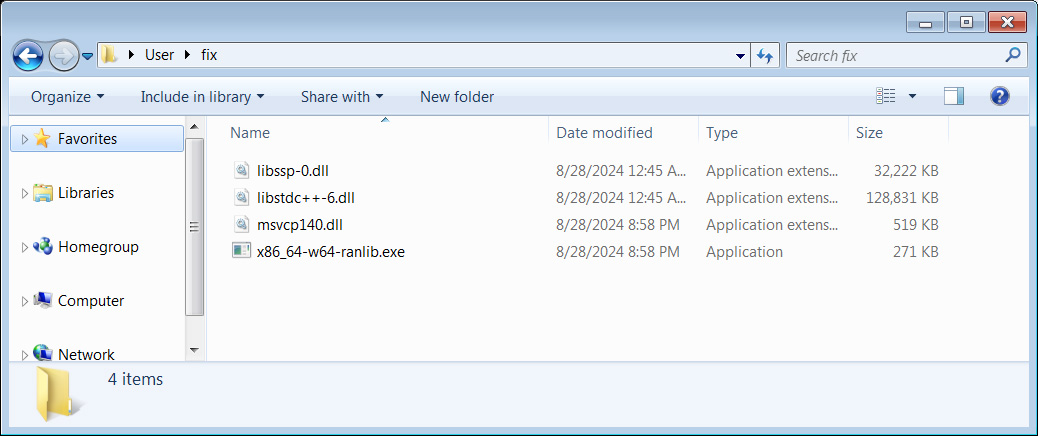
Clicking the link takes users to a download page for a file named ‘fix.zip’. Which contains several DLL files and an executable labeled x86_64-w64-ranlib.exe.
Archive containing the Lumma Stealer installer
Source: BleepingComputer
Executing this file on Any.Run reveals it to be the Lumma Stealer, an advanced info stealer that targets:
- cookies,
- credentials,
- passwords,
- credit cards,
- and browsing history from Google Chrome, Microsoft Edge, Mozilla Firefox, and other Chromium-based browsers.
Additionally, the malware can steal cryptocurrency wallets, private keys, and text files with specific names like seed.txt, pass.txt, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt, words, wallet.txt, *.txt, and *.pdf, which are likely to contain sensitive crypto keys and passwords.
The stolen data is compiled into an archive and sent to the attacker. Who can use it for further attacks or sell it on cybercrime marketplaces.
While GitHub staff have been actively removing these comments as they are discovered. Some users have already reported falling victim to the attack.
For those who have run the malware, it is crucial to change the passwords for all accounts, ensuring each site uses a unique password, and to transfer cryptocurrency to a new wallet.
Last month, Check Point Research revealed a similar campaign by the Stargazer Goblin threat actors, who leveraged over 3,000 fake GitHub accounts to distribute information-stealing malware through a Malware Distribution-as-a-Service (DaaS) model.
It remains unclear whether this is part of the same campaign or a new operation by different threat actors.
Source: BleepingComputer, Lawrence Abrams