Hackers stole the personal and contact information of nearly 1 million accounts after they breached the systems of Figure Technology Solutions, a self-described blockchain-native financial technology company.
Founded in 2018, Figure relies on the Provenance blockchain for lending, borrowing, and securities trading. To date, the company has unlocked over $22 billion in home equity and works with more than 250 partners, including banks, credit unions, fintechs, and home improvement companies.
Company Response and Initial Disclosure
However, the blockchain lender did not publicly disclose the incident. Instead, a Figure spokesperson told TechCrunch on Friday that the attackers stole “a limited number of files” in a social engineering attack.
Meanwhile, BleepingComputer also reached out to Figure with further questions about the breach, but the company did not immediately provide a response.
Although the company has yet to share how many individuals the data breach affected, notification service Have I Been Pwned has now revealed the extent of the incident, reporting that attackers stole data from 967,200 accounts.
“In February 2026, data obtained from the fintech lending platform Figure was publicly posted online,” Have I Been Pwned said on Wednesday.
“The exposed data, dating back to January 2026, contained over 900k unique email addresses along with names, phone numbers, physical addresses and dates of birth. Figure confirmed the incident and attributed it to a social engineering attack in which an employee was tricked into providing access.”
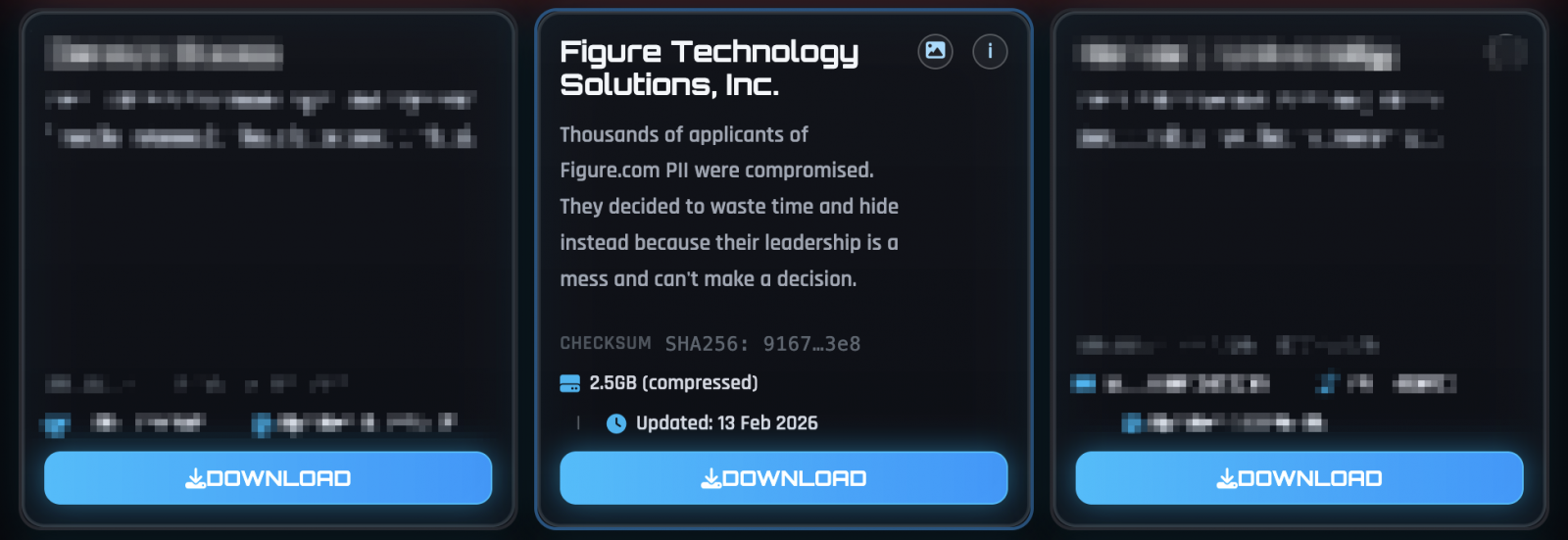
Furthermore, the ShinyHunters extortion group claimed responsibility for the breach and added the company to its dark web leak site, leaking 2.5GB of data allegedly stolen from thousands of loan applicants.
CaptionFigure Technology on ShinyHunters leak site
Source:: BleepingComputer
In recent weeks, ShinyHunters claimed similar breaches at Canada Goose, Panera Bread, Betterment, SoundCloud, PornHub, and CrowdStrike.
Broader Vishing Campaign Targets Major Platforms
While not all of these incidents belong to the same campaign, attackers breached some of these organizations in a voice phishing (vishing) campaign that targeted single sign-on (SSO) accounts at Okta, Microsoft, and Google across more than 100 high-profile organizations.
Specifically, the attackers impersonate IT support, call targeted employees, and trick them into entering credentials and multi-factor authentication (MFA) codes on phishing sites that impersonate their companies’ login portals.
Once inside, the attackers access the victims’ SSO accounts, which then give them entry to connected enterprise applications and services, including Salesforce, Microsoft 365, Google Workspace, SAP, Slack, Zendesk, Dropbox, Adobe, Atlassian, and many others.
As part of this campaign, ShinyHunters also breached online dating giant Match Group, which owns multiple popular dating services, including Tinder, Hinge, Meetic, Match.com, and OkCupid.
Source: BleepingComputer, Sergiu Gatlan
Read more at Impreza News