Two malware developed with a focus on nuclear, military and electoral espionage were discovered collecting WhatsApp conversations, army and government representatives in Pakistan and Kashmir, territory in northern India, which has suffered from territorial disputes for decades.
Malware, dubbed Hornbill and SunBird, was identified by Lookout, a North American information security company, camouflaged in various applications – apparently naive – available on Android app stores, APK Pure, APK Combo and APK Support.
According to the researchers, there is evidence that malware has been developed by cybercriminals in favor of the Indian government and army, specifically to compromise WhatsApp conversations from Pakistani and Kashmir officials.
“We believe with great confidence that these surveillance tools are used by the Advanced Persistent Threat (APT) group, Confucius, which first appeared in 2013 as a state sponsored pro-India actor, mainly chasing Pakistan and other South Asian targets, ”write Lookout researchers.
The researchers explain that the main target of Hornbill and SunBird are Pakistani military, nuclear authorities and electoral authorities in Kashmir. Malware mainly collects conversation records with images, files and audios; contacts and metadata (phone number, IMEI, Android ID, model, manufacturer, and operating system version). Both malware are capable of film the screens of the victims’ smartphones, in addition to accessing the cameras (both front and rear), in addition to extracting complete conversation records.
Traditional malware
Lookout named Hornbill’s first malware, in honor of a common bird in Chandigar, an Indian state where researchers believe it has been developed. SunBird, also Indian, has this name because it is based on traditional malware, the SunService.
The malware Hornbill is based on was first found in January 2018. The SunBird antessessor, in January 2017. “We are confident that SunBird and Hornbill are two tools used by the same actor, perhaps for different surveillance purposes,” they write.
“Hornbill and SunBird have similarities and differences in the way they operate on an infected device […] Although SunBird has remote access trojan (RAT) functionality, Hornbill is a discrete surveillance tool used to extract a selected set of data of interest to its operator”Says Apurva Kumar, security intelligence engineer and Kristin Del Rosso, security intelligence researcher at Lookout.
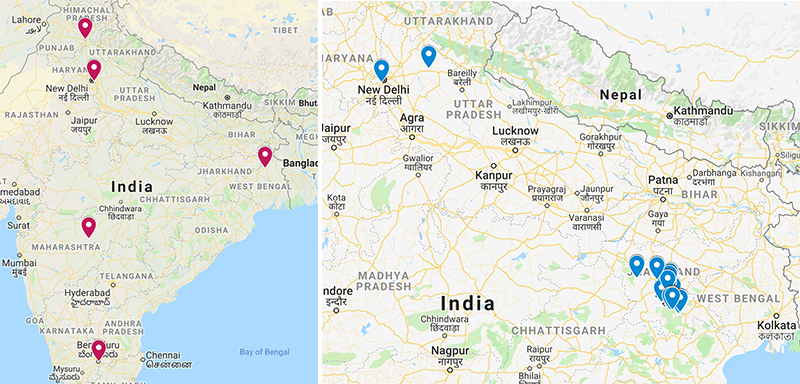
According to the researchers, there is no way to identify how many people were infected in total. But in 2019 alone, at least 156 people were infected with SunBird. However, although it was developed with a focus on Pakistan and Kashmir, users of “at least 14 different countries ”were also infected.
Source: Look out.
See the original post at: https://thehack.com.br/dois-malwares-estatais-foram-descobertos-espionando-mensagens-de-whatsapp-de-autoridades-no-paquistao/?rand=48873





















