Threat actors associated with the “Scattered Lapsus$ Hunters” (SLH) claim they breached the systems of cybersecurity firm Resecurity and stole internal data. However, Resecurity counters these claims, stating the attackers only accessed a deliberately deployed honeypot containing fake information used to monitor their activity.
Earlier today, the threat actors escalated their claims by publishing screenshots on Telegram that allegedly show evidence of the breach. They assert they stole employee data, internal communications, threat intelligence reports, and client information.
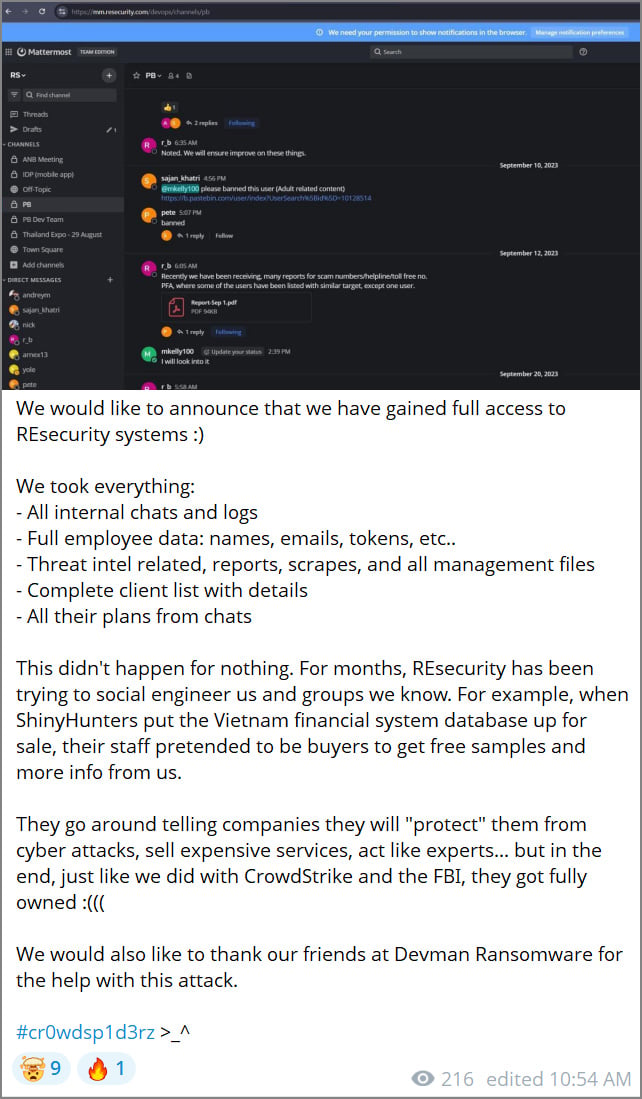
“We would like to announce that we have gained full access to REsecurity systems,” the group wrote on Telegram. They further claimed to have stolen “all internal chats and logs,” “full employee data,” “threat intel related reports,” and a “complete client list with details.”
Portion of the Telegram post by the threat actors
Source: BleepingComputer
To support their claims, the threat actors shared screenshots they allege came from Resecurity’s internal systems. These images include what appears to be a Mattermost collaboration instance displaying communications between Resecurity employees and Pastebin personnel related to malicious content hosted on the text-sharing platform.
Motive Framed as Retaliation
Meanwhile, the threat actors explained that they operate under the name “Scattered Lapsus$ Hunters” due to the alleged overlap between ShinyHunters, Lapsus$, and Scattered Spider threat actors. According to the group, they launched the attack in retaliation for what they describe as ongoing attempts by Resecurity to socially engineer them and gather intelligence on their operations.
Specifically, the threat actors claim that Resecurity employees posed as buyers during the sale of an alleged Vietnam financial system database and attempted to obtain free samples and additional information.
After publication of this article, a ShinyHunters spokesperson told BleepingComputer that the group did not participate in this activity. While ShinyHunters has consistently claimed affiliation with Scattered Lapsus$ Hunters, the spokesperson stated they played no role in this alleged attack.
If you have any information regarding this incident or other undisclosed attacks, you can contact us confidentially via Signal at 646-961-3731 or by email at [email protected].
Resecurity Says Attackers Fell Into a Honeypot
In response, Resecurity firmly disputes the threat actors’ claims. The company states that the allegedly breached systems do not belong to its production infrastructure but instead form part of a honeypot environment designed to attract and monitor malicious actors.
After BleepingComputer contacted Resecurity regarding the claims, the company shared a report published on December 24. According to the report, Resecurity first detected a threat actor probing its publicly exposed systems on November 21, 2025.
DFIR Investigation and Honeypot Deployment
Resecurity says its DFIR team quickly identified early reconnaissance indicators and logged multiple IP addresses associated with the activity, including addresses originating from Egypt and Mullvad VPN services.
In response, the company deployed a honeypot account inside an isolated environment. This setup allowed the threat actor to authenticate and interact with systems populated with fake employee, customer, and payment data, all while Resecurity researchers actively monitored the activity.
A honeypot is a deliberately exposed and closely monitored system or account designed to lure attackers. It enables defenders to observe and analyze malicious behavior while protecting real data and infrastructure.
According to Resecurity, the company filled the honeypot with synthetic datasets designed to closely mirror real business data. These datasets included more than 28,000 synthetic consumer records and over 190,000 synthetic payment transaction records generated using Stripe’s official API format.
In December, the threat actor reportedly began attempting to automate data exfiltration. Between December 12 and December 24, the actor generated more than 188,000 requests while rotating through large numbers of residential proxy IP addresses.
During this period, Resecurity says it collected extensive telemetry on the attacker’s tactics, techniques, and supporting infrastructure.
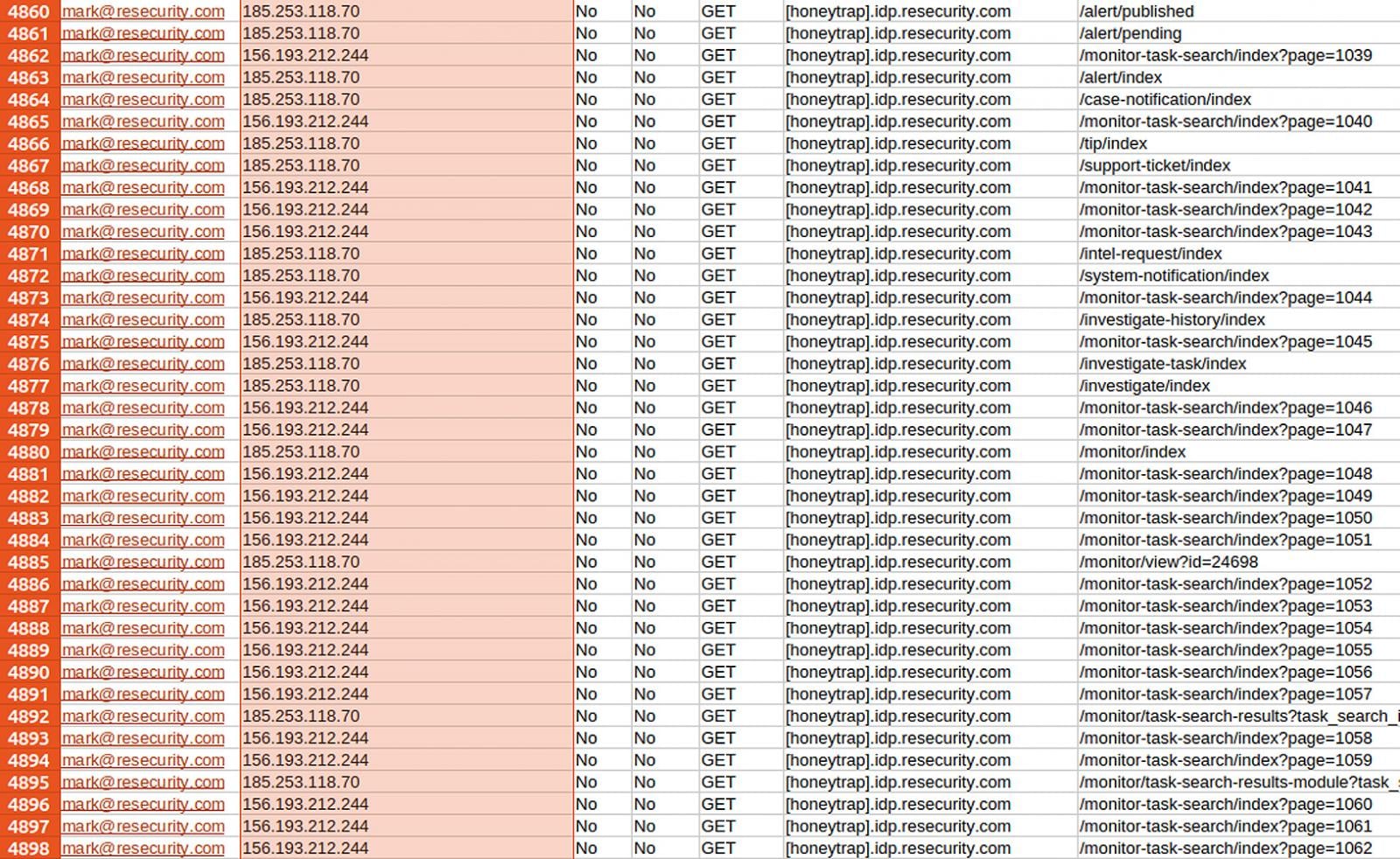
Resecurity monitoring activity on honeypot
Source: Resecurity
Law Enforcement Notification and OPSEC Failures
Resecurity claims the attacker briefly exposed confirmed IP addresses on multiple occasions due to residential proxy connection failures. The company says it shared this intelligence with law enforcement.
After detecting additional activity, Resecurity added more fake datasets to the honeypot to further study the attacker’s behavior. This move reportedly triggered further operational security failures and helped narrow down the attacker’s infrastructure.
The firm later identified servers used to automate the attack through residential proxies and again shared the findings with law enforcement.
“Once the actor was located using available network intelligence and timestamps, a foreign law enforcement organization, a partner of Resecurity, issued a subpoena request regarding the threat actor,” Resecurity stated.
At the time of writing, the threat actors have not released additional evidence. Instead, they published a new Telegram post suggesting further disclosures may follow.
“Nice damage control Resecurity. More information coming soon!,” the post reads.
Source: BleepingComputer, Lawrence Abrams
Read more at Impreza News