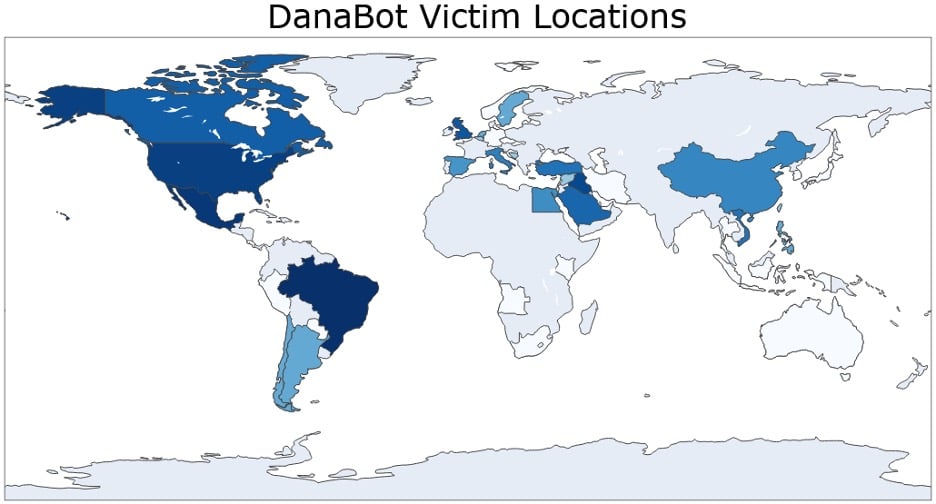
In the latest phase of Operation Endgame, an international law enforcement operation, national authorities from seven countries seized 300 servers and 650 domains that cybercriminals had been using to launch ransomware attacks.
According to the joint action’s official website, “From 19 to 22 May, authorities took down approximately 300 servers worldwide, neutralized 650 domains, and issued international arrest warrants for 20 targets, delivering a direct blow to the ransomware kill chain.”
Moreover, authorities seized EUR 3.5 million in cryptocurrency during the action week, raising the total amount confiscated during Operation Endgame to EUR 21.2 million.
Working in collaboration with private sector partners, authorities coordinated by Europol and Eurojust targeted several cybercrime operations, including Bumblebee, Lactrodectus, Qakbot, DanaBot, Trickbot, and Warmcookie.
These malware strains often serve as tools for other cybercriminals, enabling them to gain access to the networks of victims who are later targeted in ransomware attacks.
Europol Executive Director Catherine De Bolle added, “This new phase demonstrates law enforcement’s ability to adapt and strike again, even as cybercriminals retool and reorganize. By disrupting the services criminals rely on to deploy ransomware, we break the kill chain at its source.”
DanaBot charges
On Thursday, the U.S. Department of Justice unsealed charges against 16 defendants who allegedly belong to a Russian cybercrime gang that operated the DanaBot malware scheme.
The U.S. authorities identified eight of the 16 indicted Russian nationals — Aleksandr Stepanov, Artem Aleksandrovich Kalinkin, Danil Khalitov, Aleksey Efremov, Kamil Sztugulewski, Ibrahim Idowu, Artem Shubin, and Aleksey Khudiakov — while referring to the remaining eight by their pseudonyms.
According to a complaint, the defendants used the botnet to deploy additional malware payloads, including ransomware. Collectively, they infected over 300,000 computers across the globe and caused damages that exceed $50 million.
DanaBot malware, active since 2018, operates under a malware-as-a-service model. This setup allows administrators to lease access to their botnet and associated support tools for thousands of dollars per month. Furthermore, the malware can hijack banking sessions, steal data and browsing histories, and grant full remote access to compromised systems — enabling keystroke logging and video recording of user activities.
Additionally, DanaBot’s administrators have employed a second version of the botnet for cyberespionage. This version targets military, diplomatic, and government organizations.
“The botnet’s alternate version recorded all interactions with the infected computer and sent the stolen data to a different server than the fraud-focused variant of DanaBot,” the Justice Department noted. “This version was allegedly used to target diplomats, law enforcement personnel, and military members in North America and Europe.”
Image: Lumen
Previous Operation Endgame actions
This week’s action builds on several previous phases of Operation Endgame, including the seizure of more than 100 servers that hosted over 2,000 domains used by various malware loader operations, such as IcedID, Pikabot, Trickbot, Bumblebee, Smokeloader, and SystemBC.
Following that, in June 2024, law enforcement agents arrested a crypter specialist linked to the Conti and LockBit ransomware gangs. This individual helped the malware evade detection by antivirus software.
Earlier, in April, police tracked down customers of the Smokeloader botnet and detained at least five individuals. These arrests were made possible through intelligence gathered after authorities seized a database containing details of cybercriminals who had paid for Smokeloader subscriptions.
This week as well, U.S. authorities indicted Russian national Rustam Rafailevich Gallyamov, the leader of the Qakbot malware operation. His campaign compromised more than 700,000 computers and enabled numerous ransomware attacks.
Moreover, Microsoft and its partners seized approximately 2,300 domains earlier this month during a takedown operation targeting the Lumma malware-as-a-service (MaaS) information stealer campaign.
Source: BleepingComputer, Sergiu Gatlan
Read more at Impreza News