Homebrew, LogMeIn and TradingView are targets
A new malicious campaign targets macOS developers with fake Homebrew, LogMeIn, and TradingView platforms that deliver infostealing malware like AMOS (Atomic macOS Stealer) and Odyssey.
Moreover, the campaign employs “ClickFix” techniques where attackers trick targets into executing commands in Terminal, thereby causing them to infect themselves with malware.
Homebrew remains a popular open-source package management system that makes it easier to install software on macOS and Linux. Furthermore, threat actors have used the platform’s name in the past to distribute AMOS in malvertising campaigns.
LogMeIn serves as a remote access service, and TradingView provides financial charting and market analysis tools; both platforms remain widely used by Apple users.
Researchers at threat hunting company Hunt.io identified more than 85 domains impersonating the three platforms in this campaign, including the following:
| http://homebrewclubs.org/ | https://sites-phantom.com/ |
| http://homebrewfaq.org/ | https://tradingviewen.com/ |
| http://homebrewlub.us/ | https://tradingvieweu.com/ |
| http://homebrewonline.org/ | https://www.homebrewclubs.org/ |
| http://homebrewupdate.org/ | https://www.homebrewfaq.org/ |
| http://sites-phantom.com/ | https://www.homebrewfaq.us/ |
| http://tradingviewen.com/ | https://www.homebrewonline.org/ |
| http://tradingvieweu.com/ | https://www.homebrewupdate.org/ |
| http://www.homebrewfaq.us/ | https://www.tradingvieweu.com/ |
| http://www.homebrewonline.org/ | https://filmoraus.com/ |
| http://www.tradingviewen.com/ | https://homebrewfaq.org/ |
| https://filmoraus.com/ | https://homebrewfaq.us/ |
| https://homebrewfaq.org/ | https://homebrewlub.us/ |
When researchers checked some of the domains, BleepingComputer found that Google Ads drove traffic to the sites in certain cases, which indicates that the threat actor promoted them to appear in Google Search results.
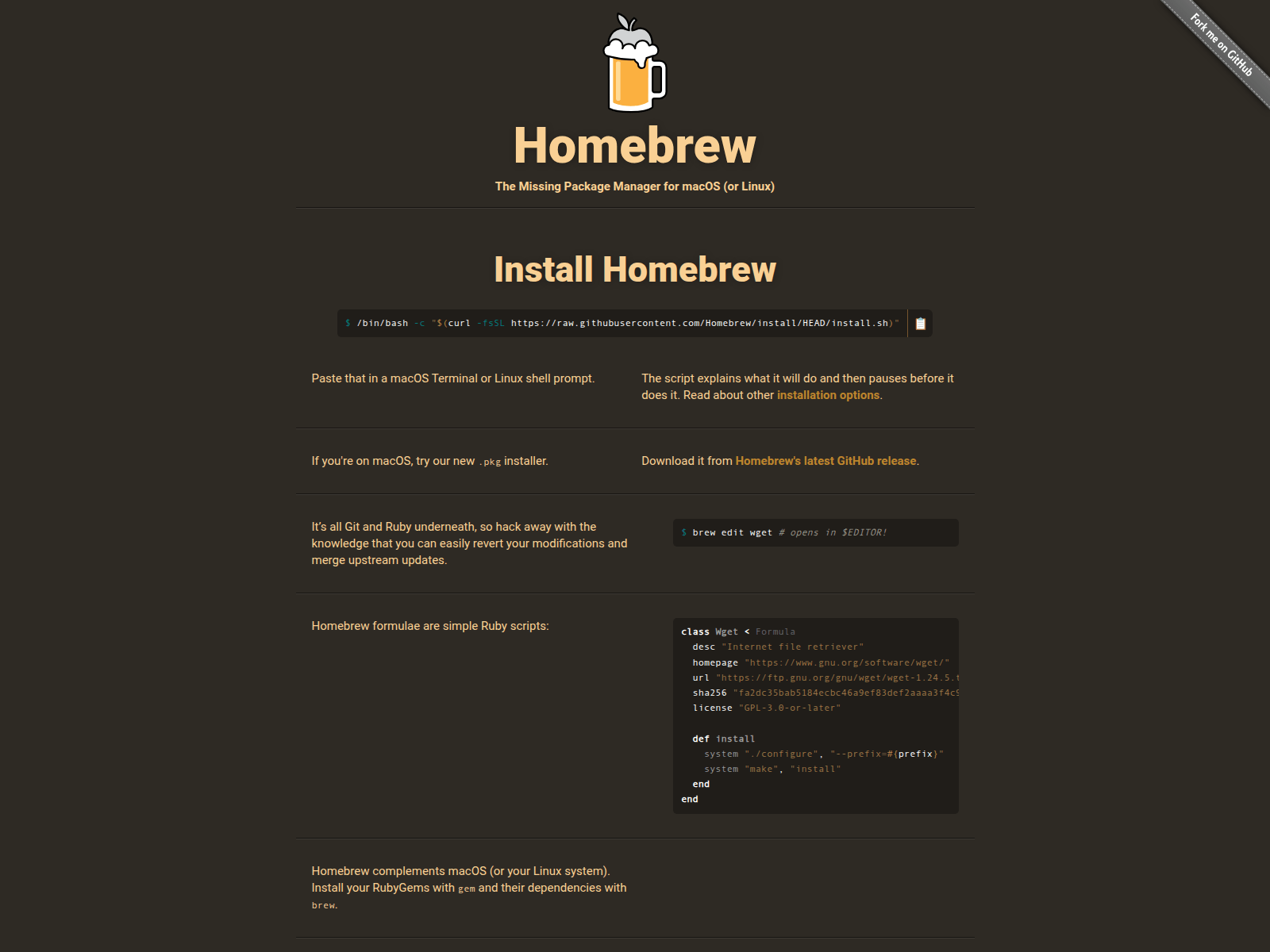
The malicious sites feature convincing download portals for the fake apps and instruct users to copy a curl command in their Terminal to install them, the researchers say.
Homebrew-themed ClickFix page
Source: Hunt.io
Just one click
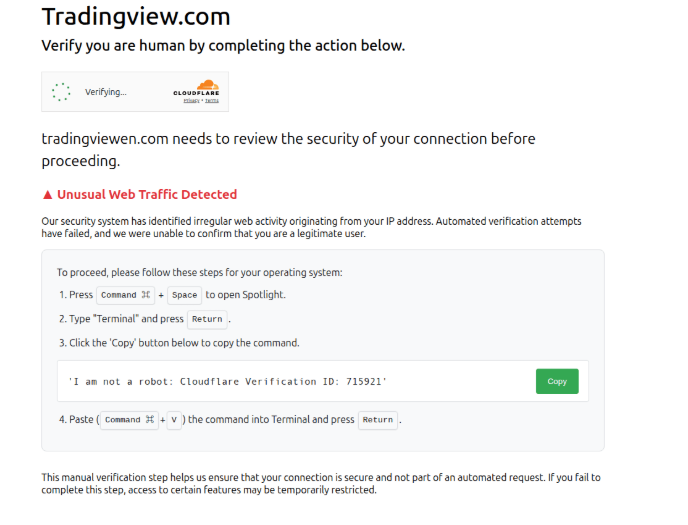
In other cases, like for TradingView, the threat actors present the malicious commands as a “connection security confirmation step.” However, if the user clicks on the ‘copy’ button, the site delivers a base64-encoded installation command to the clipboard instead of the displayed Cloudflare verification ID. Then the commands fetch and decode an ‘install.sh’ file, which downloads a payload binary, removes quarantine flags, and bypasses Gatekeeper prompts to allow its execution.
Fake TradingView page
Source: Hunt.io
Consequently, the payload contains either AMOS or Odyssey; the malware executes on the machine only after it checks whether the environment runs in a virtual machine or on an analysis system.
The malware explicitly invokes sudo to run commands as root, and its first action collects detailed hardware and memory information from the host.
Next, it manipulates system services, for example killing OneDrive updater daemons, and it interacts with macOS XPC services to blend its malicious activity with legitimate processes.
Eventually, the malware activates its information-stealing components, which harvest sensitive information stored in browsers, steal cryptocurrency credentials, and then exfiltrate the data to the command and control (C2).
AMOS malware
AMOS, which researchers first documented in April 2023, operates as a malware-as-a-service (MaaS) available under a $1,000/month subscription. It can steal a broad range of data from infected hosts.
Recently, the creators added a backdoor component to the malware to give operators remote persistent access capabilities.
Odyssey Stealer, which CYFIRMA researchers documented this summer, represents a relatively new family that developers derived from the Poseidon Stealer, and developers forked Poseidon from AMOS.
It targets credentials and cookies stored in Chrome, Firefox, and Safari browsers, more than a hundred cryptocurrency wallet extensions, Keychain data, and personal files, and it sends those items to the attackers in ZIP format.
Finally, security experts strongly recommend that users not paste Terminal commands they find online unless they fully understand what those commands do.
Source: BleepingComputer, Bill Toulas
Read more at Impreza News