FileFlix and Interlock Ransomware
Hackers recently adopted a new technique called ‘FileFix‘ in Interlock ransomware attacks, using it to drop a remote access trojan (RAT) on targeted systems.
Meanwhile, Interlock ransomware operations have surged over the past months, as the threat actor began using the KongTuke web injector (also known as ‘LandUpdate808‘) to deliver payloads through compromised websites.
Since May, researchers at The DFIR Report and Proofpoint have observed this shift in modus operandi. At that time, attackers prompted visitors to compromised sites to pass a fake CAPTCHA and verification step. Then, they had to paste content—automatically saved to the clipboard—into a Run dialog, a tactic that aligned with ClickFix attacks.
As a result, users executed a PowerShell script that retrieved and launched a Node.js-based variant of the Interlock RAT.
By June, researchers discovered a PHP-based variant of Interlock RAT in the wild, which the attackers delivered using the same KongTuke injector.
Then, earlier this month, the attacker introduced a significant change to the delivery wrapper. Interlock now uses the FileFix variation of the ClickFix method as its preferred delivery technique.
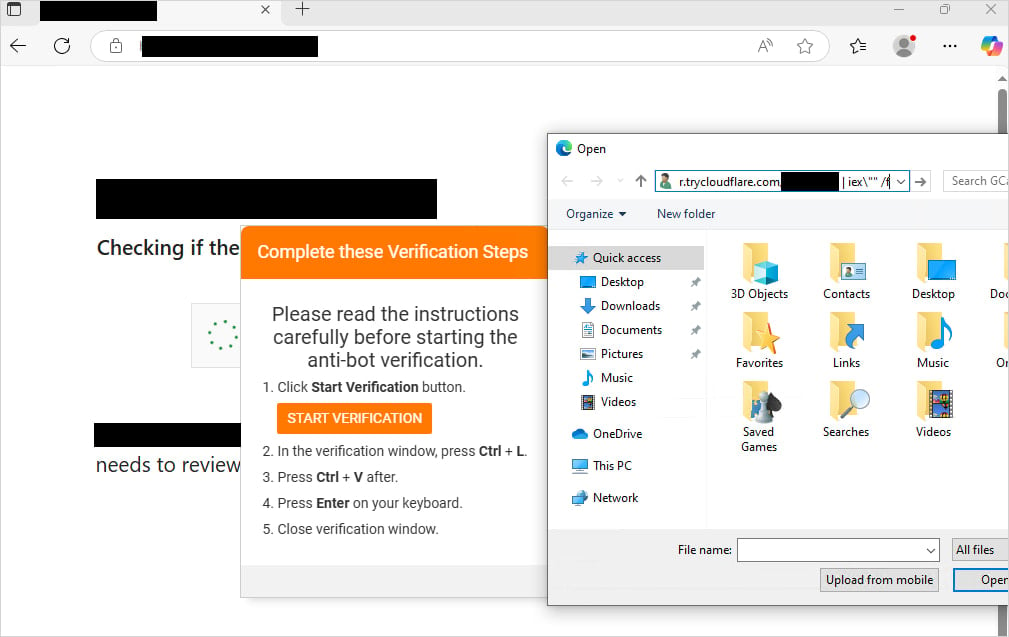
Interlock’s FileFix attack
Source: The DFIR Report
FileFlix and ClickFix
FileFix, developed by security researcher mr.d0x, represents a social engineering attack technique and an evolution of ClickFix, one of the most commonly used payload distribution methods over the past year.
In this FileFix variation, the attacker weaponizes trusted Windows UI elements—such as File Explorer and HTML Applications (.HTA)—to trick users into executing malicious PowerShell or JavaScript code, all without triggering security warnings.
Specifically, users are prompted to “open a file” by pasting a copied string into File Explorer’s address bar. This string appears as a file path due to comment syntax but functions as a disguised PowerShell command.
In the latest Interlock attacks, targets receive instructions to paste this disguised command into File Explorer. Consequently, the system downloads the PHP RAT from ‘trycloudflare.com’ and executes it.
After infection, the RAT runs a series of PowerShell commands to collect system and network information, then exfiltrates the data as structured JSON to the attacker.
Additionally, The DFIR Report notes signs of interactive attacker behavior, such as Active Directory enumeration, backup checks, local directory navigation, and domain controller inspection.
Moreover, the command and control (C2) server can issue shell commands for the RAT to execute, deploy new payloads, establish persistence via a Registry run key, or move laterally through remote desktop (RDP).
Launched in September 2024, Interlock ransomware has claimed several high-profile victims, including Texas Tech University, DaVita, and Kettering Health.
Initially, the ransomware operation relied on ClickFix to infect targets. However, the shift to FileFix demonstrates the attacker’s ability to adapt quickly to stealthier tactics.
This incident marks the first public confirmation of FileFix being used in real-world cyberattacks. Consequently, the technique is likely to gain traction as more threat actors seek to incorporate it into their attack chains.
Source: BleepingComputer, Bill Toulas
Read more at Impreza News