Hackers are increasingly targeting Windows machines by using ZIP file concatenation to embed malicious payloads within compressed archives, slipping past security defenses undetected.
This method takes advantage of the variations in how ZIP parsers and archive managers process concatenated ZIP files.
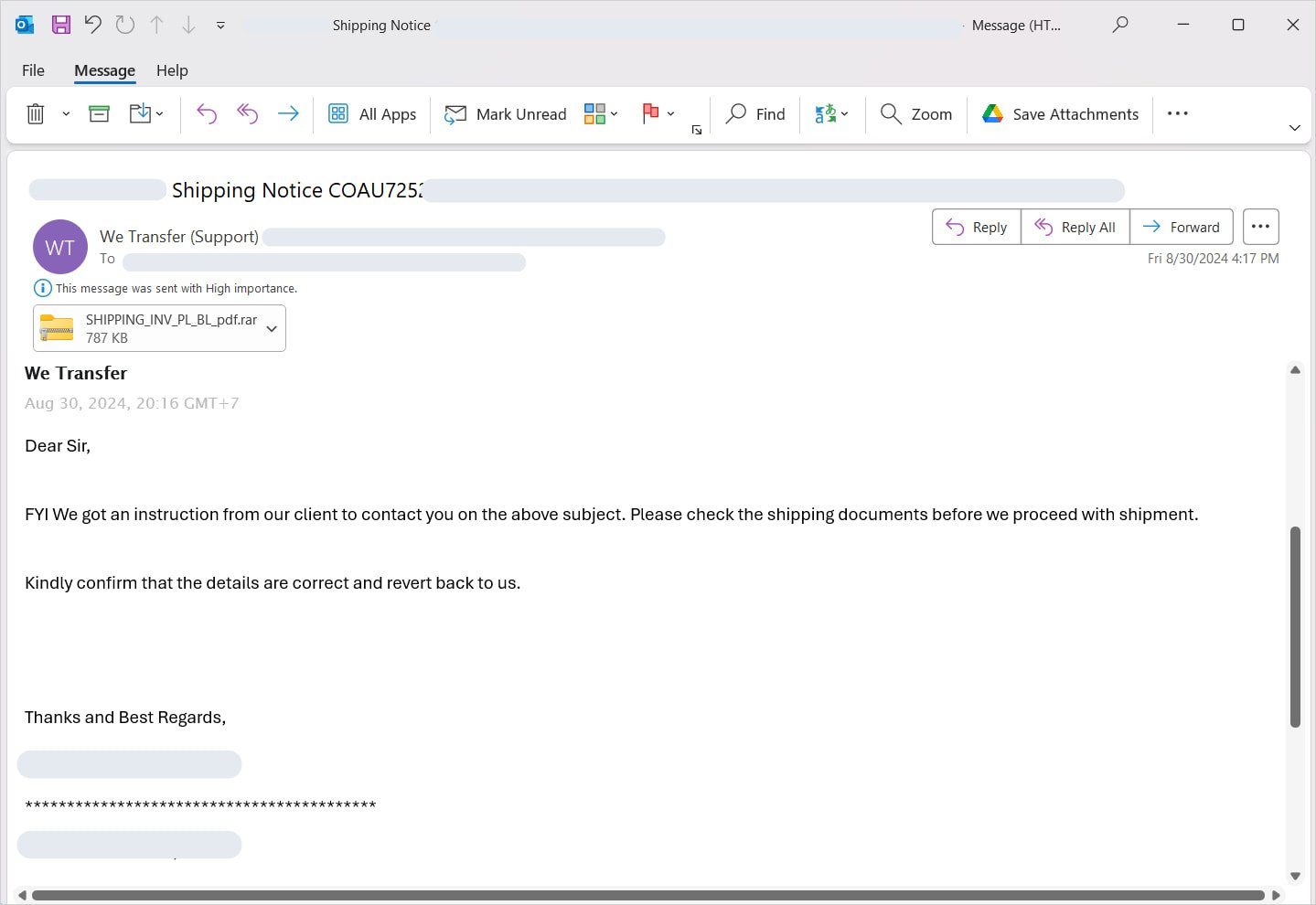
Perception Point researchers recently uncovered this tactic while analyzing a phishing attack disguised as a shipping notice. Within the concatenated ZIP archive, they found a hidden trojan.
The malware, masquerading as a RAR archive attachment, employed the AutoIt scripting language to automate harmful actions on the victim’s system.
Phishing email hiding a trojan in a concatenated ZIP file
Source: Perception Point
Hiding malware in “broken” ZIPs
The initial phase of the attack involves preparation, during which threat actors create multiple ZIP archives, concealing the malicious payload within one and leaving the others harmless.
Afterward, they concatenate these files by appending the binary data of one archive to another, effectively merging their contents into a single ZIP file.
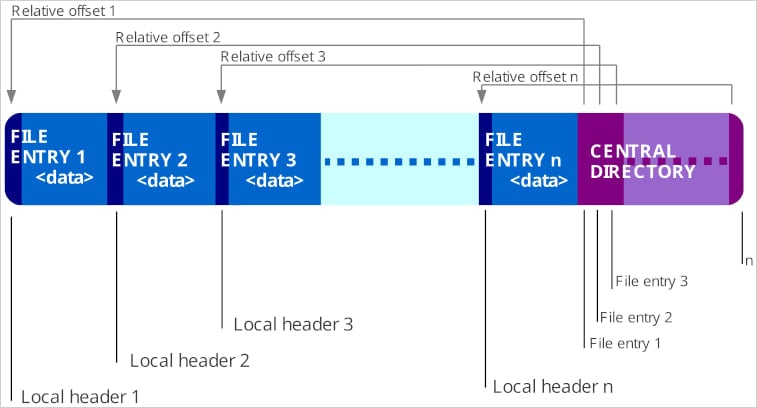
Although the final product appears as a single file, it contains multiple ZIP structures, each with its own central directory and end markers.
Internal structure of ZIP files
Source: Perception Point
Exploiting ZIP app flaws
In the next phase of the attack, hackers exploit how different ZIP parsers interpret concatenated archives. Perception Point tested various tools—7zip, WinRAR, and Windows File Explorer—and observed varied results:
- 7zip reads only the first ZIP archive, potentially benign, and may display a warning about extra data, which users could overlook.
- WinRAR displays both ZIP structures, exposing all files, including the hidden malicious payload.
- Windows File Explorer may struggle to open the concatenated file or, if renamed with a .RAR extension, may only display the second ZIP archive.
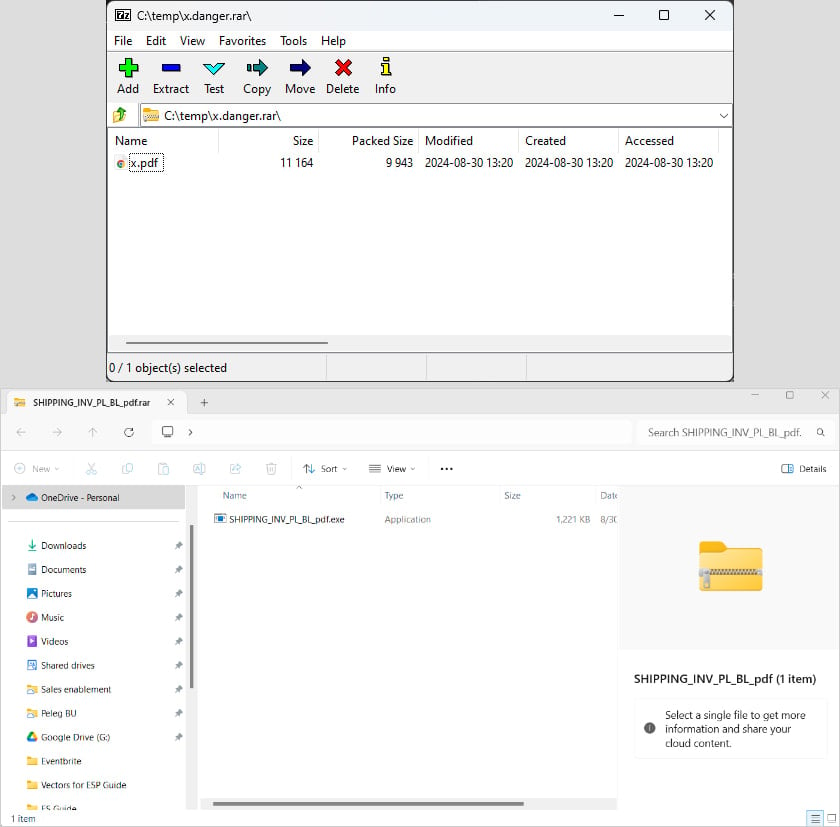
Based on these behaviors, attackers can adapt their strategy, for instance, by placing the malware in the first or second ZIP file. When Perception Point researchers opened the malicious archive with 7zip, only a harmless PDF appeared; however, with Windows File Explorer, the malicious executable was revealed.
7zip (top) and Windows File Explorer (bottom) opening the same file
Source: Perception Point
To protect against concatenated file attacks, Perception Point recommends that users and organizations deploy security solutions capable of recursive unpacking.
As a general precaution, emails containing ZIP or other archive file types should be approached with caution, and filters should be set up in critical environments to block these file extensions.
Source: BleepingComputer, Bill Toulas