Cybercriminals now exploit Meta’s advertising platforms by promoting fake offers of a free TradingView Premium app, which installs the Brokewell malware on Android devices.
The campaign specifically targets cryptocurrency assets, and since July 22nd, it has already run through an estimated 75 localized ads.
Brokewell emerged in early 2024 and carries a wide range of capabilities, including stealing sensitive data, remotely monitoring activity, and taking control of compromised devices.
Taking over the device
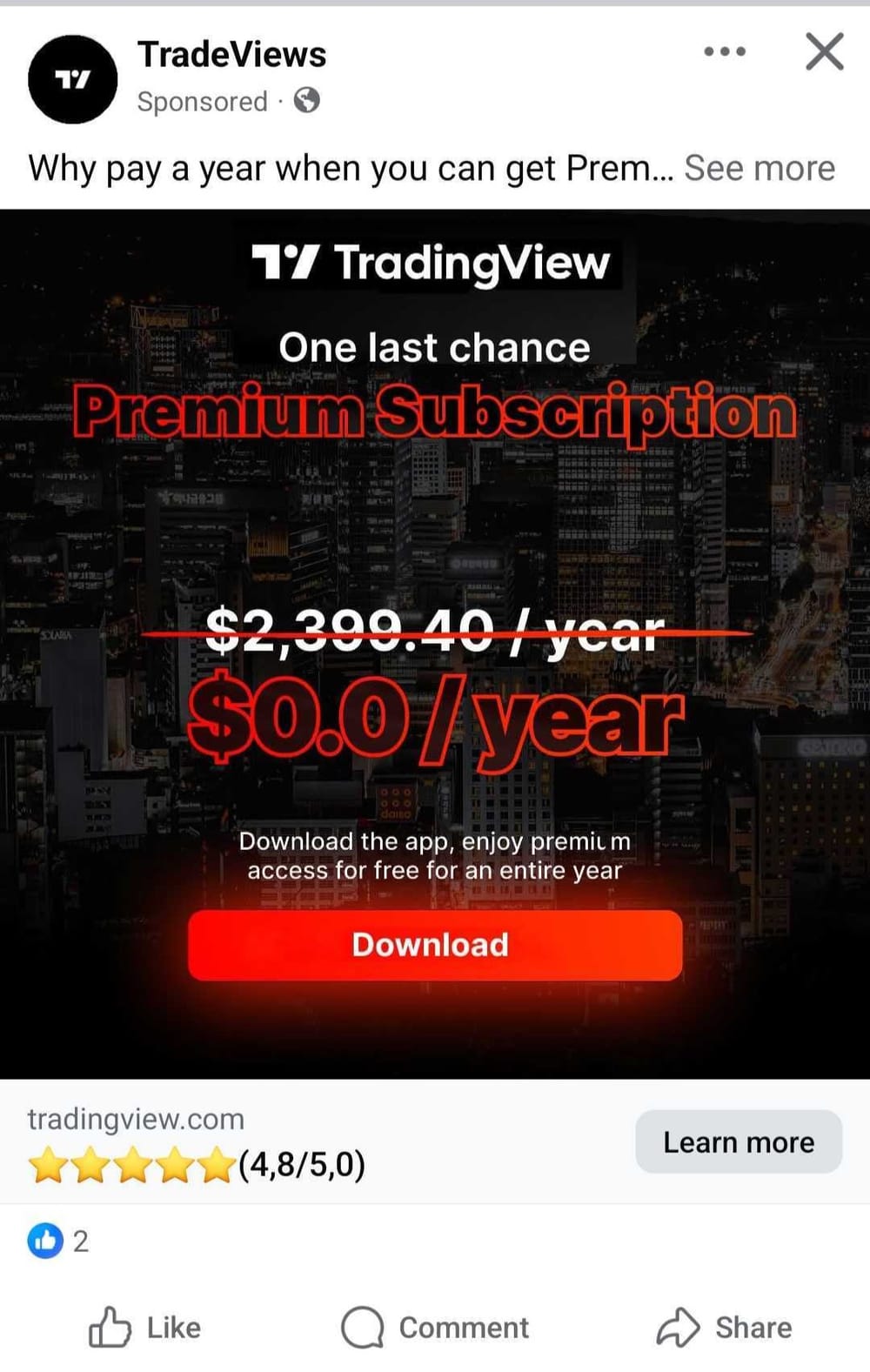
Researchers at cybersecurity company Bitdefender investigated the campaign’s ads, which use TradingView branding and visuals to lure victims with the promise of a free premium Android app.
Fake TradingView ad leading to Brokwell malware
Source: Bitdefender
Only Mobile Users
They explain that the attackers specifically designed the campaign for mobile users. When someone accesses the ad from another operating system, it leads only to harmless content.
Clicking from an Android device, however, redirects the user to a fake TradingView webpage that delivers a malicious file named tw-update.apk, hosted at tradiwiw[.]online.
The dropped application immediately asks for accessibility permissions. Once granted, it hides the screen behind a fake update prompt while secretly giving itself all the permissions it needs, according to the Bitdefender researchers.
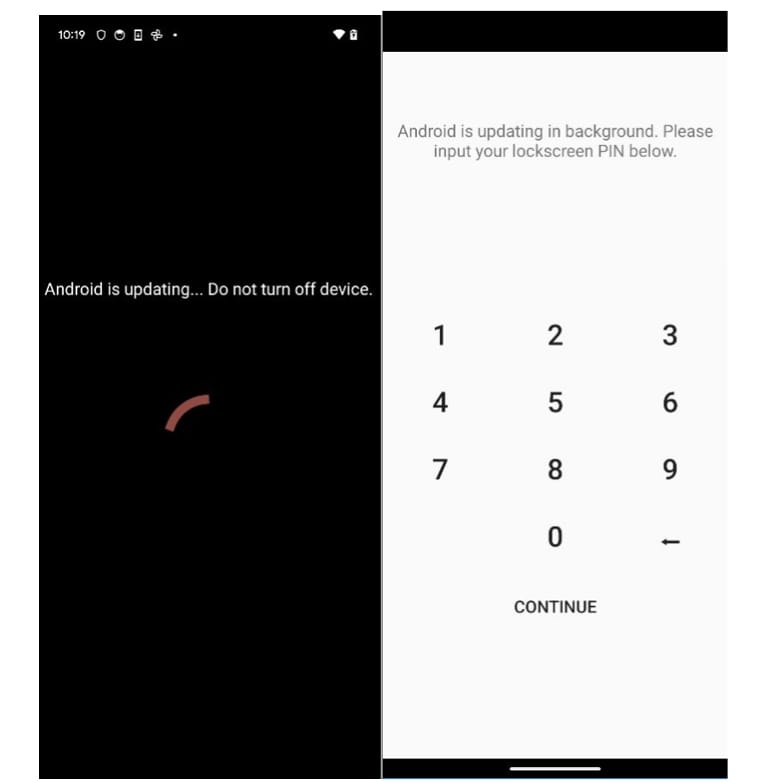
The malicious app also attempts to steal the device’s unlock PIN by simulating an Android update request that requires the lockscreen password.
Fake TradingView app tries to obtain Android device lockscreen code
Source: Bitdefender
Bitdefender identifies this fake TradingView app as “an advanced version of the Brokewell malware,” equipped with a vast arsenal of tools to monitor, control, and steal sensitive information, such as:
- Scanning for BTC, ETH, USDT, and bank account numbers (IBANs)
- Stealing and exporting Google Authenticator codes to bypass 2FA
- Taking over accounts with fake login overlays
- Recording screens and keystrokes, stealing cookies, activating the camera and microphone, and tracking location
- Hijacking the default SMS app to intercept messages, including banking and 2FA codes
- Receiving remote commands over Tor or Websockets to send texts, place calls, uninstall apps, or even self-destruct
The researchers also share a detailed technical overview of Brokewell’s inner workings, which includes a list of more than 130 supported commands.
Finally, Bitdefender places this campaign within a larger operation that originally used Facebook ads impersonating dozens of well-known brands to target Windows users.
Source: BleepingComputer, Ionut Ilascu
Read more at Impreza News