Hackers are exploiting outdated versions of the HTTP File Server (HFS) from Rejetto to deploy malware and cryptocurrency mining tools.
According to threat researchers at AhnLab, the attackers are leveraging CVE-2024-23692, a critical vulnerability that permits the execution of arbitrary commands without authentication.
This flaw impacts software versions up to and including 2.3m. Rejetto has issued a warning on their website, advising users that versions 2.3m through 2.4 are “dangerous and should not be used anymore” due to a bug that allows attackers to “control your computer” with no fix currently available.
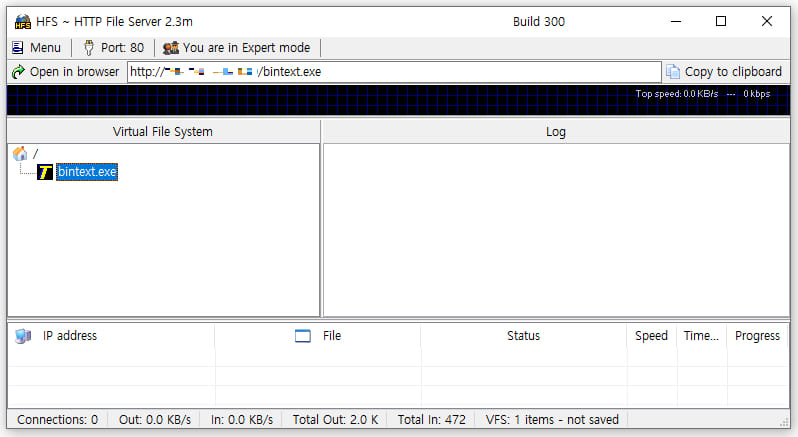
Rejetto HFS 2.3m
Source: ASEC
Observed attacks
The AhnLab Security Intelligence Center (ASEC) has detected attacks targeting version 2.3m of HFS, a version still widely used by individual users, small teams, educational institutions, and developers for network file sharing tests.
Researchers believe the attackers are exploiting CVE-2024-23692, a vulnerability identified by security researcher Arseniy Sharoglazov last August and publicly disclosed in a technical report in May.
CVE-2024-23692 is a template injection vulnerability that enables unauthenticated remote attackers to execute arbitrary commands by sending a specially crafted HTTP request to the affected system.
Following the disclosure, a Metasploit module and proof-of-concept exploits were made available, marking the beginning of active exploitation, according to ASEC.
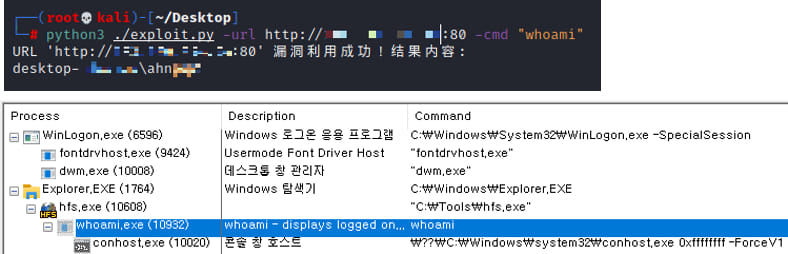
During these attacks, hackers gather system information, install backdoors, and deploy various malware types. They execute commands like “whoami” and “arp” to collect data about the system and user, identify connected devices, and plan further actions.
Malicious activity conducted through the HFS process
Source: ASEC
In numerous instances, attackers terminate the HFS process after adding a new user to the administrators’ group to prevent other threat actors from exploiting it.
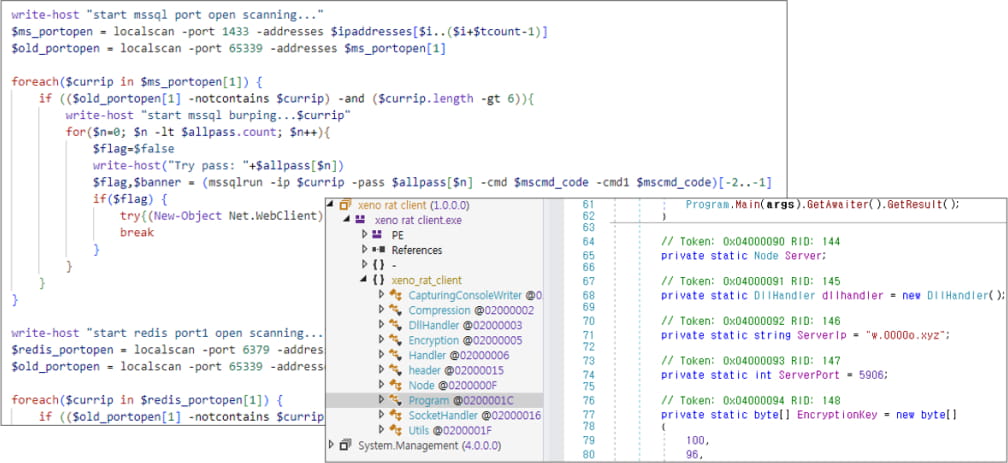
In subsequent stages of the attacks, ASEC observed the installation of the XMRig tool for Monero cryptocurrency mining. Researchers reported that XMRig was deployed in at least four distinct attacks, with one attributed to the LemonDuck threat group.
Other payloads delivered to compromised systems include:
- XenoRAT: Deployed alongside XMRig for remote access and control.
- Gh0stRAT: Utilized for remote control and data exfiltration from breached systems.
- PlugX: A backdoor often associated with Chinese-speaking threat actors, used for maintaining persistent access.
- GoThief: An information stealer leveraging Amazon AWS to exfiltrate data. It captures screenshots, collects desktop file information, and transmits data to an external command and control (C2) server.
LemonDuck’s XenoRAT and scanner tool
Source: ASEC
AhnLab researchers continue to detect attacks on version 2.3m of HFS. Since the server must be exposed online for file sharing to occur, hackers are likely to keep targeting vulnerable versions.
The recommended version of the product is 0.52.x, which, despite its lower numbering, is the latest HFS release from the developer. This version is web-based, requires minimal configuration, and supports HTTPS, dynamic DNS, and authentication for the administrative panel.
The company’s report provides a set of indicators of compromise, including hashes for the malware installed on breached systems, IP addresses for attacker command and control servers, and the download URLs for the malware used in the attacks.
Source: BleepingComputer, Bill Toulas