Cybersecurity researchers have discovered a new campaign attributed to the Chinese “Tropic Trooper” hacking group, which employs a novel loader called Nimbda and a new variant of the Yahoyah trojan.
The trojan is bundled in a greyware tool named ‘SMS Bomber,’ which is used for denial of service (DoS) attacks against phones, flooding them with messages. Tools like this are commonly used by “beginner” threat actors who want to launch attacks against sites.
According to a report by Check Point, the threat actors also demonstrate in-depth cryptographic knowledge, extending the AES specification in a custom implementation.
Attack chain
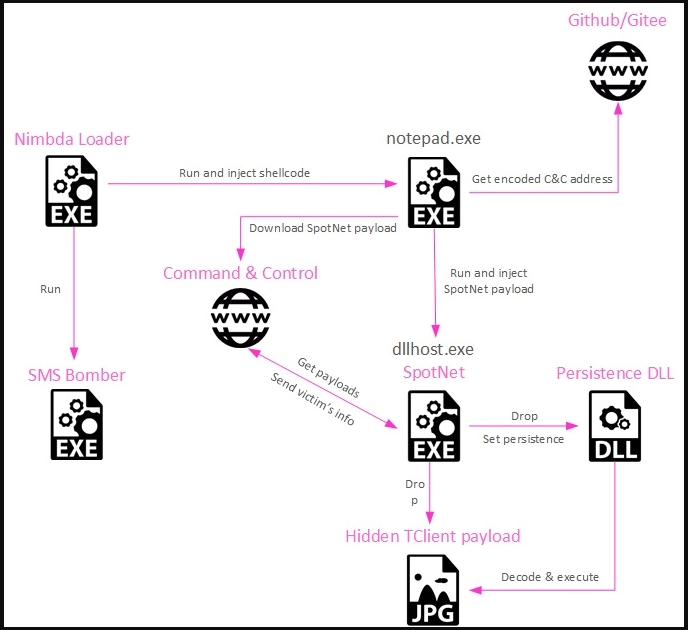
The infection begins with downloading a malicious version of SMS Bomber, which contains the tool’s binary and standard functionality. However, the download has been modified to include additional code that injects into a notepad.exe process.
The downloaded executable is actually the ‘Nimbda’ loader, which uses the SMS Bomber icon, and contains SMS Bomber as an embedded executable.
The SMS Bomber GUI tool (Check Point)
In the background, the loader injects shellcode into the notepad process to reach a GitHub repository, fetch an obfuscated executable, decode it, and then run it via process hollowing in ‘dllhost.exe.’
This payload is the new Yahoyah variant, which collects data about the host and sends it to the C2 server. The information collected by Yahoyah includes the following:
- local wireless network SSIDs in the victim machine’s vicinity
- computer name
- MAC address
- OS version
- installed AV products
- presence of WeChat and Tencent files
The final payload, dropped by the Yahoyah executable, is encoded in a JPG image using steganography. Check Point identifies it as ‘TClient,’ a backdoor Tropic Trooper used in past campaigns.
Custom AES implementation
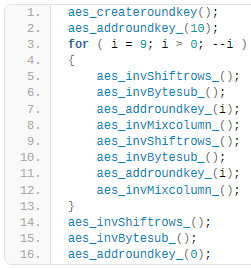
The encryption used to wrap Yahoyah is a custom implementation of AES, which performs the inverted sequence of round operations twice; hence Check Point names it AEES.
This doesn’t make encryption stronger but makes analysis of the sample very difficult, discouraging researchers who aren’t determined enough or making their work much more tedious.
“Getting an analyst to go through that entire rigmarole is a cruel and effective feat, especially for the meager cost on the malware author’s side,” comments Check Point.
“They just need the knowledge and self-confidence to mess with the crypto in a way that will not render it nonoperational.”
Peculiar targeting
Tropic Trooper is a sophisticated threat actor focused on espionage, previously seen running phishing campaigns against Russian officials.
Trojanizing’ SMS Bomb’ indicates precise, narrow targeting, so it’s likely a decision based on intelligence collected during preceding espionage.
While the exact targeting scope is unknown, this campaign demonstrates Tropic Trooper’s capability to create any decoy needed for their operations, cryptographic knowledge, and malware development activity.
Source: BleepingComputer