Hackers are increasingly targeting Windows users with the malicious Winos4.0 framework, which is distributed through seemingly harmless game-related applications.
This toolkit serves as an alternative to the Sliver and Cobalt Strike post-exploitation frameworks, and it was documented by Trend Micro in a report this summer detailing attacks on Chinese users.
At that time, a threat actor known as Void Arachne, or Silver Fox, attracted victims by offering various software, like VPNs and a modified Google Chrome browser, specifically tailored for the Chinese market and bundled with the malicious component.
A report released today by the cybersecurity company Fortinet highlights a development in this activity, revealing that hackers are now using games and game-related files to continue targeting Chinese users.
Malicious files infecting users with Winos4.0
Source: Fortinet
When these seemingly legitimate installers are run, they download a DLL file from “ad59t82g[.]com” to begin a multi-stage infection process.
In the first stage, a DLL file (you.dll) downloads additional files, configures the execution environment, and establishes persistence by adding entries to the Windows Registry.
In the second stage, injected shellcode loads APIs, retrieves configuration details, and establishes a connection with the command-and-control (C2) server.
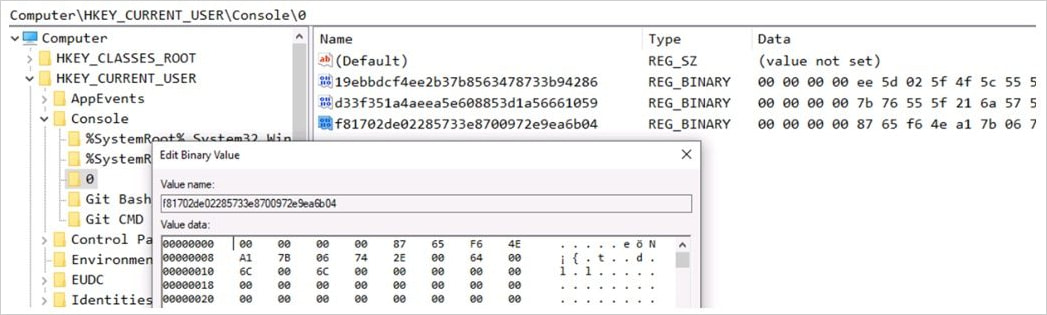
In the third stage, another DLL (上线模块.dll) retrieves additional encoded data from the C2 server, stores it in the registry at “HKEY_CURRENT_USER\Console\0,” and updates the C2 addresses.
Malware modules added onto the Registry
Source: Fortinet
In the final stage of the attack chain, the login module (登录模块.dll) is loaded to carry out the main malicious activities:
- Collects system and environment details, including IP address, operating system information, and CPU specifications.
- Scans for any anti-virus and monitoring software running on the host.
- Collects information on specific cryptocurrency wallet extensions used by the victim.
- Maintains a persistent backdoor connection to the C2 server, enabling the attacker to issue commands and retrieve further data.
- Exfiltrates data by capturing screenshots, monitoring clipboard activity, and stealing documents.
Complete Winos4.0 attack chain
Source: Fortinet
Winos4.0 scans the system for various security tools, including Kaspersky, Avast, Avira, Symantec, Bitdefender, Dr.Web, Malwarebytes, McAfee, AhnLab, ESET, Panda Security, and the now-discontinued Microsoft Security Essentials.
By detecting these processes, the malware can determine if it is operating in a monitored environment and either alters its behavior or halts execution entirely.
Hackers have been utilizing the Winos4.0 framework for several months, and the emergence of new campaigns suggests its increasing role in malicious operations.
Fortinet characterizes the framework as a powerful tool capable of controlling compromised systems, with features similar to Cobalt Strike and Sliver. Indicators of compromise (IoCs) are provided in reports from both Fortinet and Trend Micro.
Source: BleepingComputer, Bill Toulas

















.jpeg)








