More than 10,000 Docker Hub container images now expose data that developers should protect, including live credentials to production systems, CI/CD databases, or LLM model keys.
Moreover, the secrets affect a little over 100 organizations, and among them appear a Fortune 500 company and a major national bank.
Docker Hub serves as the largest container registry where developers upload, host, share, and distribute ready-to-use Docker images that contain everything necessary to run an application.
Developers typically rely on Docker images to streamline the entire software development and deployment lifecycle. However, as past studies have shown, developers often create these images carelessly and consequently expose secrets that remain valid for extended periods.
What the Researchers Found
After scanning container images uploaded to Docker Hub in November, security researchers at threat intelligence company Flare analyzed the results and found that 10,456 of them exposed one or more keys.
Additionally, the most frequent secrets included access tokens for various AI models (OpenAI, HuggingFace, Anthropic, Gemini, Groq). In total, the researchers uncovered 4,000 such keys.
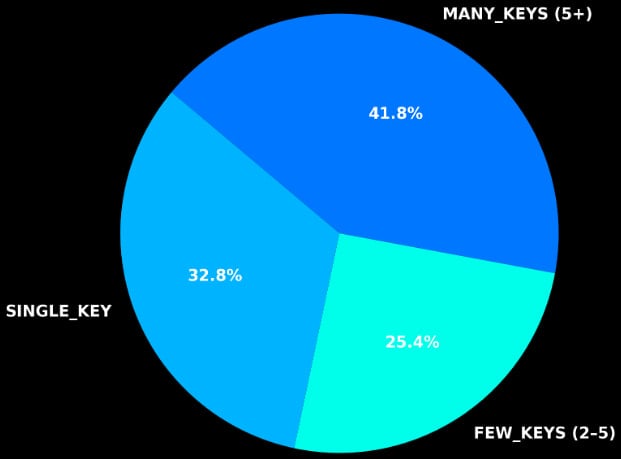
When examining the scanned images, the researchers also noticed that 42% of them exposed at least five sensitive values.
“These multi-secret exposures represent critical risks, as they often provide full access to cloud environments, Git repositories, CI/CD systems, payment integrations, and other core infrastructure components,” Flare notes in a report today.
Size of secret exposure
Source: Flare
Analyzing 205 namespaces enabled the researchers to identify a total of 101 companies, mostly small and medium-sized businesses, with a few large enterprises appearing in the dataset.
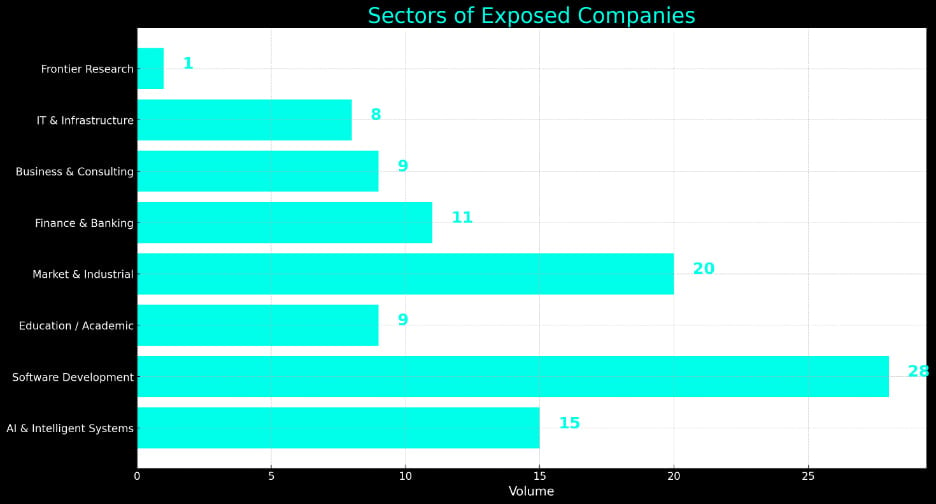
Additionally, based on the analysis, most organizations with exposed secrets operate in the software development sector, followed by entities in the market and industrial, and AI and intelligent systems.
More than 10 finance and banking companies also experienced exposure of their sensitive data.
Types of firms that exposed secrets on Docker Hub in November
Source: Flare
How the Info Leaked
According to the researchers, one of the most frequent errors came from developers who stored database credentials, cloud access keys, tokens, and various authentication data in .ENV files.
Additionally, the researchers found AI service API tokens hardcoded in Python application files, config.json files, YAML configs, GitHub tokens, and credentials for multiple internal environments.
Some of the sensitive data even appeared in the manifest of Docker images, a file that provides details about the image.
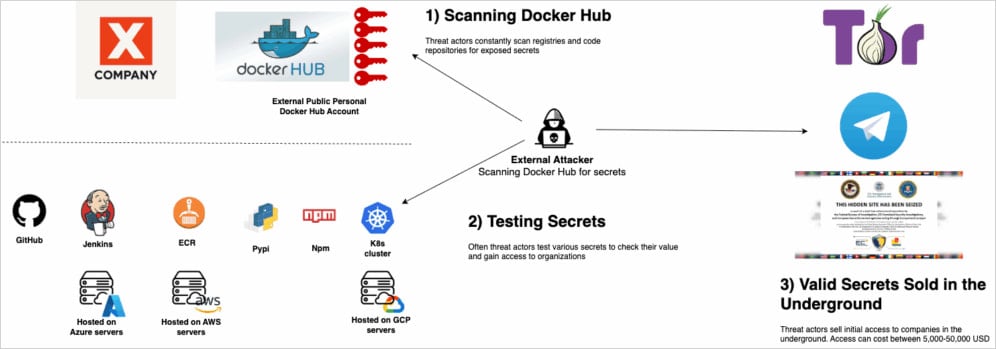
Furthermore, many of the leaks originated from the so-called “shadow IT” accounts, which include Docker Hub accounts outside stricter corporate monitoring mechanisms, such as personal accounts or accounts belonging to contractors.
Flare notes that roughly 25% of developers who accidentally exposed secrets on Docker Hub recognized the mistake and removed the leaked secret from the container or manifest file within 48 hours.
However, in 75% of these cases, the developers did not revoke the leaked key, meaning that anyone who stole it during the exposure period could still use it later to mount attacks.
Exposed secrets exploitation diagram
Source: Flare
Recommendations Going Forward
Flare suggests that developers avoid storing secrets in container images, stop relying on static and long-lived credentials, and centralize their secrets management using a dedicated vault or secrets manager.
Organizations should also implement active scanning across the entire software development life cycle and revoke exposed secrets and invalidate old sessions immediately.
Source: BleepingComputer, Bill Toulas
Read more at Impreza News