SonicWall warned customers today to patch a vulnerability in the SonicWall SMA1000 Appliance Management Console (AMC) after attackers chained it in zero-day attacks to escalate privileges.
Vulnerability Disclosure and Scope
According to SonicWall, researchers Clément Lecigne and Zander Work from the Google Threat Intelligence Group reported the medium-severity local privilege escalation flaw, tracked as CVE-2025-40602. Importantly, the issue does not affect SSL-VPN services running on SonicWall firewalls.
“SonicWall PSIRT strongly advises users of the SMA1000 product to upgrade to the latest hotfix release version to address the vulnerability,” the company said in a Wednesday advisory.
Meanwhile, remote unauthenticated attackers chained this vulnerability with a critical pre-authentication deserialization flaw in SMA1000 (CVE-2025-23006) during zero-day attacks. As a result, attackers executed arbitrary operating system commands under specific conditions.
“This vulnerability was reported to be leveraged in combination with CVE-2025-23006 (CVSS score 9.8) to achieve unauthenticated remote code execution with root privileges. CVE-2025-23006 was remediated in build version 12.4.3-02854 (platform-hotfix) and higher versions (released on Jan 22, 2025).”
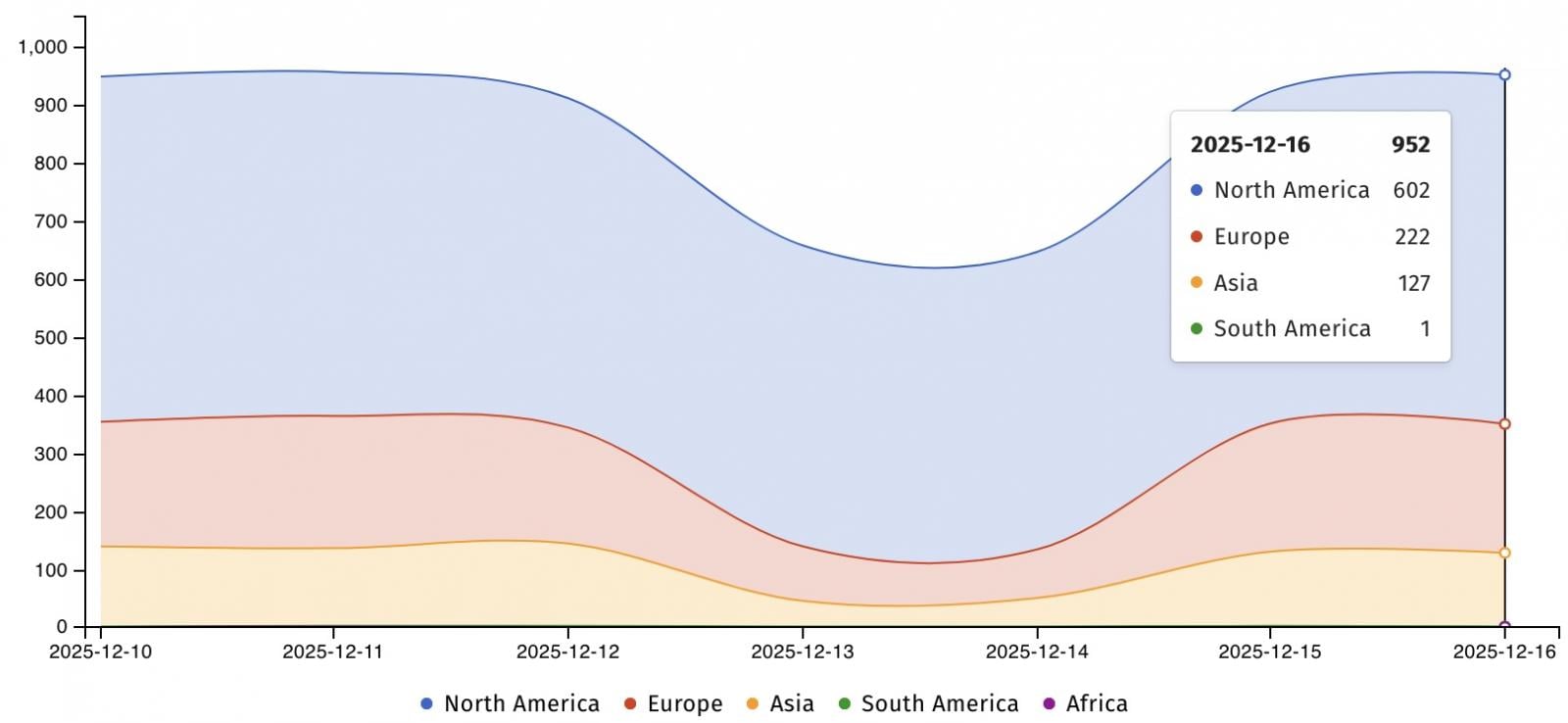
Currently, internet monitoring group Shadowserver tracks more than 950 SMA1000 appliances exposed online. However, some organizations may have already patched their devices against this attack chain.
Internet exposed SMA1000 appliances (Shadowserver)
Why SMA1000 Devices Are High-Value Targets
SMA1000 appliances provide secure remote access and VPN connectivity for large organizations. Because enterprises, government agencies, and critical infrastructure operators widely deploy these systems, attackers can easily exploit unpatched vulnerabilities to gain high-impact access.
Last month, SonicWall linked state-backed hackers to a September security breach that exposed customers’ firewall configuration backup files. The disclosure followed researchers’ warnings that attackers had compromised more than 100 SonicWall SSLVPN accounts using stolen credentials.
In September, SonicWall also released a firmware update to help IT administrators remove OVERSTEP rootkit malware deployed in attacks targeting SMA 100 series devices.
Earlier, SonicWall dismissed claims that the Akira ransomware gang exploited a zero-day vulnerability to hack Gen 7 firewalls. Instead, the company attributed the incidents to CVE-2024-40766, a critical vulnerability it patched in November 2024.
Subsequently, cybersecurity firm Rapid7 and the Australian Cyber Security Center confirmed SonicWall’s findings, stating that the Akira gang continues to exploit CVE-2024-40766 to target unpatched SonicWall devices.
Source: BleepingComputer, Sergiu Gatlan
Read more at Impreza News