Claims administration and risk management company Sedgwick has confirmed that its federal contractor subsidiary, Sedgwick Government Solutions, fell victim to a security breach.
Meanwhile, Sedgwick employs over 33,000 people and serves 10,000 clients across 80 countries, including 59% of the Fortune 500, while its subsidiary supports more than 20 government agency clients.
Specifically, the list of federal agencies using Sedgwick Government Solutions’ services includes the Cybersecurity and Infrastructure Security Agency (CISA), the Department of Commerce, the United States Citizenship and Immigration Services (USCIS), the United States Coast Guard, the Department of Homeland Security (DHS), the U.S. Department of Labor, the Customs and Border Protection (CBP), and the U.S. Coast Guard.
Company Response and Investigation Efforts
In response, a Sedgwick spokesperson told BleepingComputer that the company is currently investigating a security breach that impacted its subsidiary, adding that the parent company’s network did not experience any impact.
Additionally, Sedgwick has notified law enforcement and has brought in external cybersecurity experts to assess the scope and consequences of the breach.
“Sedgwick is addressing a security incident at one of its subsidiaries, Sedgwick Government Solutions. Following the detection of the incident, we initiated our incident response protocols and engaged external cybersecurity experts through outside counsel to assist with our investigation of the affected isolated file transfer system,” the spokesperson said.
“Importantly, Sedgwick Government Solutions is segmented from the rest of our business, and no wider Sedgwick systems or data were affected. Further, there is no evidence of access to claims management servers nor any impact on Sedgwick Government Solutions ability to continue serving its clients. We have notified law enforcement and remain in contact with our clients as we conduct our investigation.”
Ransomware Group Claims Responsibility
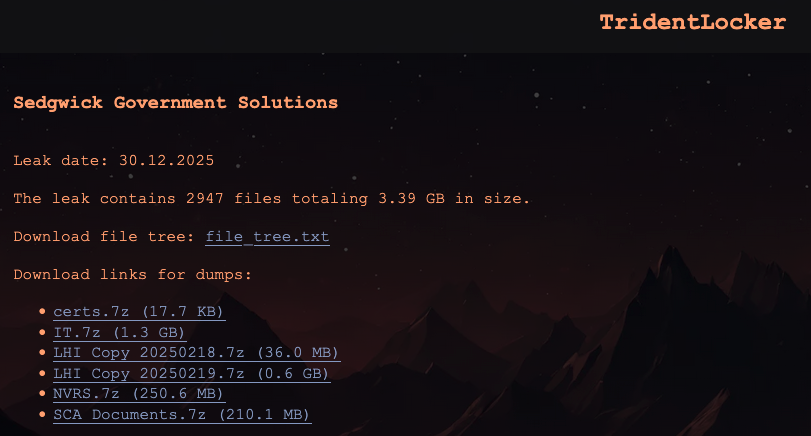
Although the company did not attribute the attack to a specific threat group, the statement nonetheless aligns with claims from the TridentLocker ransomware group, which says it breached the company.
According to the threat actors, they stole 3.39 GB of documents and, after taking responsibility for the attack, published some of the allegedly stolen data on their Tor-based data leak site.
Sedgwick Government Solutions TridentLocker entry (BleepingComputer)
Background on TridentLocker Activity
TridentLocker ransomware first surfaced in November and currently lists around a dozen victims on its leak site, including Bpost (Belgian Post Group), which delivers mail across Belgium and ranks among the country’s largest civilian employers.
Previously, Bpost confirmed that attackers breached its network on December 3rd but stated that the TridentLocker ransomware attack did not disrupt its operations.
Source: BleepingComputer, Sergiu Gatlan
Read more at Impreza News