Cybercriminals linked to the North Korean government, known as Lazarus, one of the most prolific groups in 2020, are targeting espionage attacks on security companies since the beginning of this year.
According to Kaspersky researchers, Lazarus is a group that has been active since 2009 and has already organized campaigns for ransonware, cyber espionage and attacks against the cryptocurrency market. Since the beginning of this year, its focus has been on the security industry.
This is not the first time that the group has directed attacks on the industry of the sector. In the middle of 2020, Kaspersky identified the group using malware from a family that the company calls ThreatNeedle, the same family of malware they are using now.
“We’ve seen Lazarus attack various industries using this malware cluster. In mid-2020, we realized that Lazarus was launching attacks on the defense industry using the ThreatNeedle cluster, a cluster of advanced Manuscrypt malware (known as NukeSped). By investigating this activity, we were able to observe the full life cycle of an attack, discovering more technical details and links to other group campaigns, “write Seongsu Park and Vyacheslav Kopeytsev, in a study published on Thursday (25).
Attacks against the security industry
The researchers explain that financial institutions, especially those dealing with cryptocurrencies, have always been the main focus of Lazarus. However, since the middle of 2020 the group has been “aggressively attacking” defense and security companies, mainly because they have many governments and armies as customers.
“In this campaign, the Lazarus group demonstrated its level of sophistication and ability to circumvent the security measures they face during their attacks, such as network segmentation. Lazarus is a highly prolific group, conducting multiple campaigns using different strategies. They shared tools and infrastructure between these campaigns to achieve their goals “, write the researchers.
The researchers believe that the focus on these companies aims to get data from armies and governments, since these companies have a strong data relationship with government entities.
ThreatNeedle Strategy
As with most targeted attacks, attackers use phishing as an initial infection vector. “The group studied the publicly available information about the target organization and identified e-mail addresses belonging to various departments of the company [para realizar os ataques]”, they write.
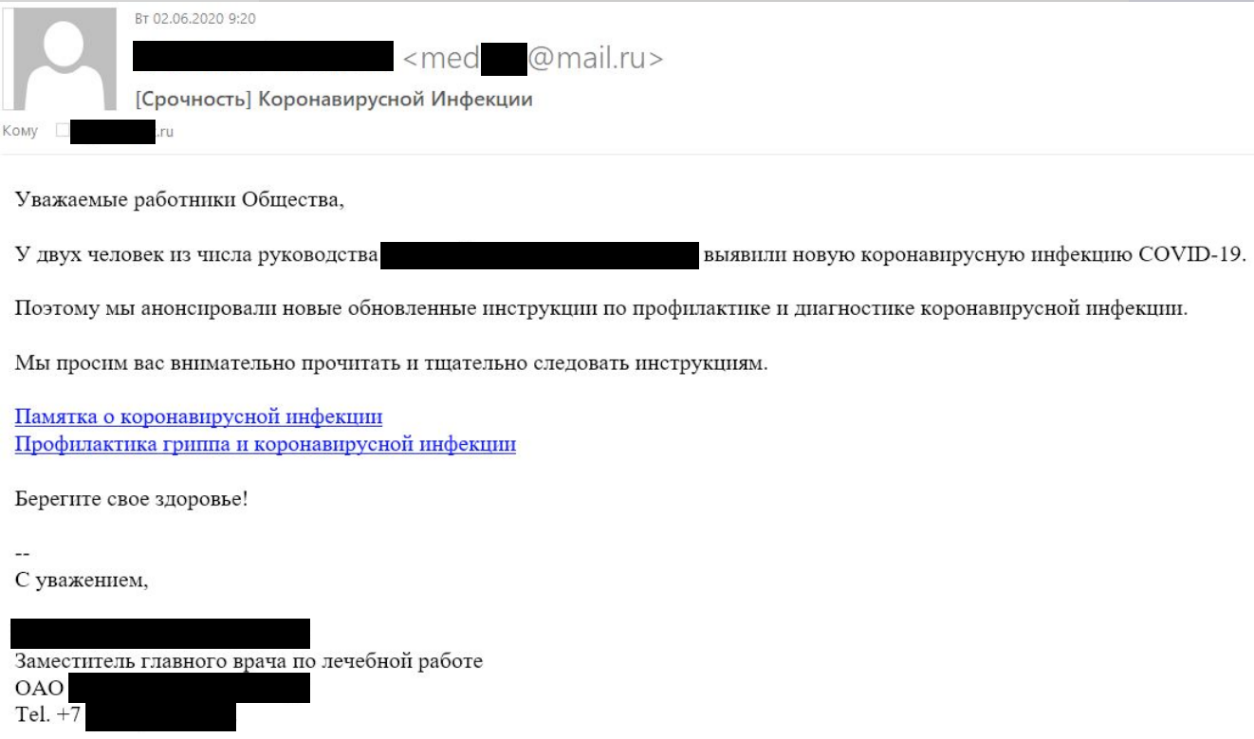
Along with the phishing email, which claimed to have urgent updates on COVID-19, a .docx file infected with malicious code has been attached. “A macro in the Microsoft Word document contained malicious code designed to download and run additional malicious software on the infected system.”
The .docx file contains a script that installs a ThreatNeedle backdoor, which allows remote access to the infected victim’s computer and data. After this initial backdoor, cybercriminals begin the process of infection with other types of malware, in addition to lateral movement.
“This installer is responsible for deploying the next-stage loader-type malware and registering it for automatic execution for persistence. ThreatNeedle loader-type malware exists in several variations and serves the primary purpose of loading the final stage of the malware ThreatNeedle in memory “, they write.
Once backdoor is definitely configured, the group begins the process of lateral movement, inserting more malware as needed and collecting intelligence data.
Source: Securelist (Kaspersky).
See the original post at: https://thehack.com.br/hackers-de-elite-da-coreia-do-norte-miram-empresas-de-seguranca/?rand=48873