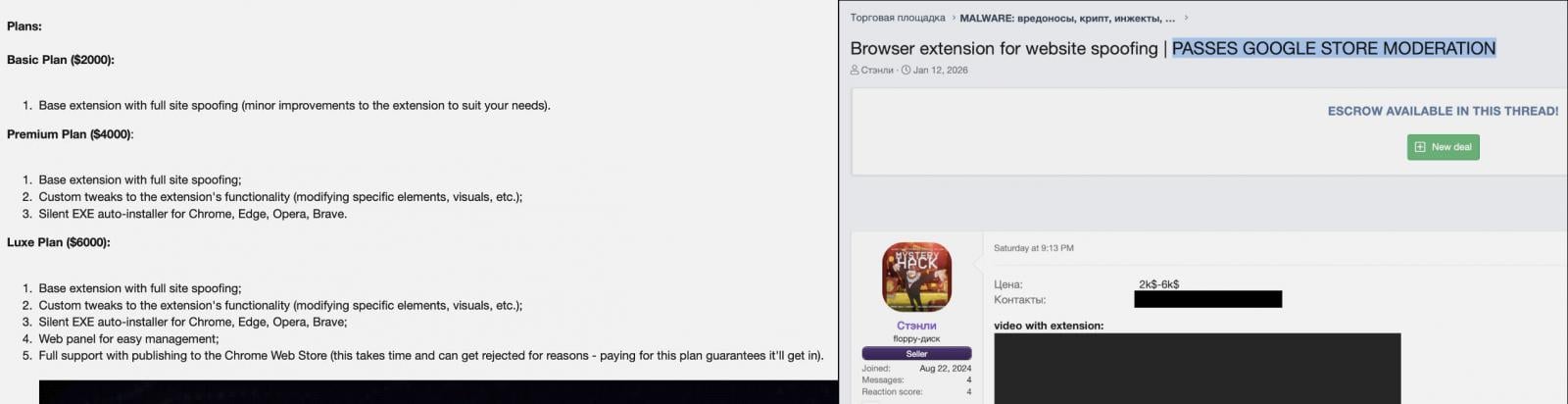
A new malware-as-a-service (MaaS) called “Stanley” promises malicious Chrome extensions that can clear Google’s review process and publish directly to the Chrome Web Store.
According to researchers at end-to-end data security company Varonis, the team named the project Stanley after the seller’s alias. Notably, the seller promotes easy phishing attacks by intercepting navigation and overlaying webpages with an iframe that displays attacker-controlled content.
At its core, the new MaaS offering delivers malicious Chrome extensions that can overlay any webpage with a full-screen iframe containing phishing content chosen by the attacker. In addition, Stanley advertises silent auto-installation on Chrome, Edge, and Brave browsers, along with support for custom tweaks.
Pricing and Distribution Model
Meanwhile, Stanley operates across multiple subscription tiers, with the most expensive option branded as the Luxe Plan. This tier notably includes access to a web-based control panel and full support for publishing malicious extensions to the Chrome Web Store.
Stanley promoted on cybercrime portals
Source: Varonis
In response to these claims, BleepingComputer has contacted Google to request comment and will update the post once it receives a response.
Varonis reports that Stanley overlays a full-screen iframe containing malicious content while leaving the browser’s address bar untouched, which continues to display the legitimate domain. As a result, victims may struggle to recognize the attack.
Function that generates the deceptive iframe
Source: Varonis
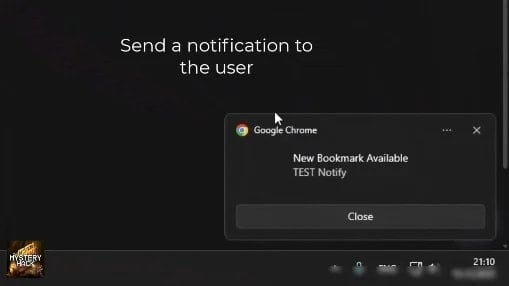
Furthermore, operators with access to Stanley’s control panel can enable or disable hijacking rules on demand. They can also push browser notifications directly to victims to lure them toward specific pages, thereby accelerating the phishing process.
Generating a custom notification
Source: Varonis
Targeting, Persistence, and Infrastructure
Beyond that, Stanley supports IP-based victim identification, enabling geographic targeting and correlation across sessions and devices. Moreover, the malicious extension performs persistent command-and-control (C2) polling every 10 seconds and rotates backup domains to maintain resilience against takedown efforts.
From a technical standpoint, Varonis notes that Stanley avoids advanced capabilities and instead relies on straightforward implementations of well-known techniques. The researchers describe the code as “rough” in places, citing Russian-language comments, empty catch blocks, and inconsistent error handling.
Nevertheless, Stanley distinguishes itself through its distribution strategy—specifically, its promise to pass Chrome Web Store reviews and place malicious extensions on the world’s largest repository of trusted browser add-ons.
User Risk and Defensive Guidance
Finally, as malicious extensions continue to evade detection—an issue recently underscored by separate reports from Symantec and LayerX—users should install only essential extensions, carefully review user feedback, and verify the publisher’s legitimacy before adding any browser add-ons.
Source: BleepingComputer, Bill Toulas
Read more at Impreza News














.jpg)