Hackers are actively exploiting LinkedIn to target finance executives through direct-message phishing attacks. They impersonate executive board invitations and attempt to steal Microsoft credentials.
Push Security recently discovered and blocked one of these phishing attempts after detecting a malicious LinkedIn message containing a harmful link.
The phishing messages pretend to invite executives to join the executive board of a newly created “Common Wealth” investment fund.
“I’m excited to extend an exclusive invitation for you to join the Executive Board of Common Wealth investment fund in South America in partnership with AMCO – Our Asset Management branch, a bold new venture capital fund launching a Investment Fund in South America,” reads the LinkedIn phishing message.
These phishing messages conclude by encouraging recipients to click a link for more details about the supposed opportunity.
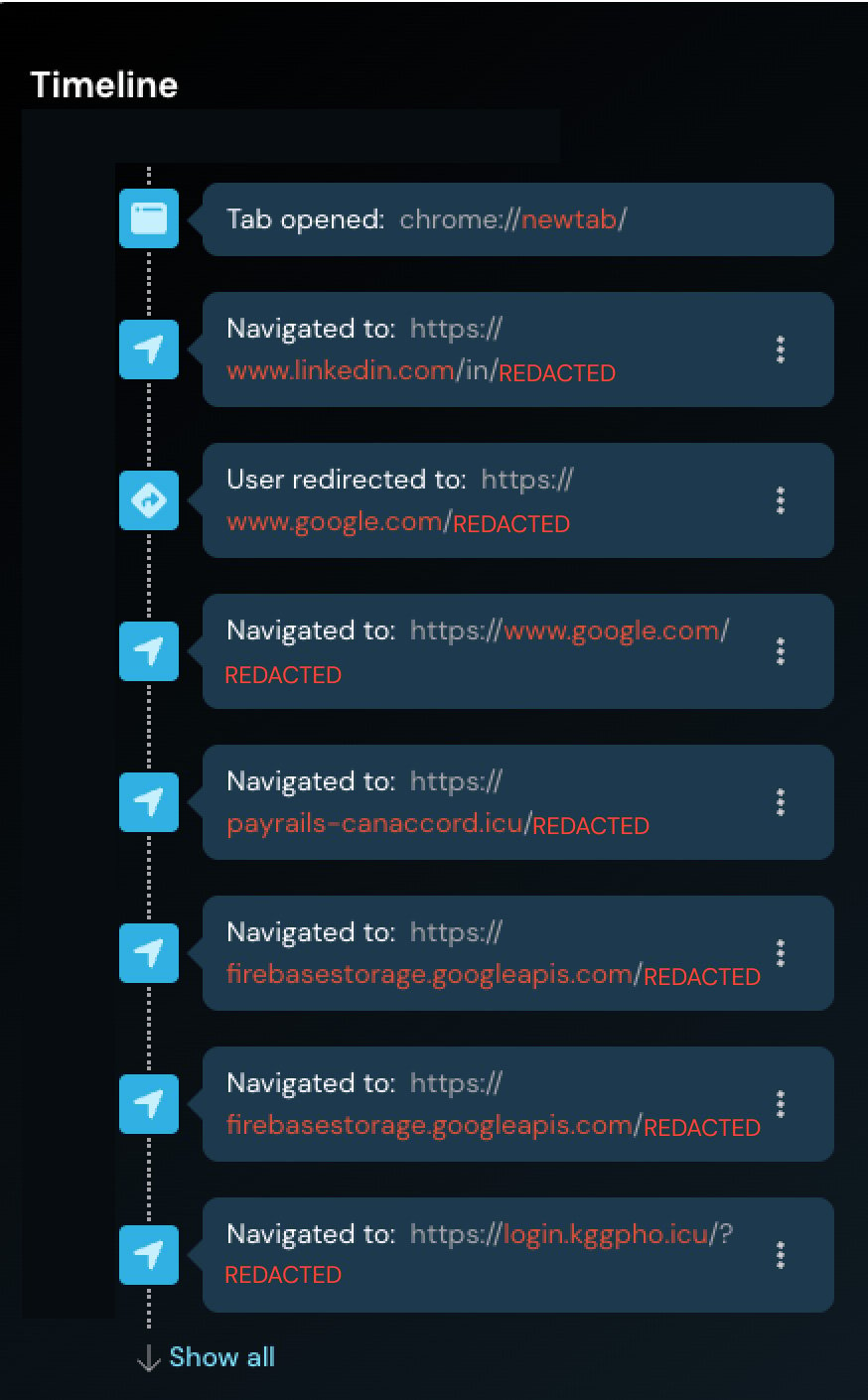
Once the target clicks the link, Push Security explains that the victim passes through several redirects. The first redirect uses a Google open redirect, which sends them to an attacker-controlled site. From there, the user lands on a custom page hosted on firebasestorage.googleapis[.]com.
Redirect chain used in the phishing attack
Source: Push Security
More Domains
Push Security and BleepingComputer identified several malicious domains connected to this campaign, including payrails-canaccord[.]icu, boardproposalmeet[.]com, and sqexclusiveboarddirect[.]icu.
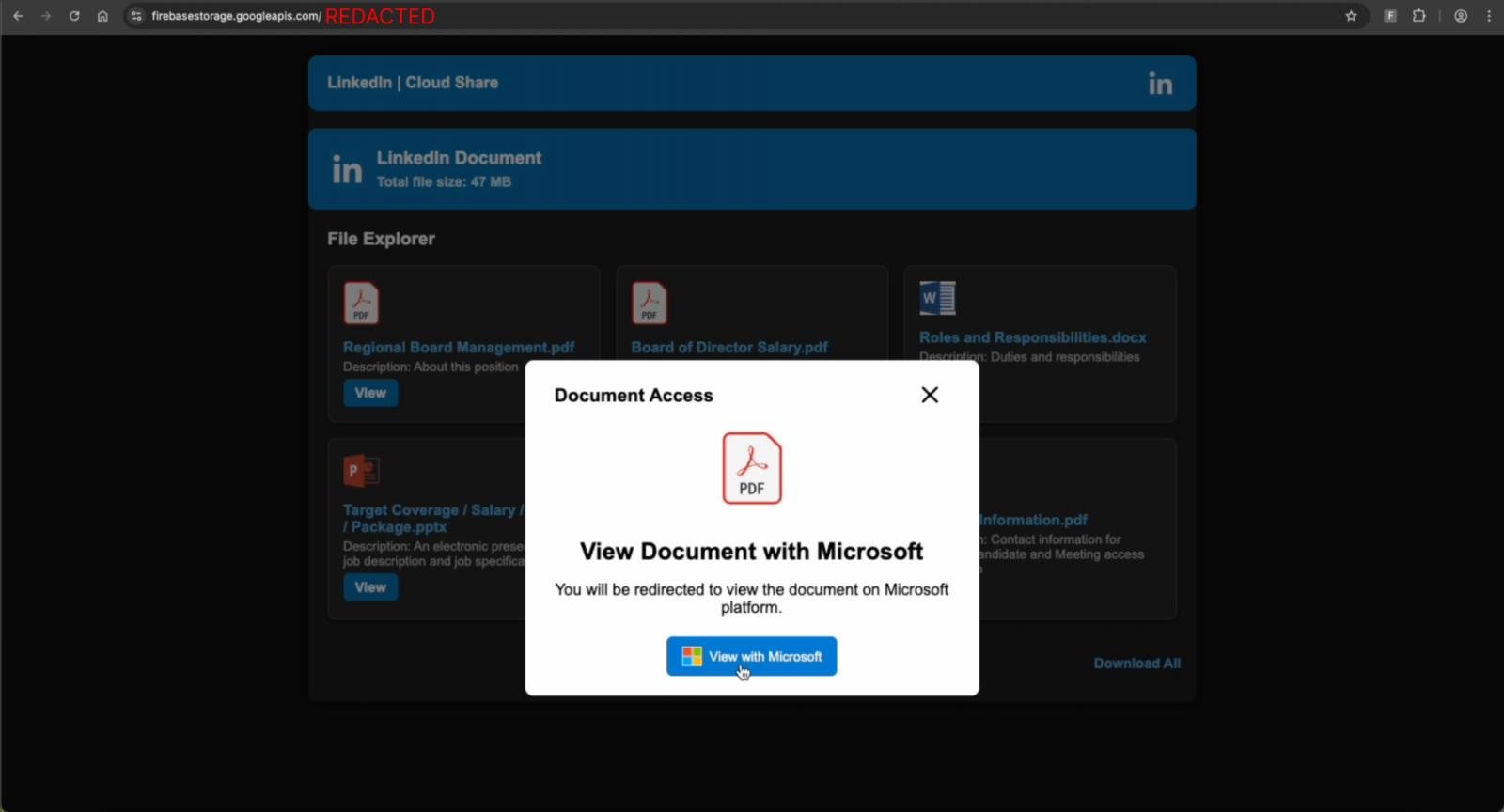
The Firebase landing page poses as a “LinkedIn Cloud Share” portal that appears to host documents related to the board membership role and its responsibilities.
When victims attempt to open one of these files, an alert prompts them to click the “View with Microsoft” button to gain access.
Fake LinkedIn Cloud Share platform on Firebase
Source: Push Security
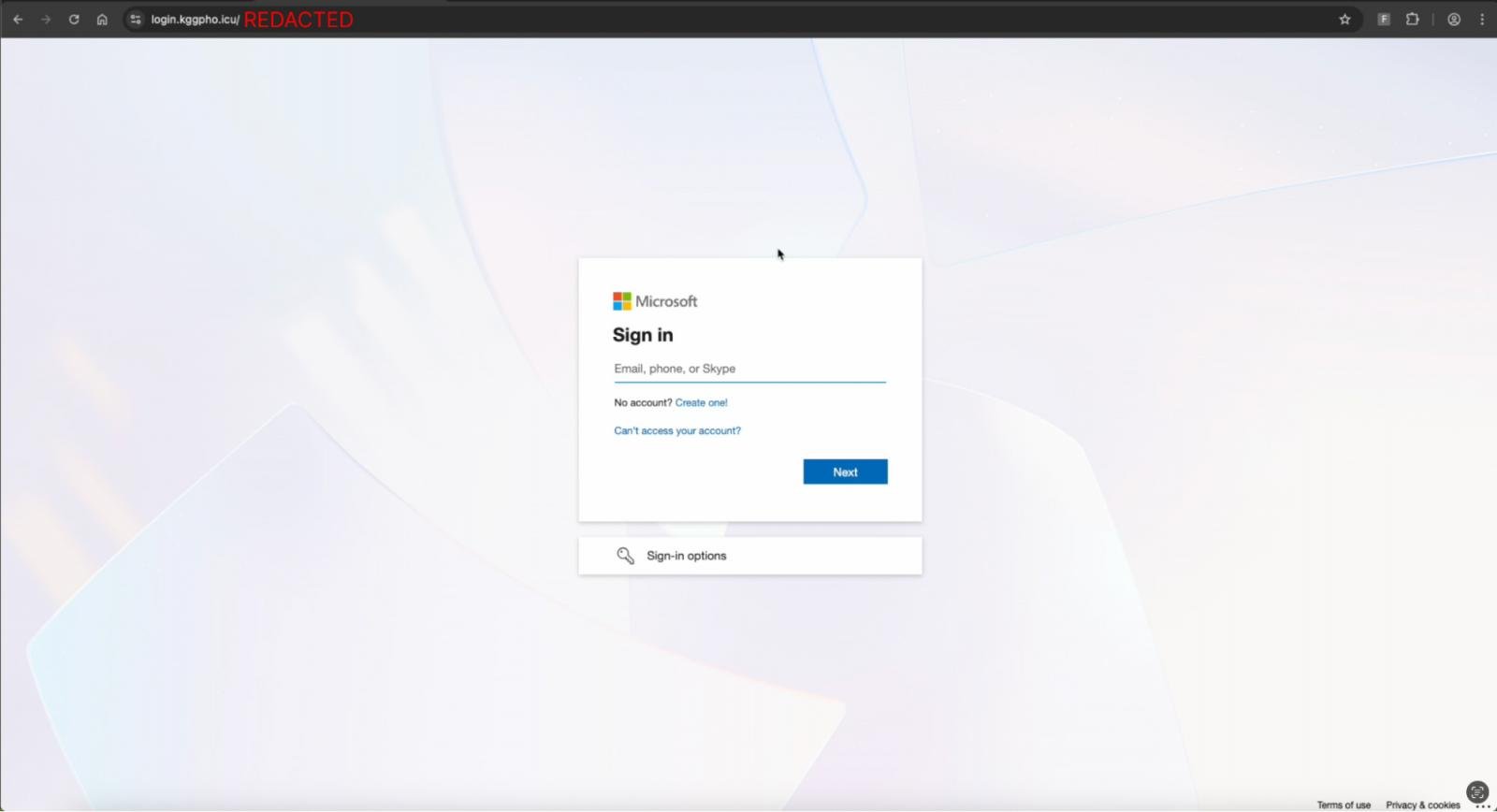
Push Security reports that this button redirects users again, this time to login.kggpho[.]icu, where a Cloudflare Turnstile captcha appears. The attackers use this step to block automated scanners before loading a fake Microsoft login page.
“Attackers are using common bot protection technologies like CAPTCHA and Cloudflare Turnstile to prevent security bots from accessing their web pages to be able to analyse them (and therefore block pages from being automatically flagged),” explains Push Security.
“This requires anyone visiting the page to pass a bot check/challenge before the page can be loaded, meaning the full page cannot be analysed by automated tools.”
After completing the Cloudflare Turnstile challenge, the visitor reaches what looks like a genuine Microsoft authentication page. However, it’s actually an Adversary-in-the-Middle (AITM) phishing page designed to steal both credentials and session cookies.
Phishing page capturing Microsoft credentials
Source: Push Security
Push Security notes that phishing increasingly happens outside traditional email channels, shifting instead to online platforms where users communicate more frequently.
“Phishing isn’t just happening in email anymore,” said Jacques Louw, Chief Product Officer at Push Security. “Over the past month, about 34% of the phishing attempts we’ve tracked have come through places like LinkedIn and other non-email channels — up from under 10% three months ago. Attackers are getting smarter about where people actually communicate and how to effectively target them — and defenders need to keep up.”
Over the past six weeks, Push Security has tracked two separate phishing campaigns on LinkedIn targeting executives. The first, detected in September, focused on technology executives, while the latest one targets finance professionals.
To stay safe, users should treat unexpected LinkedIn messages that offer business opportunities or board invitations with extreme caution. They should avoid clicking any shared links in direct messages and always verify the sender’s identity and the legitimacy of the offer before responding.
Because many phishing campaigns rely on domains with unusual top-level domains (TLDs) such as .top, .icu, and .xyz, users should consider links with these extensions suspicious and avoid them whenever possible.
Source: BleepingComputer, Lawrence Abrams
Read more at Impreza News