Security researchers at Red Canary, a US developer of information security, discovered almost 30,000 infected Macs with a new mysterious, silent and hitherto harmless malware. The “Silver Sparrow”, as it was baptized, was discovered in the beginning of February this year.
The mysterious malware caught the attention of researchers, Firstly, for not offering any threat to the user, that is, without any malicious “payload”. In addition, it runs natively on Apple’s new Mac models, equipped with M1 processors, manufactured by Arm.
Another mysterious feature of Silver Sparrow is that it was developed with a “killer switch”, a complete self-removal mechanism, feature normally used in more elaborate campaigns. In addition, it uses the MacOS Installer’s JavaScript API to execute commands, which makes investigation difficult.
According to the researchers, who are monitoring the 29,139 infected Macs, no action by cybercriminals has yet been noticed, not even an exchange of data involving the malicious application. The researchers fear that these viruses could come into play in a massive way, from an unknown condition.
“Red Canary’s detection engineers have found a malware strain for macOS […] This malware, whatever it may be, did not exhibit the behaviors we expect from conventional malware […] Mainly because of the way it uses JavaScript for execution – something we had not previously found in other macOS malware – and the emergence of a related binary compiled for Apple’s new M1 ARM64 architecture, “writes Red Canary researchers.
“In addition to the mystery of the payload, Silver Sparrow includes a file check that causes the removal of all persistence mechanisms and scripts. It checks for the presence of ~ / Library /._ insu on the disk and, if the file is present , Silver Sparrow removes all its components from the terminal. The presence of this feature is also a mystery “, they write.
Curious behavior
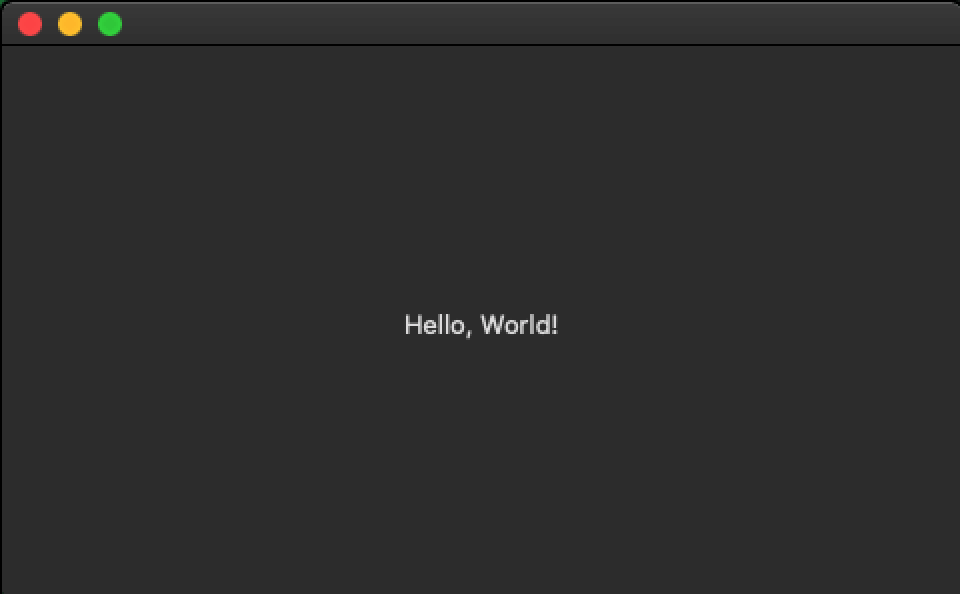
Curious behavior is not lacking in Silver Sparrow. The researchers identified that when the malware runs on older Macs, equipped with Intel processors, it displays a black screen, with the classic message: “Hello, World!” and nothing else.
In the newer Macs, equipped with M1 processors, developed internally by Apple and manufactured by Arm, the malware displays an orange screen, with the text “You did it!” (you did it, in portuguese). Which generated even more doubts.
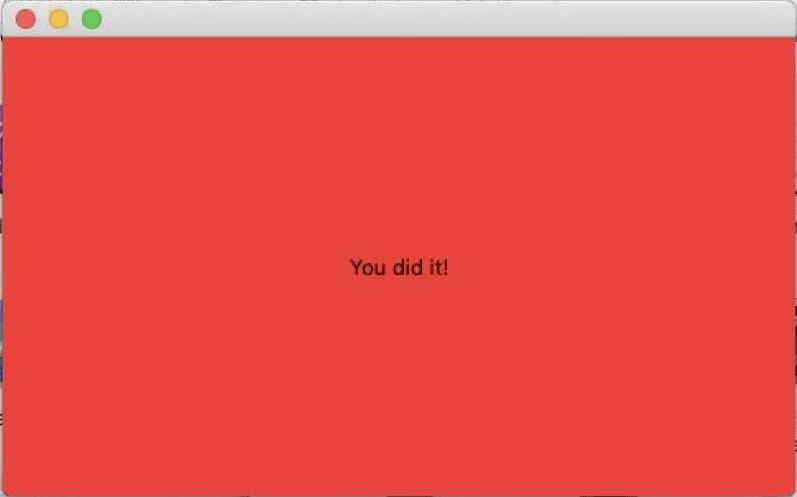
“The first version of the Silver Sparrow malware we reviewed contained a strange Mach-O binary, compiled for Intel x86_row that appeared to play no additional role in execution, simply [uma mensagem]: ‘Hello, World!’ […] The second version also included a strange Mach-O binary that was compiled to be compatible with Intelx86_64 and M1 ARM64. This time, displaying the message: ‘You dit it!’ ”, They write.
How to know if you have been infected
The researchers note that the procedure for detecting Silver Sparrow on a Mac is very similar to the procedure for detecting other malware for macOS. “These analyzes help us to find several families of malware for macOS”, they explain.
To detect Silver Sparrow, look for a process called “PlistBuddy”, then look for a command containing “LaunchAgents; RunAtLoad; true ”in the same sentence. Then, look for a process with a name similar to “sqlite3” running together with a command containing “LSQuarantine”. Finally, look for a process “that appears to be running curl together with a command line that contains: s3.amazonaws.com”.
Source: Red Canary.
See the original post at: https://thehack.com.br/malware-misterioso-encontrado-em-30-mil-macs-confunde-pesquisadores-de-seguranca/?rand=48873