State-sponsored hackers linked to the Silk Typhoon activity cluster actively targeted diplomats by hijacking web traffic and redirecting it to a malware-serving website.
These hackers employed an advanced adversary-in-the-middle (AitM) technique to take control of the captive portal of the network, subsequently sending the target to the first-stage malware.
The Google Threat Intelligence Group (GTIG) tracks this threat actor as UNC6384. Based on their tooling, targeting, and infrastructure, they believe that the Chinese threat actor TEMP.Hex, also known as Mustang Panda and Silk Typhoon, is associated with it.
Hijacking Chrome requests
GTIG researchers believe that the AitM attack became possible after compromising an edge device on the target network; however, they did not find evidence to support this theory.
The attack begins when the Chrome browser checks whether it is behind a captive portal, which is a web page where users authenticate before connecting to the internet.
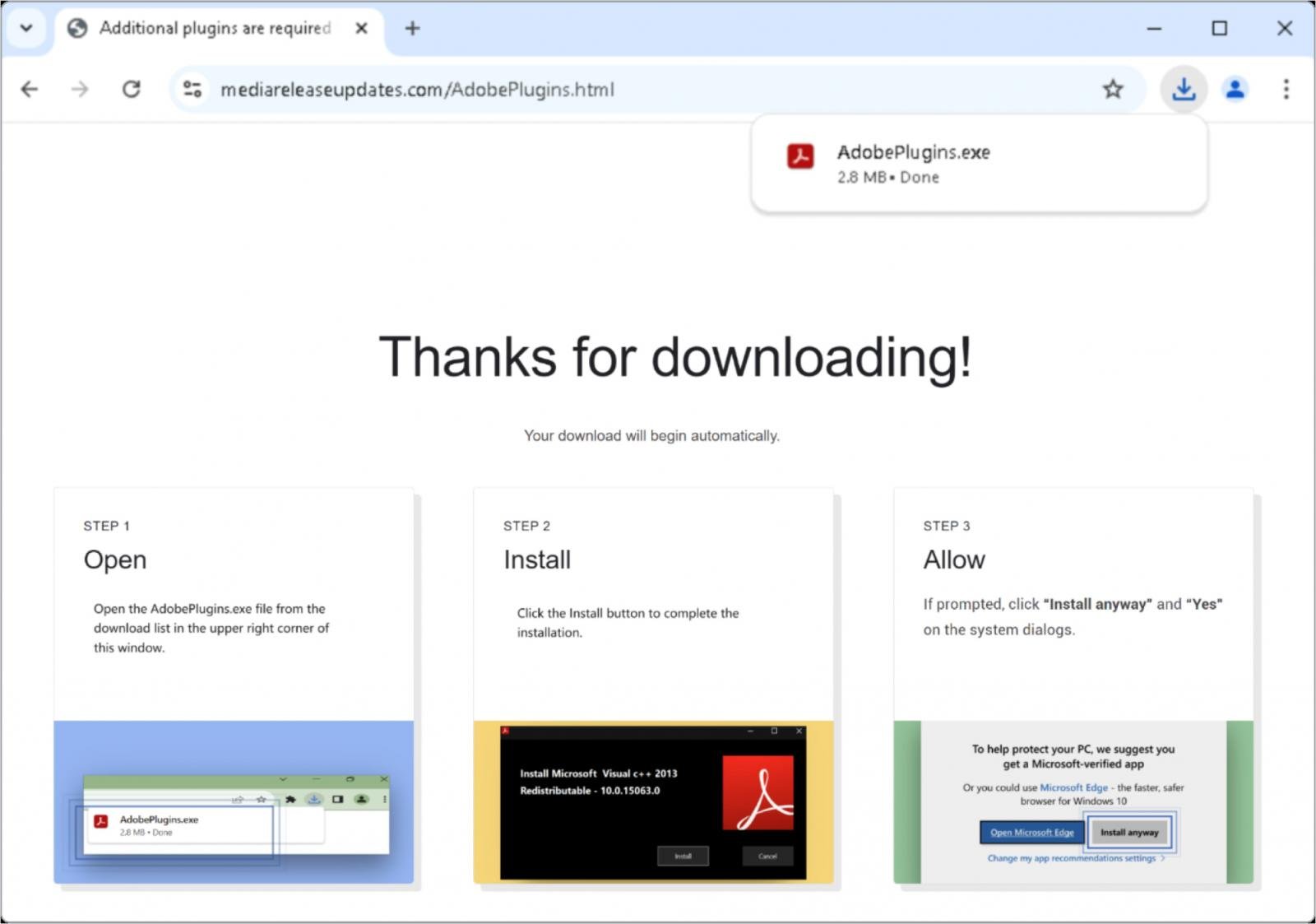
With the hackers positioned to hijack web traffic, they redirect the target to a landing page that impersonates an Adobe plugin update site.
Victims download a digitally signed ‘AdobePlugins.exe’ file, presented as a necessary plugin update, and receive step-by-step instructions on the site to bypass Windows security prompts during installation.
Fake site prompting Adobe plugin installation
Source: Google
When victims launch that file, it displays a Microsoft Visual C++ installer, but it secretly downloads a disguised MSI package (20250509.bmp) containing a legitimate Canon printer tool, a DLL (CANONSTAGER), and the SOGU.SEC backdoor in RC-4 encrypted form.
The DDLs
CANONSTAGER decrypts and loads the final payload into the system memory using the DLL side-loading technique.
SOGU.SEC, which Google identifies as a variant of the PlugX malware extensively used by multiple Chinese threat groups, can collect system information, upload or download files, and provide operatives with a remote command shell.
Overview of the attack chain
Source: Google
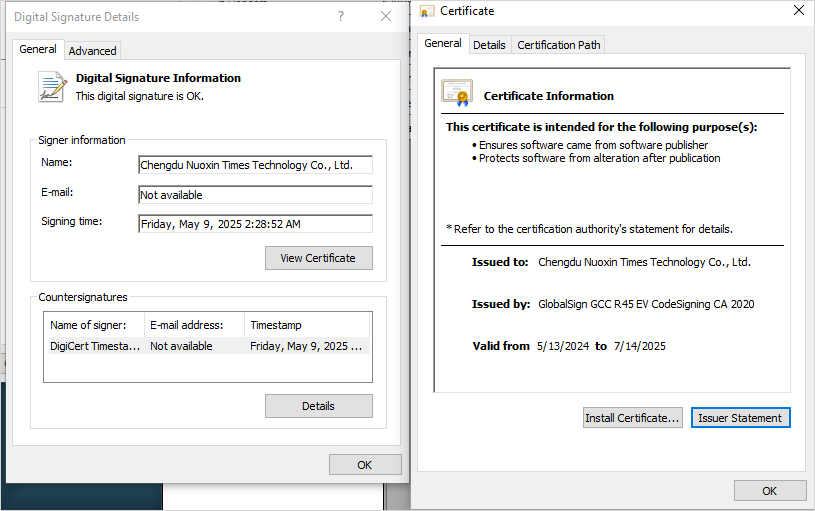
The GTIG researchers noted that it remains unclear whether the entity that signs the files used in this campaign, Chengdu Nuoxin Times Technology Co., Ltd, knowingly participates in these operations or has been compromised.
Nevertheless, GTIG tracks at least 25 malware samples signed by this entity since early 2023, and these samples associate with various Chinese activity clusters.
Treating all certificates from Chengdu Nuoxin Times Technology Co., Ltd as untrusted represents a reasonable defensive action until the situation is clarified.
Certificate used in the latest Mustang Panda campaign
Source: Google
Google has blocked the malicious domains and file hashes via Safe Browsing and issued government-backed attacker alerts to affected Gmail and Workspace users.
Additionally, the tech giant has shared YARA rules for detecting STATICPLUGIN and CANONSTAGER, along with indicators of compromise (IoCs) for all files sampled from these attacks.
This latest campaign indicates the increasing sophistication of Chinese-nexus espionage actors, who are very likely to switch to new infrastructure and binary builds, allowing them to rebound quickly.
Source: BleepingComputer, Bill Toulas
Read more at Impreza News
















.jpg)