A malware campaign employs an unusual tactic of trapping users in their browser’s kiosk mode, pressuring them to input their Google credentials, which are subsequently stolen by information-stealing malware.
The malware locks the user’s browser on Google’s login page, disabling the “ESC” and “F11” keys to prevent closing the window. This tactic aims to frustrate the user into saving their Google credentials in the browser, believing it will “unlock” their computer.
Once the credentials are saved, the StealC information-stealing malware extracts them from the credential store and transmits them to the attacker.
Kiosk mode theft
OALABS researchers, who uncovered this unusual attack method, report that it has been active in the wild since at least August 22, 2024. The attack is primarily carried out by Amadey, a malware loader, info-stealer, and system reconnaissance tool initially deployed by hackers in 2018.
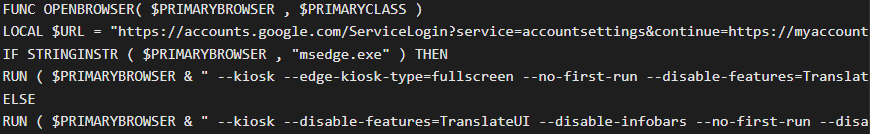
When executed, Amadey deploys an AutoIt script that functions as a credential flusher. The script scans the infected system for browsers and launches one in kiosk mode to a specific URL.
Script part that launches Chrome or Edge in kiosk mode, on a Google login URL
Source: OALABS
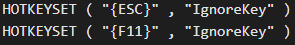
Additionally, the script disables the F11 and Escape keys on the browser, preventing the user from easily exiting kiosk mode.
Ignoring presses of F11 and Esc keys
Source: OALABS
Kiosk mode, typically used in web browsers or applications to display content in full screen without standard UI elements like toolbars or navigation buttons, is intended to limit user interactions, making it ideal for public terminals and demonstration displays.
In this case, however, Amadey exploits kiosk mode to trap users on a login page, with the only visible option being to enter their account credentials.
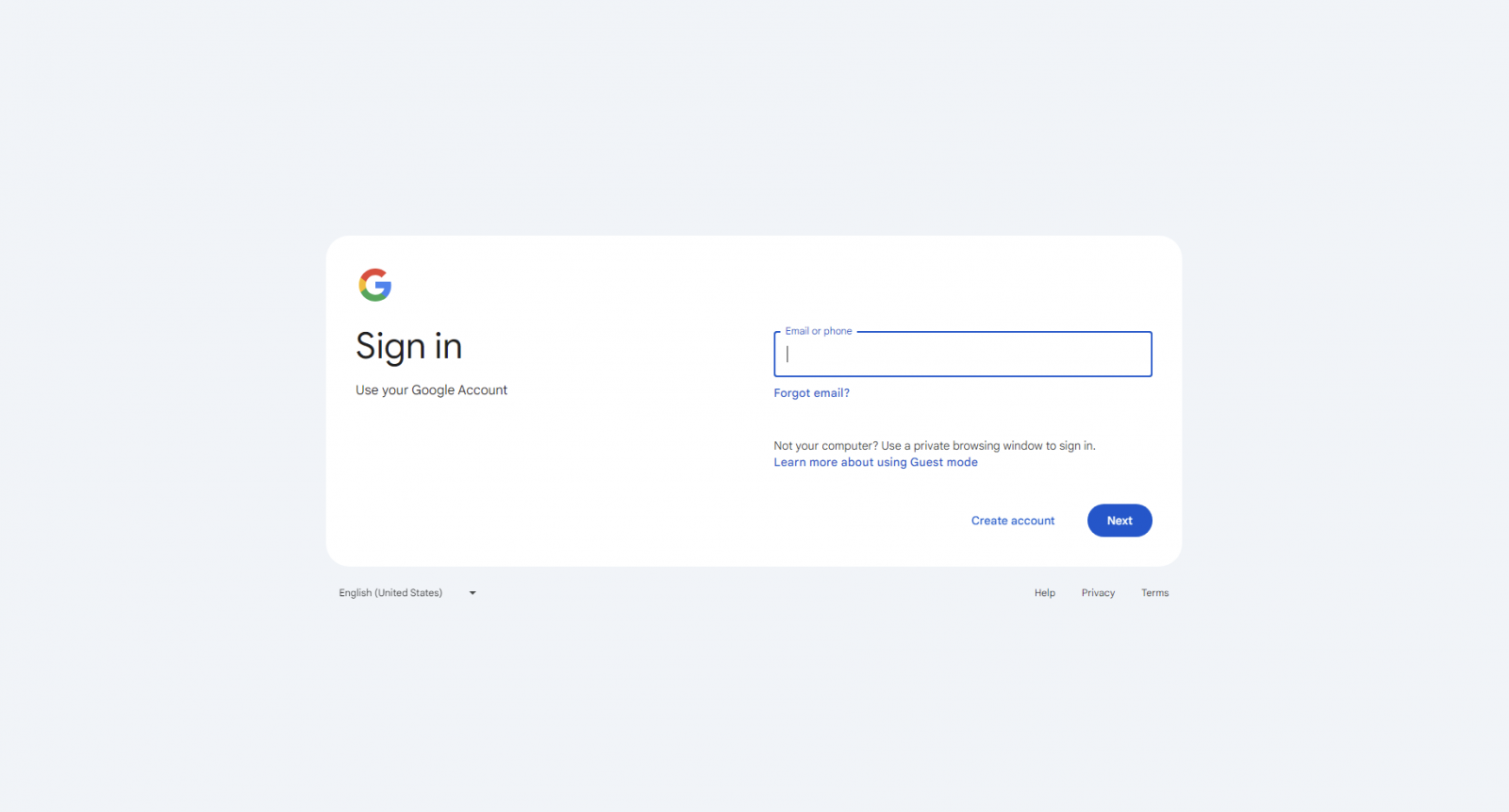
The browser is directed to https://accounts.google.com/ServiceLogin?service=accountsettings&continue=https://myaccount.google.com/signinoptions/password, the change password URL for Google accounts.
Since Google requires users to reenter their password before any changes, the attack creates an opportunity for users to reauthenticate and potentially save their credentials in the browser when prompted.
What the victim sees on their computer
Source: OALABS
Any credentials entered and saved are then stolen by StealC, a lightweight and versatile information-stealing malware launched in early 2023.
Exiting the kiosk mode
If you find yourself locked in kiosk mode with the Esc and F11 keys unresponsive, it’s important to stay calm and avoid entering any sensitive information into forms.
Instead, try alternative hotkey combinations such as ‘Alt + F4,’ ‘Ctrl + Shift + Esc,’ ‘Ctrl + Alt + Delete,’ or ‘Alt + Tab.’
These shortcuts may help bring the desktop to the foreground, switch between open apps, or launch the Task Manager to terminate the browser (End Task).
You can also try pressing ‘Win Key + R‘ to open the Run dialog. From there, type ‘cmd’ to open the command prompt and use the command ‘taskkill /IM chrome.exe /F’ to force close Chrome.
If these methods fail, performing a hard reset by holding the Power button until the computer shuts down is an option. While unsaved work may be lost, it’s preferable to having your account credentials compromised.
After rebooting, press F8 to enter Safe Mode, and once you’re back in the operating system, run a full antivirus scan to detect and remove the malware. Unexpected kiosk mode browser behavior is a red flag and should not be ignored.
Source: BleepingComputer, Bill Toulas