The Glassworm campaign, which first emerged on the OpenVSX and Microsoft Visual Studio Marketplaces in October, now enters its third wave, and attackers introduce 24 new packages on both platforms.
Understanding the Affected Marketplaces
OpenVSX and the Microsoft Visual Studio Marketplace are both extension repositories for VS Code–compatible editors, and developers use them to install language support, frameworks, tooling, themes, and other productivity add-ons.
Furthermore, the Microsoft marketplace serves as the official platform for Visual Studio Code, while OpenVSX operates as an open, Vendor-neutral alternative for editors who can’t or don’t use Microsoft’s proprietary store.
How Glassworm Works
First documented by Koi Security on October 20, Glassworm is a malware that uses “invisible Unicode characters” to hide its code from review.
After developers install it in their environments, it attempts to steal GitHub, npm, and OpenVSX accounts, as well as Cryptocurrency wallet data from 49 extensions.
Moreover, the malware deploys a SOCKS proxy to route malicious traffic through the victim’s machine and installs the HVNC client to give operators Stealthy remote access.
Although teams removed the initial infection from the extension repositories, the malware quickly returned to both sites with new extensions and publisher accounts.
Prior to this, Open VSX declared the incident fully contained, and the platform rotated compromised access tokens.
New Findings From Researchers
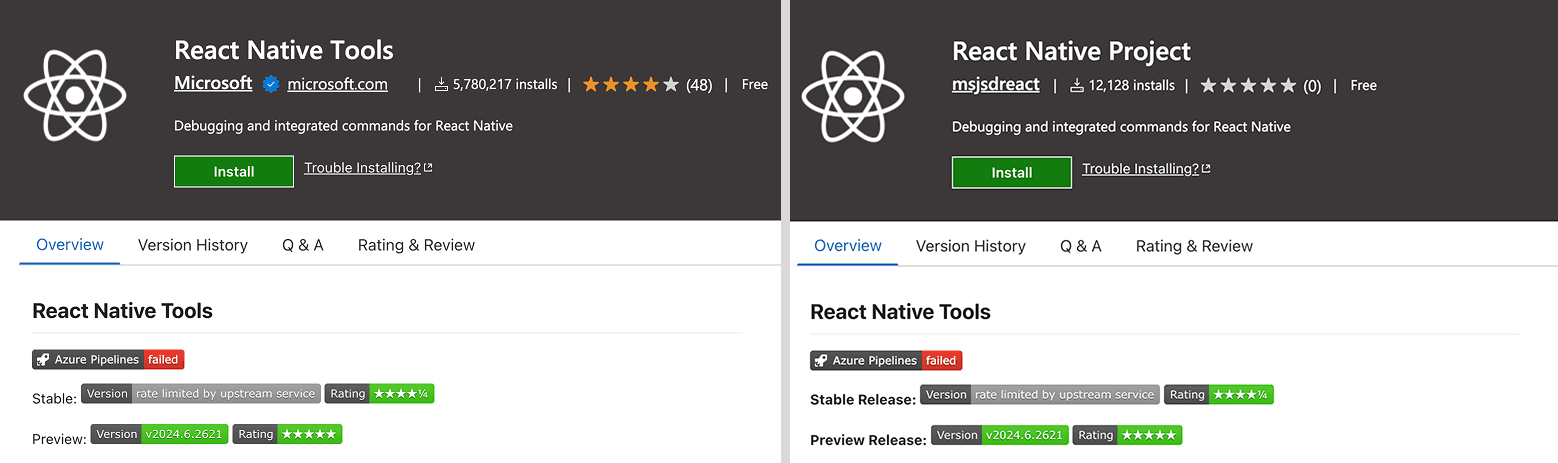
The re-emergence of Glassworm surfaced when Secure Annex’s researcher, John Tuckner, discovered it. He reports that the package names indicate a broad targeting scope covering popular tools and developer frameworks like Flutter, Vim, Yaml, Tailwind, Svelte, React Native, and Vue.
Legitimate (left) and impersonator (right) packages
Source: Secure Annex
Secure Annex now confirms that the third wave uses the packages listed below.
VS Marketplace Packages:
- iconkieftwo.icon-theme-materiall
- prisma-inc.prisma-studio-assistance
- prettier-vsc.vsce-prettier
- flutcode.flutter-extension
- csvmech.csvrainbow
- codevsce.codelddb-vscode
- saoudrizvsce.claude-devsce
- clangdcode.clangd-vsce
- cweijamysq.sync-settings-vscode
- bphpburnsus.iconesvscode
- klustfix.kluster-code-verify
- vims-vsce.vscode-vim
- yamlcode.yaml-vscode-extension
- solblanco.svetle-vsce
- vsceue.volar-vscode
- redmat.vscode-quarkus-pro
- msjsdreact.react-native-vsce
Open VSX Packages:
- bphpburn.icons-vscode
- tailwind-nuxt.tailwindcss-for-react
- flutcode.flutter-extension
- yamlcode.yaml-vscode-extension
- saoudrizvsce.claude-dev
- saoudrizvsce.claude-devsce
- vitalik.solidity
How the Attackers Boost Credibility
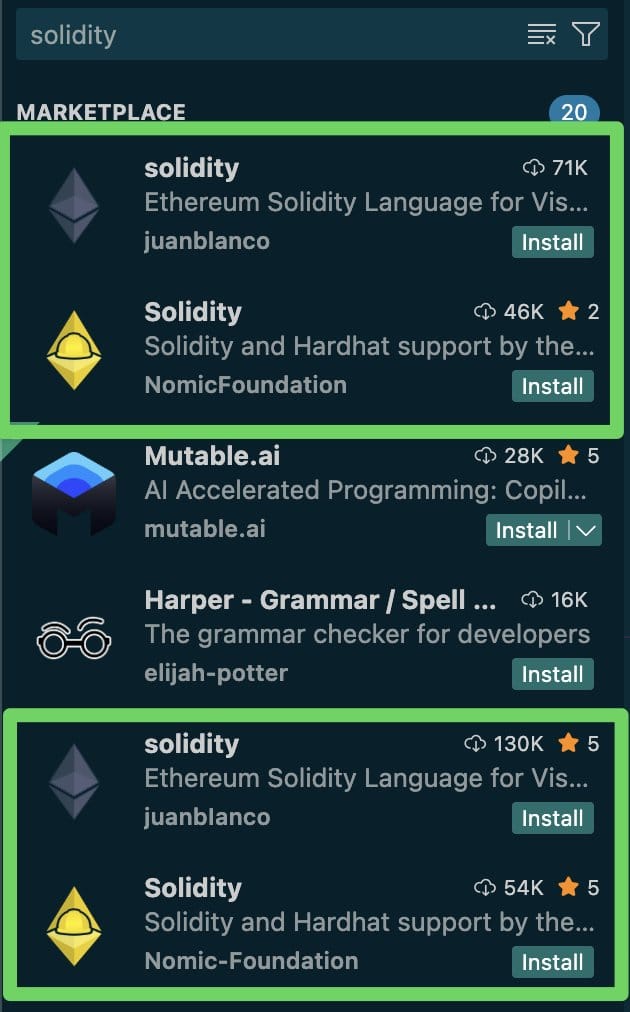
Once the packages reach the marketplaces, the publishers push an update that introduces the Malicious code, then inflate their download counts to make them appear legitimate and Trustworthy.
Additionally, Artificially increasing download counts manipulates search results, placing the Malicious extension higher—often very close to the legitimate projects it impersonates.
Confusing search results
Source: Secure Annex
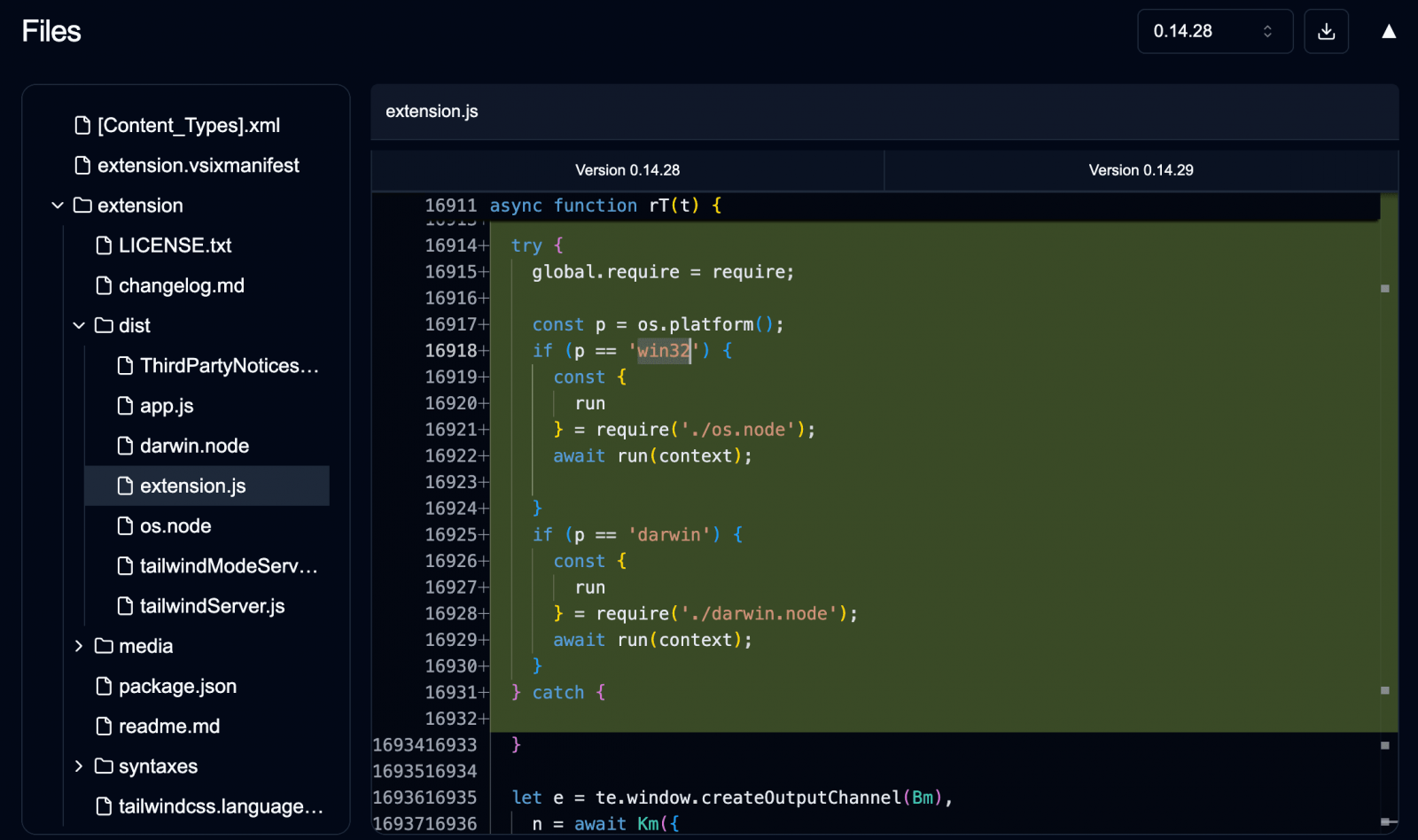
The researcher reports that Glassworm has evolved on the technical side as well, now using Rust-based Implants Packaged inside the extensions. The invisible Unicode trick also remains in use in some cases.
Payload
Source: Secure Annex
BleepingComputer has contacted both OpenVSX and Microsoft regarding Glassworm’s continued ability to bypass their defenses, and we will update this post with their responses once received.
Update 12/2 – Microsoft sent BleepingComputer the following statement:
“We continue to assess and improve our scanning and detections to prevent abuse. Microsoft encourages users to flag suspicious content through a “Report Abuse” link found on every extension page.”
Source: BleepingComputer, Bill Toulas
Read more at Impreza News