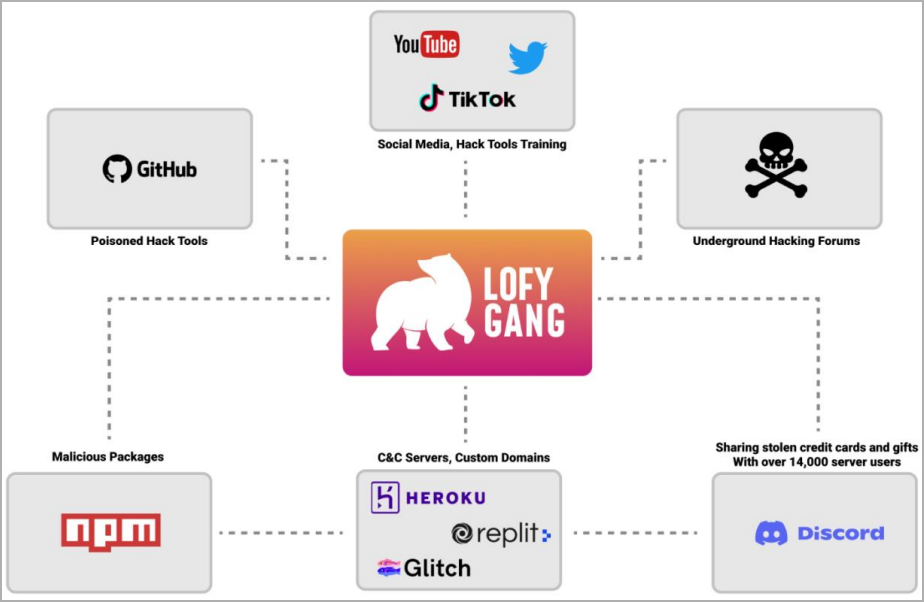
The ‘LofyGang’ threat actors have created a credential-stealing enterprise by distributing 200 malicious packages and fake hacking tools on code hosting platforms, such as NPM and GitHub.
Researchers highlighted some of these packages in recent reports by Kaspersky, Jfrog, and Sonatype, who spotted them in supply chain attacks using typo-squatted package names.
Many of the malicious packages have been reported and removed, while others are still available for download at the time of writing this. There’s even a dedicated project to search for and track malicious LofyGang packages on GitHub.
A new report by Checkmarx attempts to map LofyGang’s operation and provide a clear and broad perspective on the threat actor’s goals, size, and actual impact.
Overview of LofyGang’s online presence (Checkmarx)
A large-scale credential theft operation
By observing the threat group’s extensive online presence, Checkmarx deduced that they are interested in stealing credit card data, Discord “Nitro” credentials, and streaming and gaming services accounts, such as Disney+ and Minecraft.
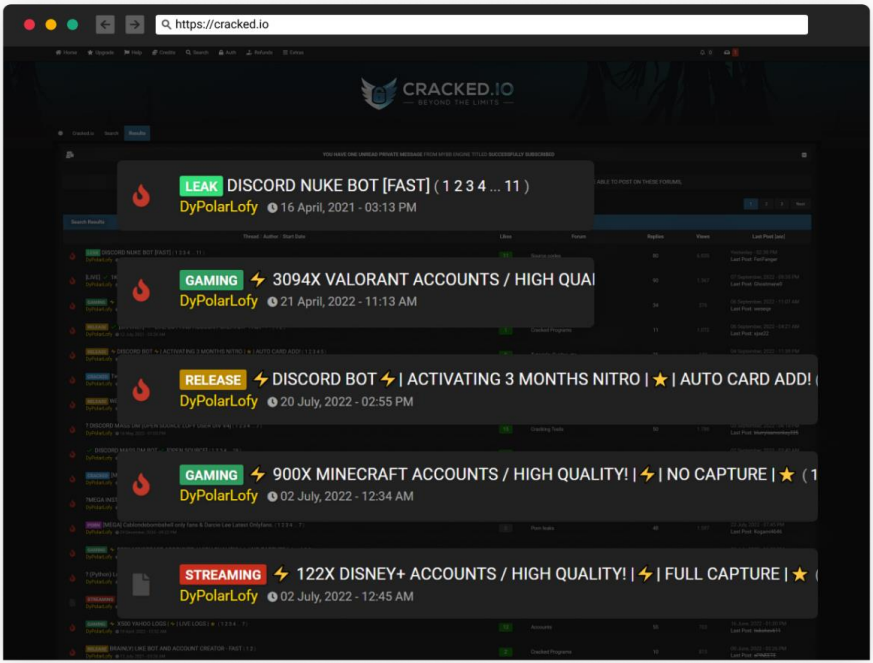
Hence, LofyGang is motivated by financial profit, aiming to achieve high-volume account compromise and then resell access to those accounts on various private channels on the dark web, hacking forums, and Discord.
The gang selling compromised accounts on hacking forums (Checkmarx)
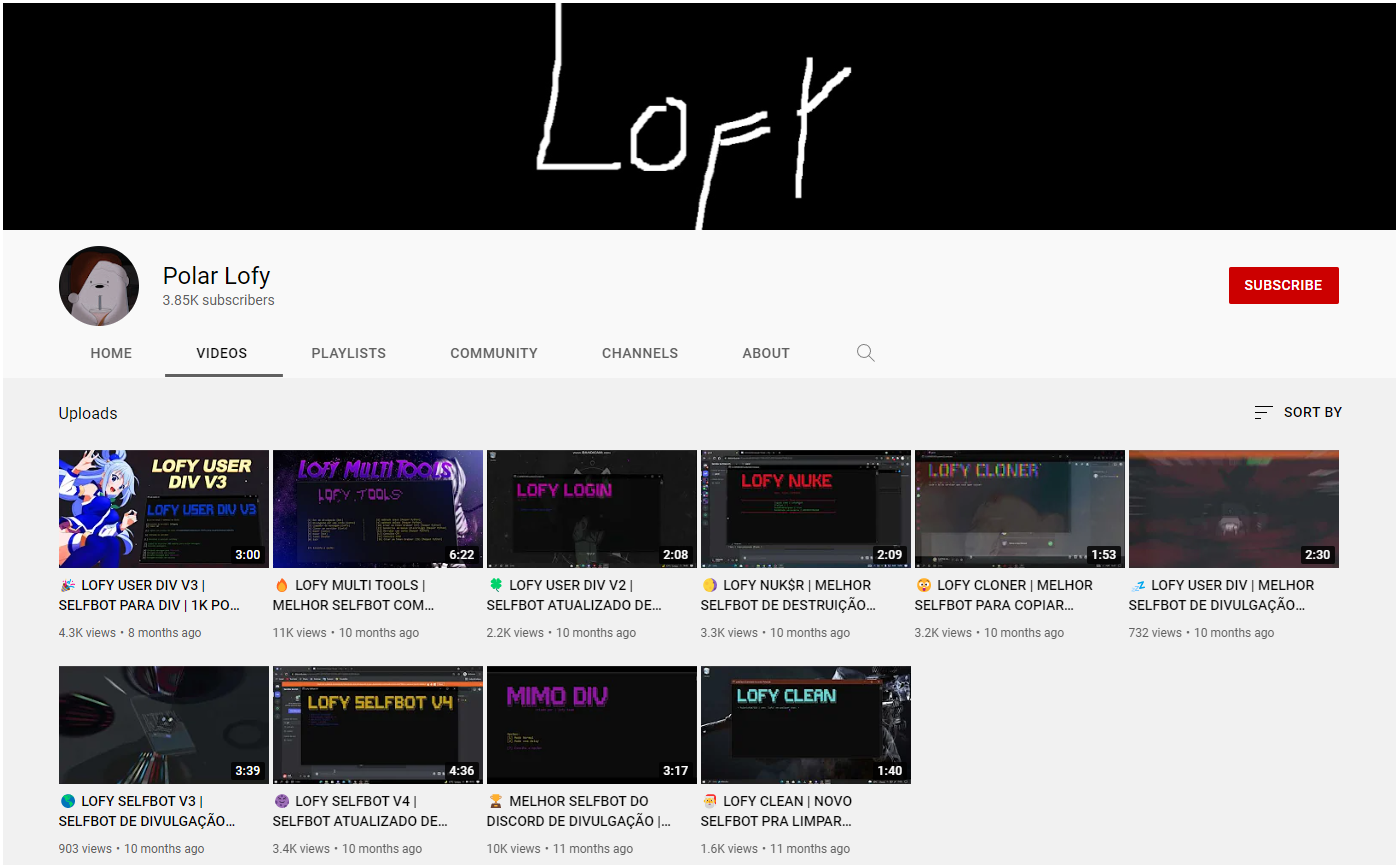
The group also operates a YouTube channel hosting video tutorials on how to use its hacking tools, with two having surpassed 10k views.
LofyGang’s YouTube channel
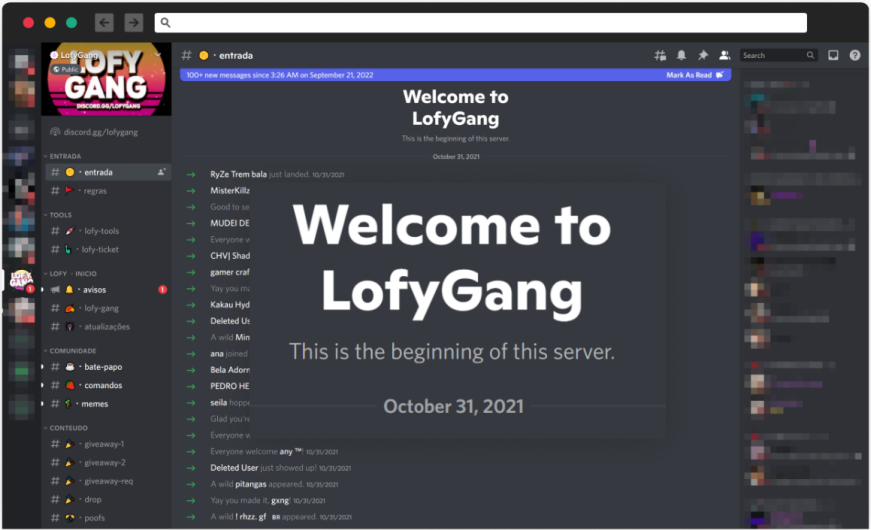
The Discord channel was created a year ago, offering guidance and support to the group’s hacking tool operators, holding promotional Discord Nitro giveaways, and more.
LofyGang’s Discord channel (Checkmarx)
A bot on Discord, named “Lofy Boost,” can be used by channel members to purchase Nitro using a stolen credit card on behalf of the user. The bot also receives user tokens, which the crooks may abuse later.
The stash of the stolen credit cards comes from NPM supply chain infections and by pushing laced and backdoored hacking tools on GitHub, which less skilled cybercriminals grab and use free of charge.
Many of the NPMs impersonate Discord development packages or packages for color, strings, and file operations. The free hacking tools are promoted on forums where hackers tend to congregate and learn from each other.
Some of the tools promoted by the gang on GitHub are a Discord spammer, a Nitro generator, a password stealer, a Discord token grabber, and a Discord webhook hiding module.
GitHub repository pushing hacking tools
LofyGang’s main Discord malware modifies the legitimate version of the Discord app on the infected system with a malicious version that siphons credit card information every time the user pays for a subscription.
In most cases, the malware isn’t included in the main package. Instead, it is fetched as a dependency, so the operators of their tools are less likely to realize they got scammed, and the hosting platforms won’t remove them.
Additionally, LofyGang uses over 50 accounts to upload NPM packages, fragmenting their malicious operation as much as possible to evade large-scale takedowns.
For a complete list of the packages that should be avoided/removed, Checkmarx compiled a list of GitHub.
Source: BleepingComputer