Several prominent open-source projects, including those from tech giants like:
- Google,
- Microsoft,
- AWS,
- and Red Hat,
were discovered to be leaking GitHub authentication tokens via GitHub Actions artifacts in their CI/CD workflows.
If exploited, these stolen tokens could grant attackers unauthorized access to private repositories. Thus allowing them to steal source code or inject malicious code into critical projects.
This alarming discovery, made by Palo Alto Networks’ Unit 42, spurred action among repository owners whose secrets were exposed through GitHub Actions artifacts. Despite this, GitHub has chosen not to resolve the root issues, instead leaving the responsibility on users to safeguard their artifacts.
In light of these developments, GitHub users must:
- assess their vulnerabilities,
- recognize the potential risks,
- and implement preventative measures to avoid future leaks.
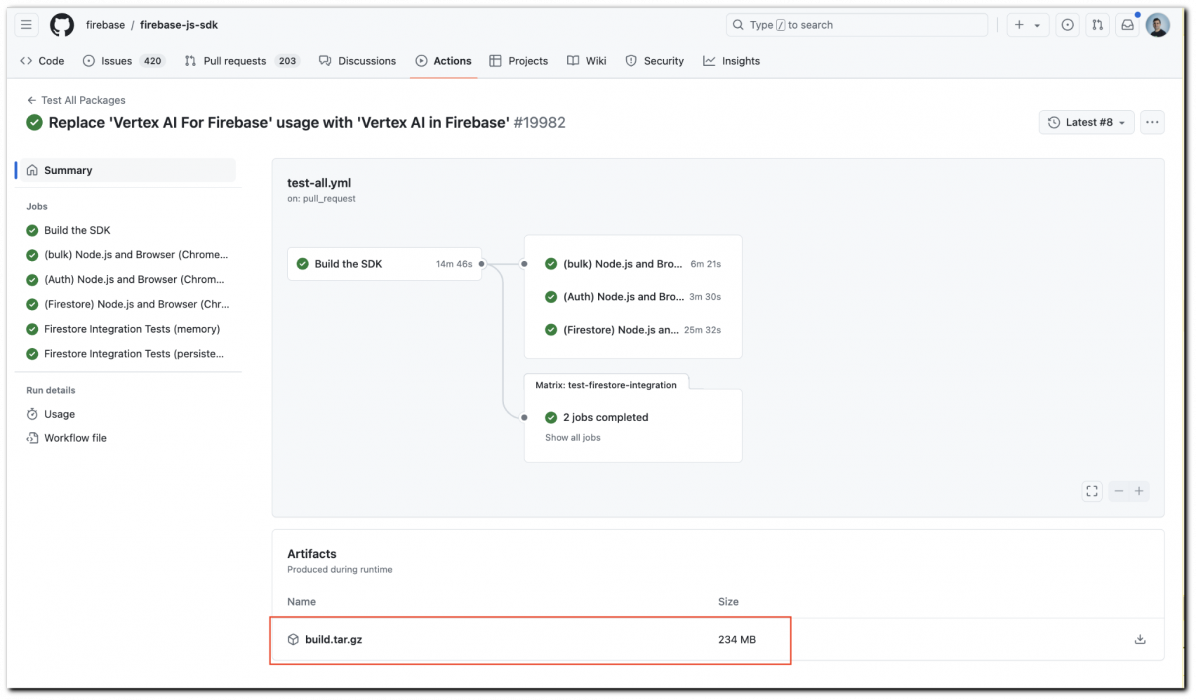
Artifact generated by GitHub Actions
Source: Unit 42
Leaking GitHub tokens
Unit 42’s report underscores a convergence of issues—ranging from insecure default settings and user misconfigurations to weak security checks—that can result in GitHub token leaks in what they term an “ArtiPACKED” attack.
A key vulnerability lies within the widely used ‘actions/checkout’ action, which allows GitHub workflows to clone repository code for use during workflow execution.
By default, this action saves the GitHub token to the local hidden .git directory, facilitating authenticated operations throughout the workflow.
However, if users mistakenly include the entire checkout directory in an artifact upload, the token stored within the git folder could be inadvertently exposed.
Publicly exposed GitHub token
Source: Unit 42
Alongside the token, other sensitive data such as API keys, cloud service access tokens, and account credentials might also be revealed in the process.
Similar risks arise when artifacts created during CI/CD workflows—like build outputs or test results—are improperly handled and stored. These artifacts remain accessible for up to three months, potentially exposing sensitive information.
Additionally, CI/CD pipelines that rely on environment variables to store GitHub tokens are vulnerable if these variables are logged during workflows, either intentionally or by accident. When logs are uploaded as artifacts, tokens can be exposed.
Unit 42 also highlights the ‘super-linter‘ action, which can generate detailed logs that include environment variables if the ‘CREATE_LOG_FILE’ property is set to ‘True.’
Exploiting the leakages
Ultimately, attackers aim to exploit specific race conditions, extracting ephemeral GitHub tokens from logs and using them before they expire.
The validity of GitHub tokens is tied to the duration of the workflow job, meaning their exploitation potential varies case by case.
For example, the ‘Actions_Runtime_Token‘, which GitHub uses internally for caching and artifact management, remains valid for around six hours, offering a limited window for exploitation.
In contrast, custom secrets and tokens, such as API keys or cloud service access tokens, have varying lifespans—ranging from a few minutes to indefinitely.
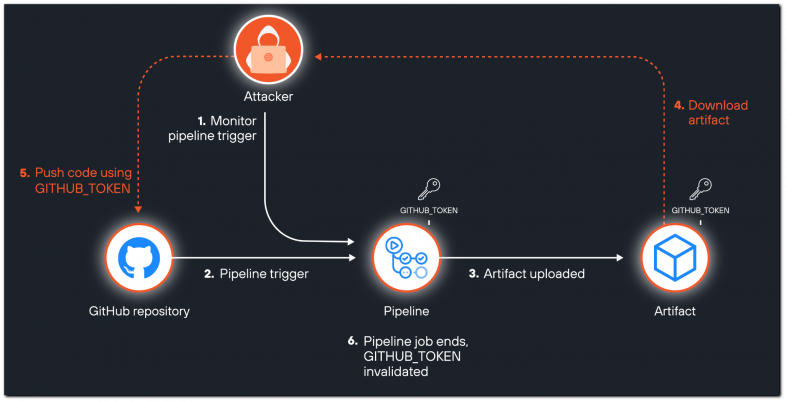
Unit 42 outlines a potential attack scenario in which automated scripts target public repositories or projects utilizing GitHub Actions, scanning them for characteristics that heighten the likelihood of artifact creation.
Another set of scripts could then automatically download artifacts from the CI/CD pipelines of these repositories—a straightforward task in the case of public projects—and search them for sensitive information or secrets.
Attack flow
Source: Unit 42
Mitigation
Unit 42 uncovered 14 instances where large open-source projects had exposed artifacts containing GitHub tokens, and promptly reported these vulnerabilities to the respective organizations for remediation:
- Firebase (Google)
- OpenSearch Security (AWS)
- Clair (Red Hat)
- Active Directory System (Adsys) (Canonical)
- JSON Schemas (Microsoft)
- TypeScript Repos Automation, TypeScript Bot Test Triggerer, Azure Draft (Microsoft)
- CycloneDX SBOM (OWASP)
- Stockfish
- Libevent
- Guardian for Apache Kafka (Aiven-Open)
- Git Annex (Datalad)
- Penrose
- Deckhouse
- Concrete-ML (Zama AI)
To mitigate such risks, GitHub users are advised to avoid uploading entire directories in artifacts, sanitize logs, and consistently review their CI/CD pipeline configurations.
It is also recommended to modify the default settings of actions like ‘actions/checkout‘ to prevent credentials from persisting. Additionally, token permissions within workflows should be configured using the principle of least privilege, minimizing potential damage if tokens are leaked.
Source: BleepingComputer, Bill Toulas
Read other news at our blog