The Internet Archive has experienced another security breach, this time through their Zendesk email support platform, after multiple warnings about threat actors stealing exposed GitLab authentication tokens.
Since last night, BleepingComputer has received numerous reports from individuals who received replies to old Internet Archive removal requests. These messages warned that the organization had been breached due to their failure to properly rotate stolen authentication tokens.
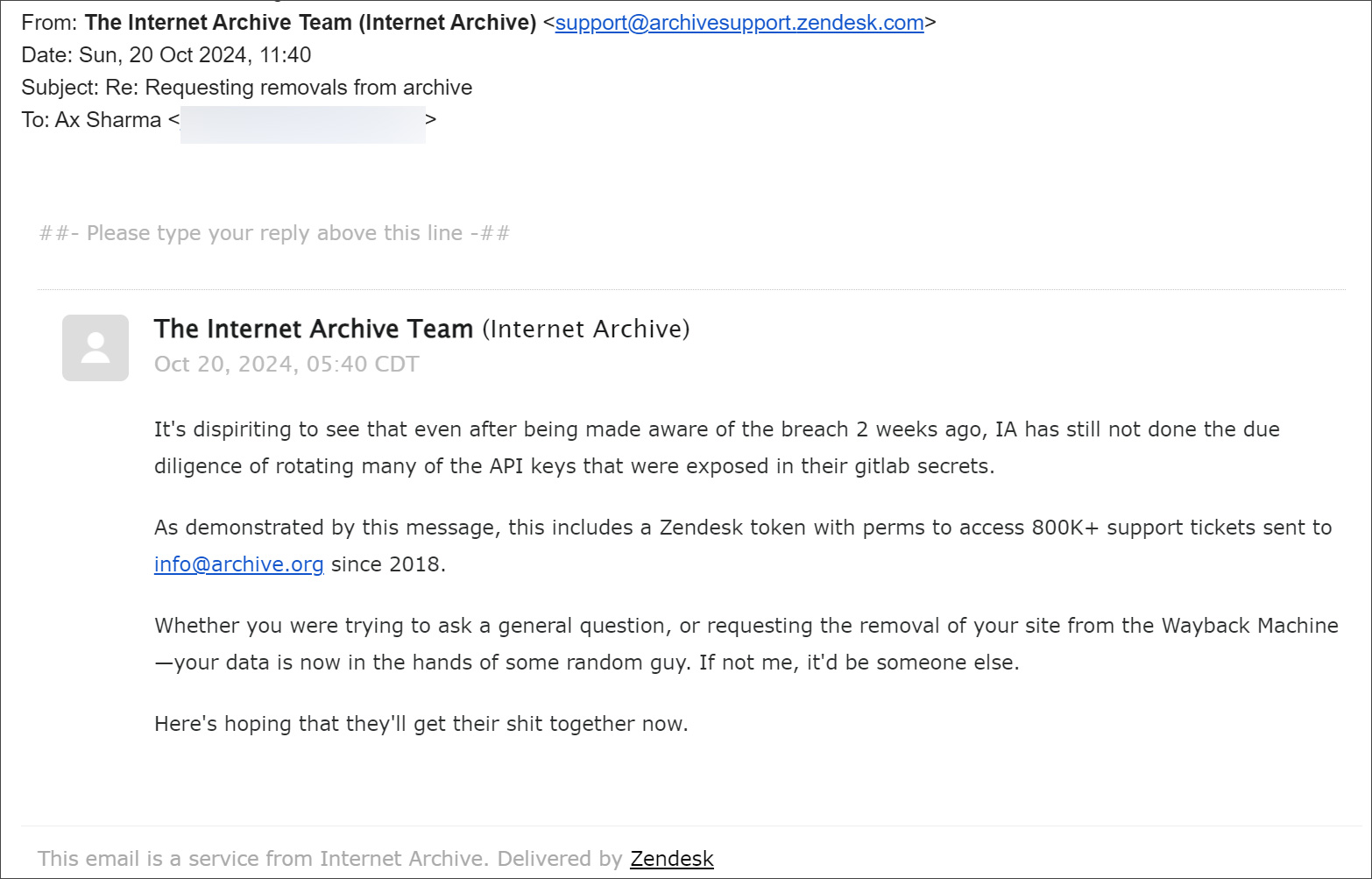
“It’s frustrating to see that, despite being alerted to the breach weeks ago, the Internet Archive has still not rotated many of the API keys exposed in their GitLab secrets,” a threat actor’s email stated.
The email further explained that the stolen credentials included a Zendesk token with permissions to access over 800,000 support tickets sent to info@archive.org since 2018.
“Whether you had a general inquiry or requested the removal of your site from the Wayback Machine, your data is now in the hands of an unauthorized party. If not me, someone else would have gotten it,” the message warned.
Internet Archive Zendesk emails sent by the threat actor
Source: BleepingComputer
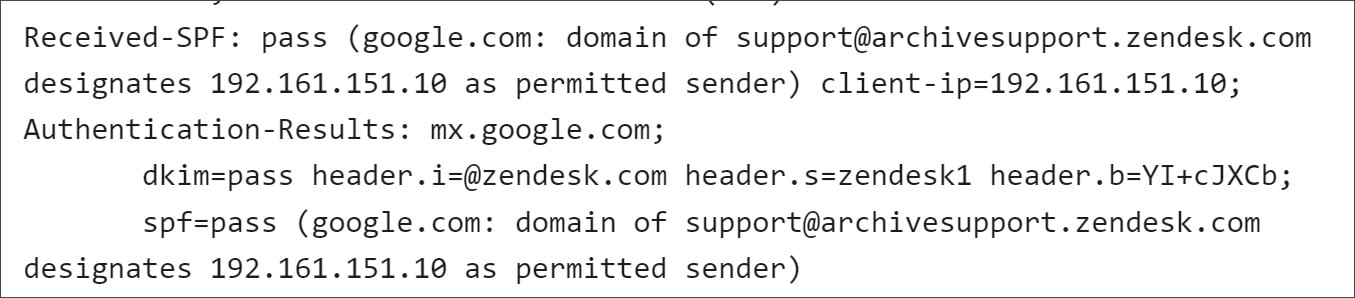
The email headers showed that all DKIM, DMARC, and SPF authentication checks passed, confirming the emails were sent from an authorized Zendesk server at IP address 192.161.151.10.
Internet Archive Zendesk email headers
Source: BleepingComputer
After the story was published, a recipient of the emails informed BleepingComputer that they had uploaded personal identification when requesting a page removal from the Wayback Machine. Depending on the level of API access the attacker had to Zendesk, they may now possess these sensitive attachments as well.
These emails follow repeated attempts by BleepingComputer to warn the Internet Archive that their source code had been stolen via an exposed GitLab authentication token, which had remained online for nearly two years.
Exposed GitLab authentication tokens
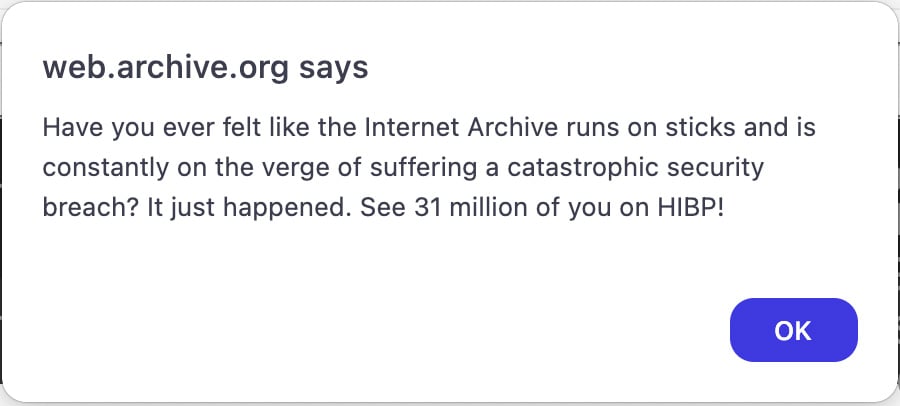
On October 9th, BleepingComputer reported that the Internet Archive was targeted by two separate attacks last week—a data breach that exposed user data for 33 million users, and a DDoS attack carried out by a pro-Palestinian group named SN_BlackMeta.
While the attacks occurred simultaneously, they were executed by different threat actors. However, several media outlets mistakenly reported that SN_BlackMeta was responsible for both the data breach and the DDoS attack, leading to confusion.
JavaScript alert on Internet Archive warning about the breach
Source: BleepingComputer
This misreporting frustrated the hacker behind the data breach, who reached out to BleepingComputer through an intermediary to take credit and clarify how they compromised the Internet Archive.
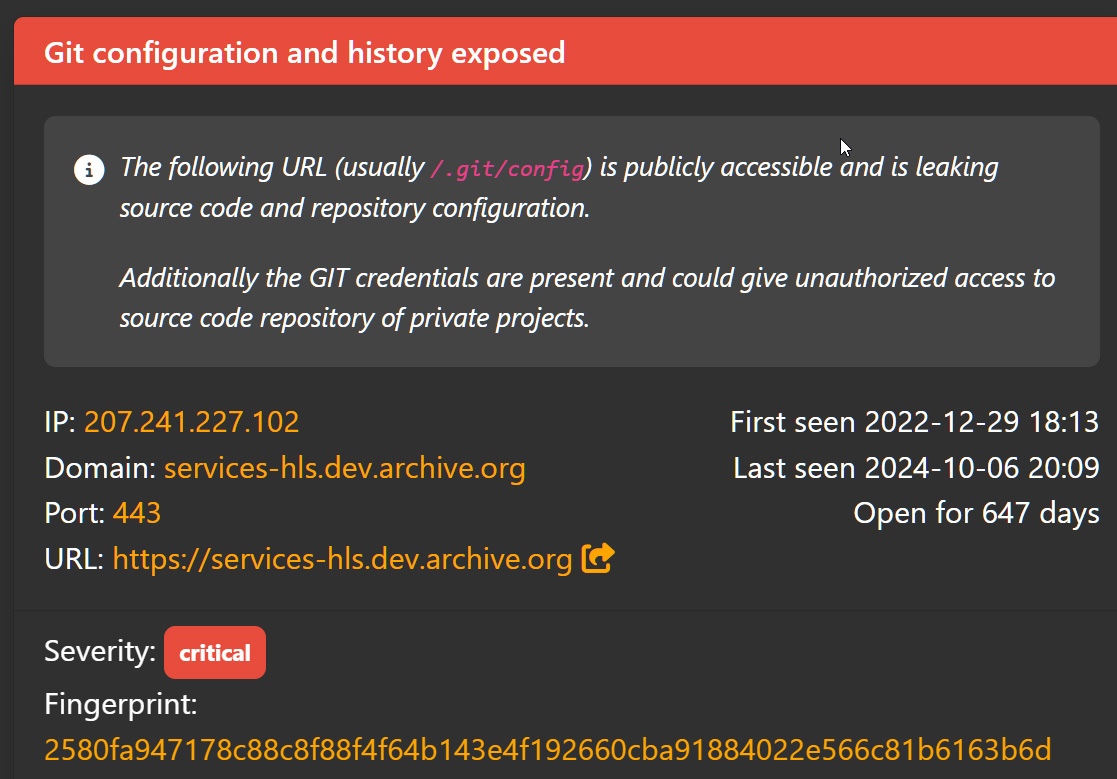
According to the threat actor, the breach began when they discovered an exposed GitLab configuration file on one of the organization’s development servers, services-hls.dev.archive.org.
BleepingComputer verified that this token had been publicly exposed since at least December 2022, and had been rotated several times since then.
Exposed Internet Archive GitLab authentication token
Source: BleepingComputer
The hacker explained that this GitLab configuration file contained an authentication token that granted access to the Internet Archive’s source code.
The source code, in turn, contained additional credentials and authentication tokens, including access to the Internet Archive’s database management system. This allowed the threat actor to download the user database, further source code, and even modify the site.
The hacker claimed to have stolen 7TB of data from the Internet Archive but declined to provide any samples as proof.
It has since been revealed that the stolen data also included API access tokens for the Internet Archive’s Zendesk support system.
Despite BleepingComputer’s repeated efforts to contact the Internet Archive, including as recently as Friday, offering details on how the breach occurred, the organization has not responded.
Breached for cyber street cred
Following the breach of the Internet Archive, conspiracy theories quickly emerged, speculating about who was behind the attack.
Some suggested Israel, the U.S. government, or even corporations embroiled in copyright disputes with the Internet Archive were responsible.
However, the breach did not occur for political or monetary reasons—it simply happened because the hacker had the means to do so.
There exists a vast community of individuals who traffic in stolen data. Some do it for financial gain by extorting victims or selling the information to other cybercriminals, while others collect breaches simply as a hobby.
Often, this stolen data is released for free to boost the hacker’s “cyber street cred,” enhancing their reputation among other threat actors as they compete to execute the most significant, high-profile attacks.
In the case of the Internet Archive, extortion wasn’t the goal, as there was no financial incentive to target the organization. Instead, breaching such a widely recognized and heavily trafficked site served to enhance the hacker’s standing within the community.
Although no one has publicly taken responsibility for this breach, BleepingComputer was informed that it took place during a group chat with other threat actors, many of whom received portions of the stolen data.
This database is now likely being traded among members of the data breach community, and it is anticipated that it will eventually be leaked for free on hacking forums such as Breached.
Source: BleepingComputer, Lawrence Abrams