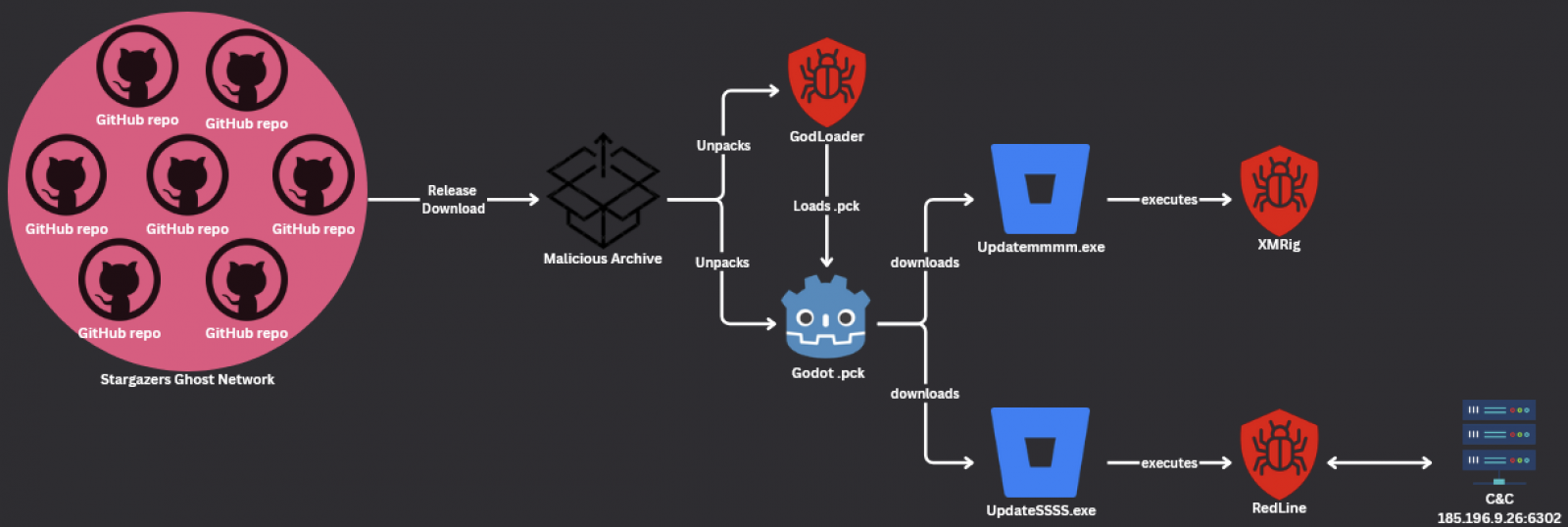
Hackers have deployed the new GodLoader malware, exploiting the features of the widely adopted Godot game engine to bypass detection and compromise over 17,000 systems within three months.
As uncovered by Check Point Research during their analysis, cybercriminals utilize this malware loader to target gamers on all major platforms, including Windows, macOS, Linux, Android, and iOS.
The malware also takes advantage of Godot’s versatility and the scripting capabilities of its GDScript language to execute arbitrary code and evade detection. By embedding harmful scripts into the game engine’s .pck files, which are typically used to package game assets, attackers can disguise their malicious activities.
Once activated, the compromised files execute malicious code on victims’ devices, allowing attackers to steal sensitive credentials or deploy additional payloads, such as the XMRig crypto miner. This miner’s configuration was hosted on a private Pastebin file uploaded in May, which received 206,913 visits throughout the campaign.
“Since at least June 29, 2024, cybercriminals have been exploiting the Godot Engine to execute tailored GDScript code, triggering malicious commands and distributing malware. This method has largely evaded detection by most antivirus tools on VirusTotal, potentially impacting over 17,000 machines in a matter of months,” Check Point reported.
“Godot has a thriving and expanding community of developers who appreciate its open-source nature and robust functionality. Over 2,700 developers have contributed to the engine,” while “platforms like Discord, YouTube, and other social media channels host around 80,000 followers engaged with the latest updates about the Godot engine.”
Attack chain (Check Point)
The attackers distributed the GodLoader malware via the Stargazers Ghost Network, a malware Distribution-as-a-Service (DaaS) platform that disguises its operations through seemingly legitimate GitHub repositories.
Between September and October 2024, the attackers leveraged over 200 repositories managed by more than 225 Stargazer Ghost accounts to deliver malware to targets’ systems, exploiting victims’ trust in open-source platforms and legitimate-looking software repositories.
During this campaign, Check Point identified four distinct attack waves targeting developers and gamers between September 12 and October 3. Victims were lured into downloading compromised tools and games.
Although the security researchers only found GodLoader samples targeting Windows systems, they created proof-of-concept GDScript exploit code to demonstrate how easily the malware could be adapted for attacks on Linux and macOS systems.
Stargazer Goblin, the group behind the Stargazers Ghost Network DaaS platform, was first documented by Check Point in June 2023 promoting this malware service on the dark web. However, evidence suggests the group has been active since at least August 2022, generating over $100,000 in revenue since the service’s launch.
The Stargazers Ghost Network utilizes more than 3,000 GitHub “ghost” accounts to build networks of hundreds of repositories used to distribute malware. These repositories—primarily delivering information stealers like RedLine, Lumma Stealer, Rhadamanthys, RisePro, and Atlantida Stealer—are artificially boosted by starring, forking, and subscribing to push them into GitHub’s trending section, increasing their perceived credibility.
Update November 27, 18:19 EST: Godot Engine maintainer and security team member Rémi Verschelde provided the following statement after publication.
As the Check Point Research report states, the vulnerability is not specific to Godot. The Godot Engine is a programming system with a scripting language. It is akin to, for instance, the Python and Ruby runtimes. It is possible to write malicious programs in any programming language. We do not believe that Godot is particularly more or less suited to do so than other such programs.
Users who merely have a Godot game or editor installed on their system are not specifically at risk. We encourage people to only execute software from trusted sources.
For some more technical details:
Godot does not register a file handler for “.pck” files. This means that a malicious actor always has to ship the Godot runtime together with a .pck file. The user will always have to unpack the runtime together with the .pck to the same location and then execute the runtime. There is no way for a malicious actor to create a “one click exploit”, barring other OS-level vulnerabilities. If such an OS-level vulnerability were used then Godot would not be a particularly attractive option due to the size of the runtime.
This is similar to writing malicious software in Python or Ruby, the malicious actor will have to ship a python.exe or ruby.exe together with their malicious program.
Source: BleepingComputer, Sergiu Gatlan