The retail chain Fast Shop, specializing in electronics, published at 11 am today a statement informing “an attempt to unauthorized access to the company’s systems”. Since yesterday, there were rumors among security executives that three attacks were taking place, one of them against Fast Shop assets on the internet. Somehow, the cybercriminals who carried out the attack managed to gain access to the company’s Twitter account and made some publications realizing that they had seized data and providing a Telegram address for negotiation.
Dozens of users have reported problems and instability with the Fast Shop shopping site. A source from CISO Advisor reported that interestingly the DNS address used by the company had been changed yesterday, and the contact transferred to someone with an address in Pronton Mail. Today the change is undone.


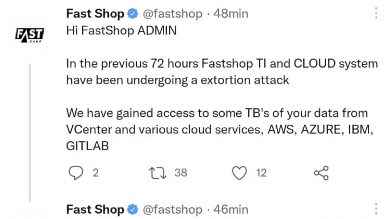
The cybercriminals apparently managed to use the company’s Twitter account to publicize the attack. (click to enlarge)
They said in two English-language posts that they had seized terabytes of data related to PCI (secure payments) protocols, as well as source code and personal and company data, without specifying which ones. They also said that the attack had been going on for 72 hours and that they had gained access to the company’s assets on AWS, Azure, GitLab and IBM, as well as VCenter.
At the same time, a post made by the same official profile but in Portuguese even announced the closing of stores until the 26th and the postponement of online orders until the 27th. This post is highlighted at the top of Fast Shop’s Twitter but the company informed officially that all stores are open. The Fast Shop sales website was unstable or down as indicated by a user’s post on Twitter (@konther). The company sent the following statement to CISO Advisor:
“Fast Shop informs that it has identified an attempt of unauthorized access to the company’s systems. As a form of prevention, the company activated the security protocols, and for this reason, the website and the app were temporarily unavailable, but they are already restored and working normally. We emphasize that all stores remain open and operating regularly throughout the country.
We emphasize that the entire information base of the company is under strict security processes and there was no evidence of damage to our customers’ data.”
Source: CisoAdvisor





















