Clorox and Cognizant
Clorox is suing IT giant Cognizant for gross negligence, alleging it enabled a massive August 2023 cyberattack by resetting an employee’s password for a hacker without first verifying their identity.
The incident first became public in September 2023 and reportedly involved hackers associated with Scattered Spider, who utilized a social engineering attack to breach the company.
The lawsuit states that Cognizant provided IT services to Clorox, including service desk support and identity management. This was the point of compromise that ultimately led to a devastating and costly cyberattack for the company.
Clorox is a major consumer goods company, best known for household cleaning products, bleach, disinfectants, and personal care items. In contrast, Cognizant is a global IT services and consulting company, providing cloud services, software development, and cybersecurity.
According to the complaint, from 2013 to 2023, Cognizant handled Clorox’s IT operations under contract.
“Cognizant operated the service desk (“Service Desk”) that Clorox employees could contact when they needed password recovery or reset assistance,” reads the complaint shared with BleepingComputer.
“Cognizant’s operation of the Service Desk came with a simple, common-sense requirement: never reset anyone’s credentials without properly authenticating them first. Clorox made this easy for Cognizant by providing straightforward procedures to follow whenever providing credential recovery or reset assistance.”
The Hacker
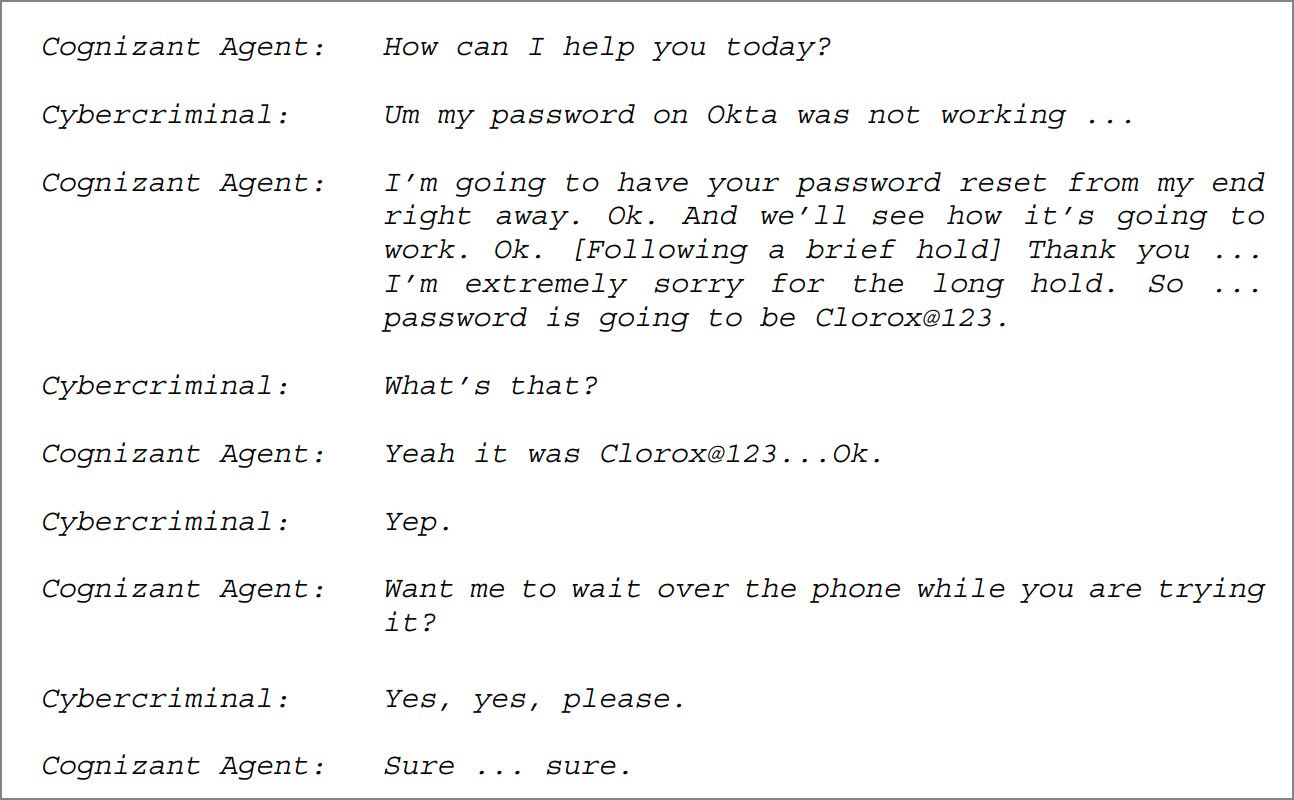
However, the complaint alleges that on August 11, 2023, recordings show that a cybercriminal called Cognizant’s Service Desk multiple times, pretending to be a Clorox representative requesting password and multi-factor authentication resets.
“At no point during any of the calls did the Agent verify that the caller was, in fact, Employee 1. At no point did the Agent follow Clorox’s credential support procedures—either the pre-2023 procedure or the January 2023 update—before changing the password for the cybercriminal. The Agent further reset Employee 1’s MFA credentials multiple times without any identity verification at all. And at no point did the Agent send the required emails to the employee or the employee’s manager to alert them of the password reset,” Clorox claims in the complaint.
This type of social engineering attack has become the hallmark of Scattered Spider attacks, which were recently used in UK retail attacks on Marks & Spencer and Co-op.
After allegedly failing to verify the caller’s actual identity, Cognizant reset the credentials and multi-factor authentication (MFA) for the hacker, thereby granting them access to Clorox’s IT network.
To make matters worse, Clorox alleges that the threat actors used the same playbook to reset the password and MFA for another employee who worked in IT security, which they accomplished without verification once again. This reportedly gave the attackers privileged access to the network, which they then used to spread to further devices.
Transcript of call between hacker and service desk
Source: Clorox complaint against Cognizant
Clorox states that Cognizant’s actions Paralyzed its corporate network, halted manufacturing, and caused widespread product shortages and business interruption.
In addition to this, Clorox described Cognizant’s response and recovery support as overly incompetent. This incompetence resulted in delays in applying containment measures, failure to shut down Compromised accounts, and sending Underqualified personnel on-site.
“The resulting Cyberattack was debilitating. It paralyzed Clorox’s corporate network and crippled business operations,” the legal complaint describes.
“And to make matters worse, when Clorox called on Cognizant to provide incident response and disaster recovery support services, Cognizant botched its response and compounded the damage it had already caused.”
Clorox’s lawsuit
Clorox’s complaint alleges breach of contract due to Cognizant’s failure to meet ITSA obligations, breach of good faith and fair dealing, gross Negligence, and Intentional Misrepresentation of staff training on the Client’s Credential reset procedures.
For these actions, which resulted in hundreds of millions of dollars in lost sales due to business disruption, as well as Reputational damage with long-term consequences, Clorox seeks $49 million in direct Remediation damages and $380 million in total damages.
[Update 7/24 03:00 AM EST] – A Cognizant spokesperson sent BleepingComputer the following comment:
“It is shocking that a corporation the size of Clorox had such an inept internal cybersecurity system to mitigate this attack. Clorox has tried to blame us for these failures, but the reality is that Clorox hired Cognizant for a narrow scope of help desk services, which Cognizant reasonably performed. Cognizant did not manage cybersecurity for Clorox.” – Cognizant
Source: BleepingComputer, Bill Toulas
Read more at Impreza News