The latest incarnation of the notorious BreachForums hacking forum has experienced a data breach, after attackers leaked its user database table online.
BreachForums refers to a series of hacking forums that cybercriminals use to trade, sell, and leak stolen data. In addition, members use the platform to sell access to corporate networks and offer other illegal cybercrime services.
The operators launched the site after law enforcement seized the original forum, RaidForums, and arrested its owner, “Omnipotent.”
Although BreachForums has endured data breaches and police actions in the past, operators have repeatedly relaunched the site under new domains. As a result, some researchers and users have accused the forum of operating as a potential law-enforcement honeypot.
ShinyHunters-Named Website Releases Archive
Yesterday, a website named after the ShinyHunters extortion gang released a 7Zip archive titled breachedforum.7z.
The archive contains three files:
- shinyhunte.rs-the-story-of-james.txt
- databoose.sql
- breachedforum-pgp-key.txt.asc
However, a representative of the ShinyHunters extortion gang told BleepingComputer they are not affiliated with the website that distributed the archive.
Leaked PGP Key Raises Limited Risk
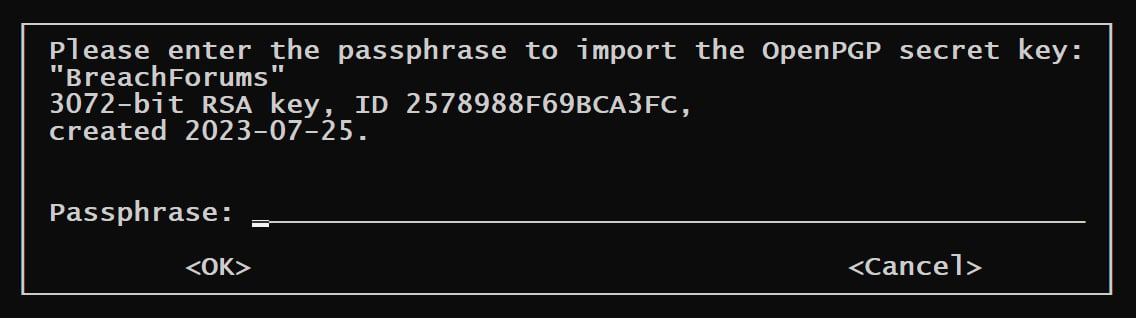
The breachedforum-pgp-key.txt.asc file contains a PGP private key created on July 25, 2023, which BreachForums administrators used to sign official messages. Although attackers leaked the key, it remains protected by a passphrase. Without that password, threat actors cannot abuse it to sign administrative messages.
Passphrase-protected BreachForums PGP private key
Source: BleepingComputer
Meanwhile, the databoose.sql file contains a MyBB users database table (mybb_users) with 323,988 member records. These records include display names, registration dates, IP addresses, and other internal data.
After analyzing the table, BleepingComputer found that most IP addresses map to a local loopback address (0x7F000009 / 127.0.0.9). Consequently, those records provide little practical value.
Thousands of Public IPs Pose OPSEC Concerns
However, 70,296 records do not contain the 127.0.0.9 IP address. The tested entries instead map to public IP addresses. As a result, these records could pose operational security (OPSEC) concerns for affected users and offer valuable intelligence to law enforcement and cybersecurity researchers.
Notably, the most recent registration date in the leaked database is August 11, 2025. That date matches the day operators shut down the previous BreachForums instance hosted at breachforums[.]hn, following the arrest of some alleged operators.
On the same day, a member of the ShinyHunters extortion gang posted a message in the “Scattered Lapsus$ Hunters” Telegram channel, claiming the forum functioned as a law-enforcement honeypot. Shortly afterward, BreachForums administrators denied the accusation.
Later, in October 2025, law enforcement seized the breachforums[.]hn domain. Authorities took action after criminals repurposed the site to extort companies affected by the widespread Salesforce data theft attacks attributed to the ShinyHunters extortion group.
Administrator Confirms Backup Exposure
The current BreachForums administrator, known as “N/A,” has since acknowledged the new breach. According to N/A, an unsecured folder temporarily exposed a backup of the MyBB user database table, and an unknown party downloaded it only once.
“We want to address recent discussions regarding an alleged database leak and clearly explain what happened,” N/A wrote on BreachForums.
“First of all, this is not a recent incident. The data in question originates from an old users-table leak dating back to August 2025, during the period when BreachForums was being restored/recovered from the .hn domain.”
“During the restoration process, the users table and the forum PGP key were temporarily stored in an unsecured folder for a very short period of time. Our investigation shows that the folder was downloaded only once during that window,” continued the administrator.
Although the administrator advised members to use disposable email addresses and emphasized that most IP addresses map to local addresses, the exposed database still contains information that could attract law enforcement interest.
Source: BleepingComputer, Lawrence Abrams
Read more at Impreza News