The Google Project Zero team identified 24 zero days being exploited by cybercriminals in 2020. A quarter of the problems they caused could have been avoided if vendors corrected their products properly, experts said.
Six were variations of vulnerabilities discovered in previous years, when attackers had access to vulnerability reports, which allowed them to study the problem and deploy a new version of the exploit. According to experts, in some cases it was enough to change a line or two of code to get a new working exploit.
As noted by them, the first patches for zero day vulnerabilities in Chrome (CVE-2020-6572), Internet Explorer (CVE-2020-0674) and Windows (CVE-2020-0986) required additional patches. If an attacker were to analyze the patch data, they could easily create new exploits, exploit the same vulnerability again, and continue their attacks.
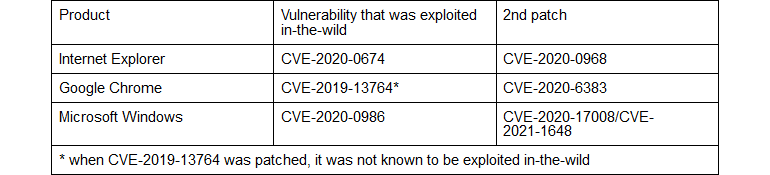
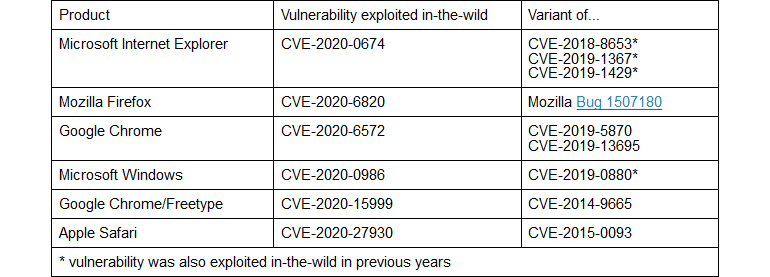
The researchers reported that these situations could have been avoided if suppliers investigated the root cause of the problem more closely and invested more in the remediation process.
See the original post at: https://www.cisoadvisor.com.br/25-dos-zero-days-sao-o-resultado-de-correcoes-inadequadas/?rand=59039