Unidentified cybercriminals attacked and compromised the server infrastructure of NoxPlayer – an Android emulator application for Windows and Macbook, developed by BigNox – and with that, sent malware to five specific victims in Asia. A targeted attack on the supply chain, with no identified officers, reports ESET.
At the end of January this year, researchers from ESET (Slovak information security company) identified that an API server, “api.bignox.com”, just like a database server, “res06.bignox.com”, belonging to BigNox, were committed to September 2020.
BigNox is a software developer based in Hong Kong. According to the company itself, the NoxPlayer emulator, its main product to date, has more than 150 million users around the world, mostly Asian.
The attack
As ESET explains, with access to servers (API and database), cybercriminals have tampered with the address of a NoxPlayer update, replacing it with an update infected with at least 3 types of malware, tailored to target certain users.
This attack is very similar to the attack on SolarWinds’ supply chain, which started in late December 2020, which had no purpose of damaging data, but of spying on users of the compromised solution.
“Three different malware families were found being distributed from customized malicious updates to selected victims, with no sign of leverage of any financial gain, but resources related to surveillance”Writes Ignacio Sanmillan, a malware researcher at ESET.
Although the company has more than 150 million users worldwide. Cybercriminals were not interested in watching all users of this tool. The attack was aimed at only five Asians, divided between the countries, Taiwan, Hong Kong and Sri Lanka.
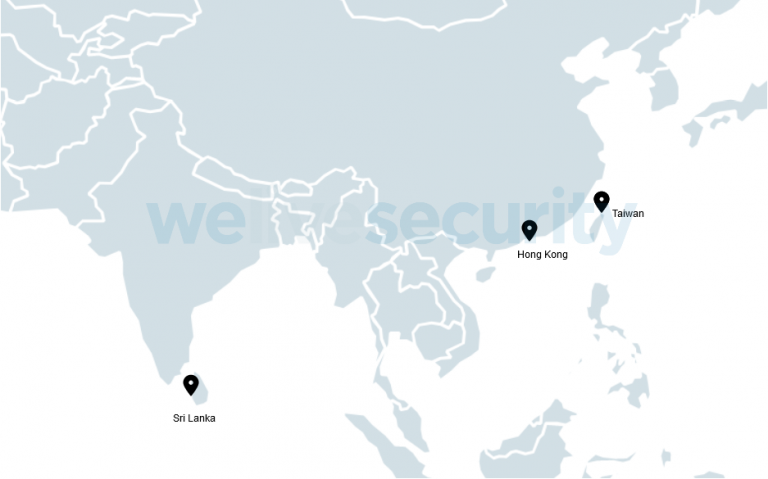
“Compared to the overall number of active NoxPlayer users, there are a very small number of victims. According to ESET telemetry, over 100,000 users have NoxPlayer installed on their machines. Among them, only 5 users received a malicious update, showing that Operation NightScout is a highly targeted operation ”, writes researcher Sanmillan.
ESET reports that it contacted BigNox to offer security solutions and internal investigation, but the company denied having been attacked. “We contacted BigNox about the intrusion and they denied being affected. We also offer our support to help them overcome disclosure, should they decide to conduct an internal investigation, ”says Sanmillan.
This is the third attack on the supply chain discovered by ESET since December 2020. The first involves the human resource management software Able used by the government of Mangolia. The second involves software for issuing official certifications, used by the government of Vietnam.
“We detected several attacks on the supply chain last year [… O ataque que envolve o NoxPlayer] it is particularly interesting due to the directed vertical, since we rarely find many cyber espionage operations targeting online players […] The attacks on the supply chain will continue to be a vector of common commitment, leveraged by cyber espionage groups, and its complexity can impact the discovery and mitigation of this type of incident ”, concludes the researcher.
Source: Welivesecurity (ESET).
See the original post at: https://thehack.com.br/cibercriminosos-comprometem-emulador-noxplayer-para-espionar-cinco-vitimas-especificas/?rand=48873










