A new commercial mobile spyware platform dubbed ZeroDayRAT is actively advertised to cybercriminals on Telegram as a tool that provides full remote control over compromised Android and iOS devices.
Specifically, the malware gives buyers access to a full-featured panel for managing infected devices and reportedly supports Android versions 5 through 16 and iOS up to the latest version 26.
According to researchers at mobile threat hunting company iVerify, ZeroDayRAT not only steals data but also enables real-time surveillance and financial theft.
To begin with, the dashboard displays compromised devices alongside detailed information such as the device model, operating system version, battery status, SIM details, country, and lock state.
Dashboard overview
Source: iVerify
Additionally, the malware logs app usage, activity timelines, and SMS message exchanges, while presenting operators with a consolidated overview of victim activity.
Account Monitoring and Notification Tracking
Beyond basic monitoring, other tracking tabs on the dashboard display all received notifications and list registered accounts on the infected device. These entries include email addresses or user IDs, which potentially enable brute-forcing and credential stuffing attacks.
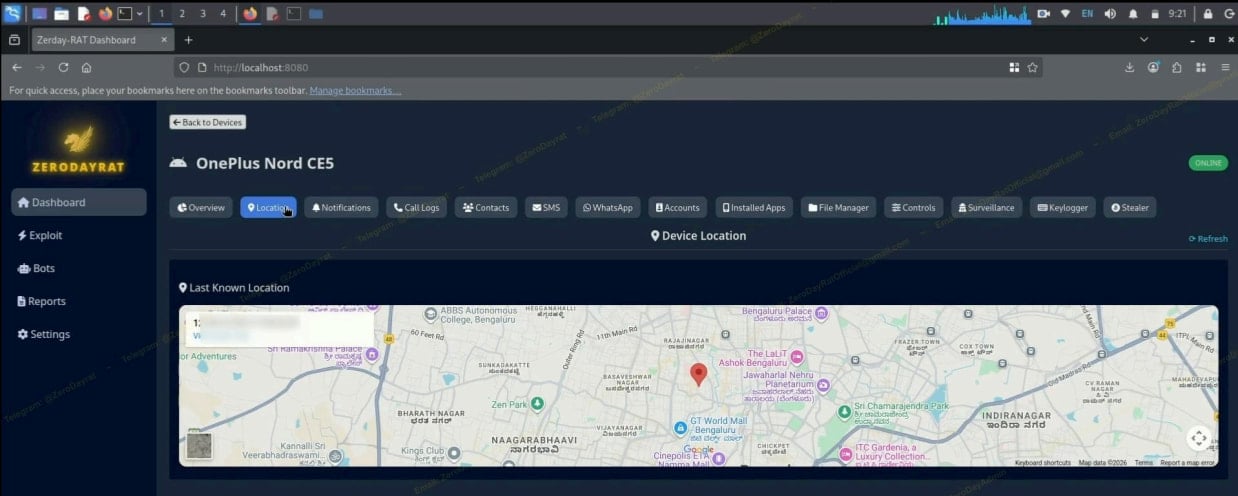
Furthermore, if the attacker secures GPS access, the malware tracks the victim in real time and plots their current position on a Google Maps view. It also maintains a complete location history.
Tracking the victim in real time
Source: iVerify
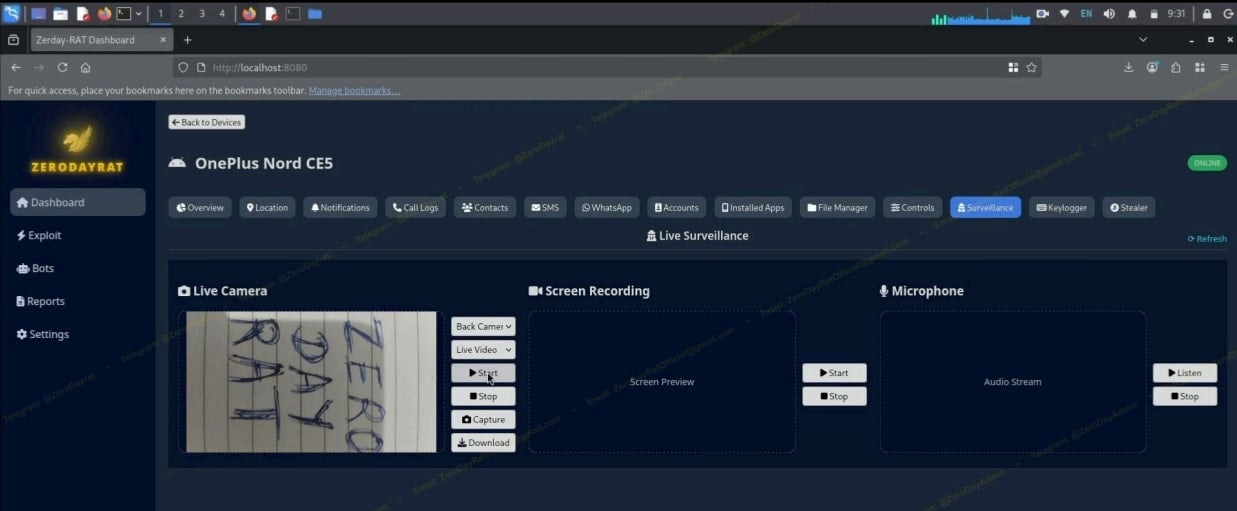
In contrast to purely passive data collection, ZeroDayRAT also supports active, hands-on operations. For example, the malware can activate both front and rear cameras, as well as the microphone, to provide live media feeds. It can also record the victim’s screen to expose additional sensitive information.
Accessing camera and microphone feeds
Source: iVerify
Moreover, when attackers secure SMS access permissions, the malware captures incoming one-time passwords (OTPs), enabling 2FA bypass, and can even send SMS messages directly from the victim’s device.
At the same time, the developer included a keylogging module that captures user input, including passwords, gestures, and screen unlock patterns.
Cryptocurrency and Banking Theft Modules
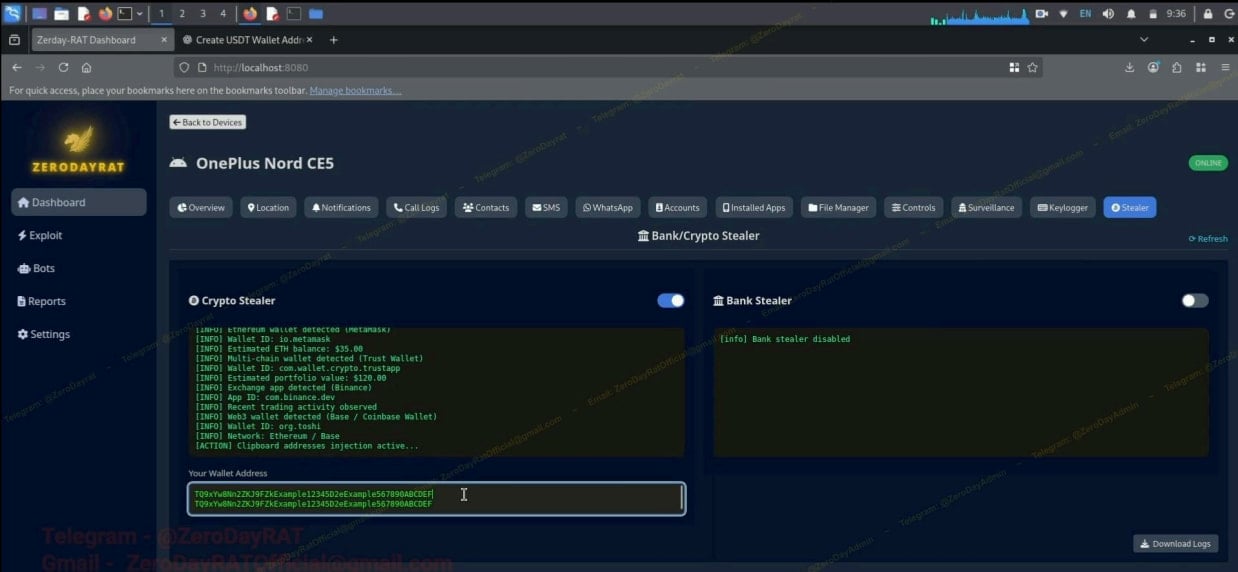
In addition, ZeroDayRAT enables further financial theft through a dedicated cryptocurrency stealer module. Researchers found that this component activates a wallet app scanner targeting MetaMask, Trust Wallet, Binance, and Coinbase. It logs wallet IDs and balances and attempts clipboard address injection by replacing copied wallet addresses with attacker-controlled ones.
Similarly, the bank stealer targets online banking applications, UPI platforms such as Google Pay and PhonePe, and payment services including Apple Pay and PayPal. The malware steals credentials by overlaying fake login screens.
The crypto and bank stealer modules
Source: iVerify
Although iVerify does not detail how attackers deliver the malware, the researchers state that ZeroDayRAT “is a complete mobile compromise toolkit.” They further warn that a compromised employee device could lead directly to enterprise breaches.
Impact on Individuals and Security Recommendations
For individual users, a ZeroDayRAT infection could expose private data and result in significant financial losses.
To reduce risk, users should only trust official app stores — Google Play on Android and the Apple App Store on iOS — and install applications exclusively from reputable publishers. Additionally, high-risk users should consider enabling Lockdown Mode on iOS and Advanced Protection on Android.
Source: BleepingComputer, Bill Toulas
Read more at Impreza News














.jpg)