According to Cloudflare’s Application Security report for 2024, threat actors rapidly weaponize proof-of-concept (PoC) exploits, sometimes within 22 minutes of public release. The report, which covers activity from May 2023 to March 2024, highlights emerging threat trends.
Cloudflare, processing an average of 57 million HTTP requests per second, continues to observe increased scanning activity for disclosed CVEs, followed by command injections and attempts to weaponize PoCs.
The most targeted flaws during this period included CVE-2023-50164 and CVE-2022-33891 in Apache products, CVE-2023-29298, CVE-2023-38203, and CVE-2023-26360 in Coldfusion, and CVE-2023-35082 in MobileIron.
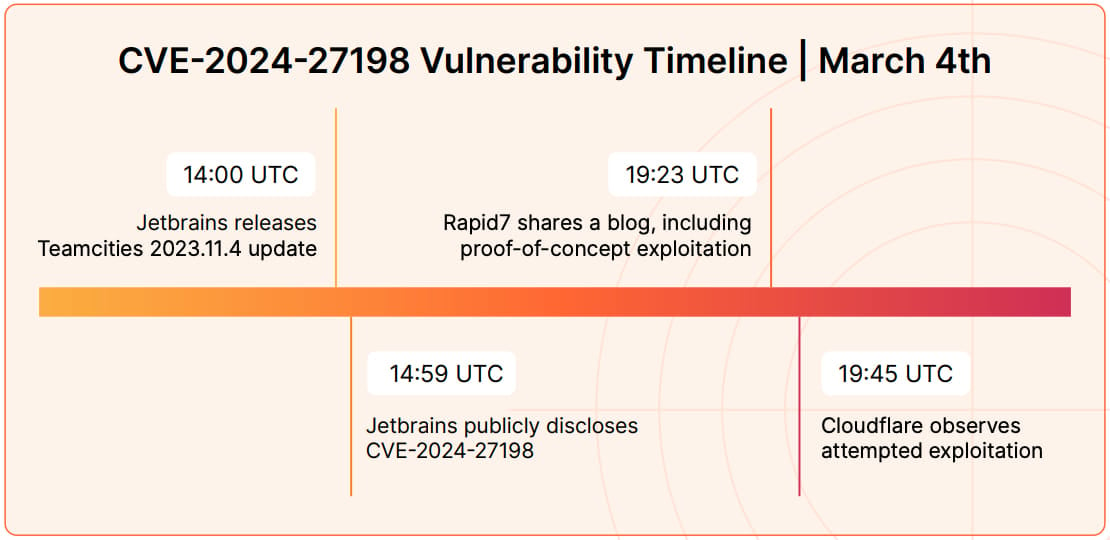
An example of the accelerated weaponization is CVE-2024-27198, an authentication bypass flaw in JetBrains TeamCity. Cloudflare noted an incident where an attacker used a PoC exploit 22 minutes after its release, giving defenders almost no time to respond.
CVE exploitation speed
Source: Cloudflare
The internet firm states that the only way to counter this rapid exploitation is to use AI assistance to swiftly develop effective detection rules.
“Exploitation of disclosed CVEs often outpaces the creation of WAF rules and deployment of patches by humans,” Cloudflare explains.
“This challenge also affects our internal security analyst team responsible for maintaining the WAF Managed Ruleset, prompting us to combine human-written signatures with a machine learning-based approach to balance low false positives and fast response times.”
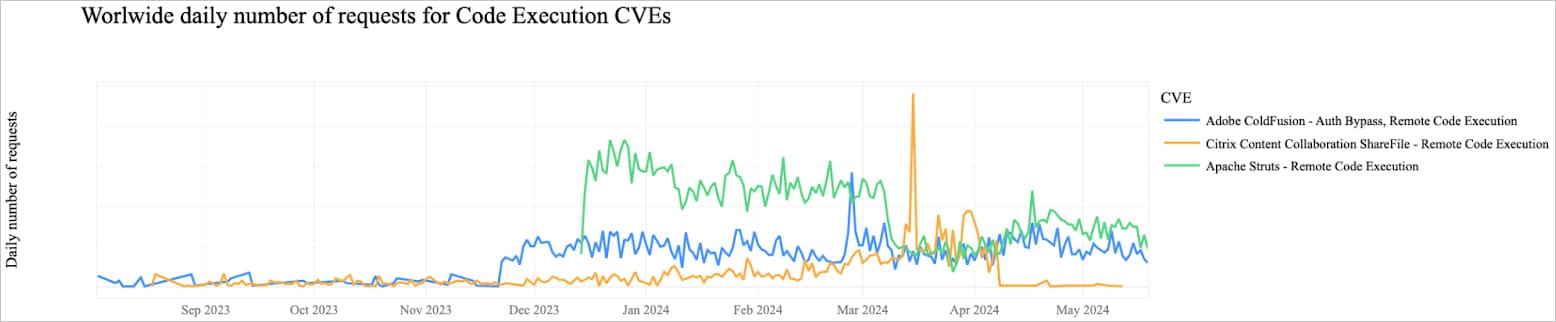
Cloudflare notes that this is partly due to certain threat actors specializing in specific CVE categories and products, enabling them to quickly exploit new vulnerabilities.
RCE exploitation attempts focusing on specific products
Source: Cloudflare
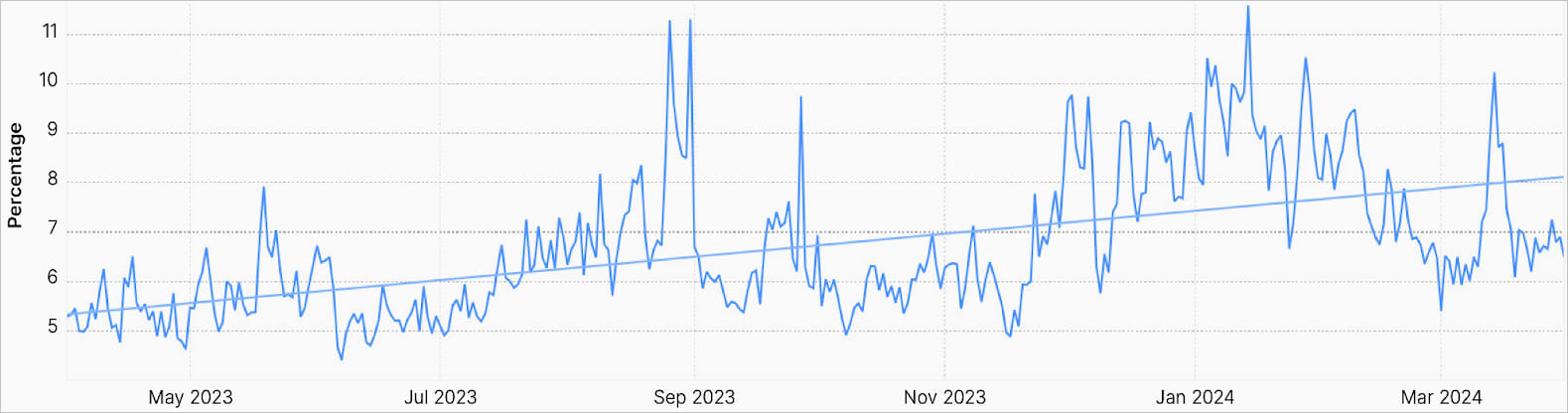
6.8% of all internet traffic is DDoS
Another striking highlight in Cloudflare’s report is that 6.8% of all daily internet traffic consists of distributed denial of service (DDoS) attacks, targeting online apps and services to make them inaccessible to legitimate users.
Percentage of mitigated HTTP traffic
Source: Cloudflare
This marks a significant rise from the 6% recorded in the previous 12-month period (2022-2023), indicating an increase in the overall volume of DDoS attacks.
Cloudflare reports that during major global attack events, malicious traffic can account for up to 12% of all HTTP traffic.
“In Q1 2024, focusing on HTTP requests alone, Cloudflare blocked an average of 209 billion cyber threats daily, an 86.6% year-over-year increase,” Cloudflare states.
The firm’s PDF report, available for download here, offers further recommendations for defenders and detailed insights into the compiled statistics.
Source: BleepingComputer, Bill Toulas