Cybercriminals allegedly linked to the Russian government are directing attacks on a number of US companies and government agencies. The Department of Commerce, the Department of the Treasury, the National Telecommunications, Information and Administration Agency (NTIA), in addition to other US government institutions are among the main victims.
According to The Washington Post, which received anonymous information from people directly linked to the case, the attacks may have been organized by the APT29 group (also known as Cozy Bear), the same group responsible for the theft of tools from the red team, FireEye’s defense solutions testing group. Cybercriminals have even succeeded access to the internal emails of some of the institutions mentioned.
As anonymous sources explain to the newspaper, cybercriminals reportedly inserted trojans into an update to SolarWinds’ IT management platform, the Orion software. This manipulated and malicious code update (with legitimate SolarWinds signature), when installed by customers, created a backdoor that frees access to the IT infrastructure monitored by the SolarWinds platform.
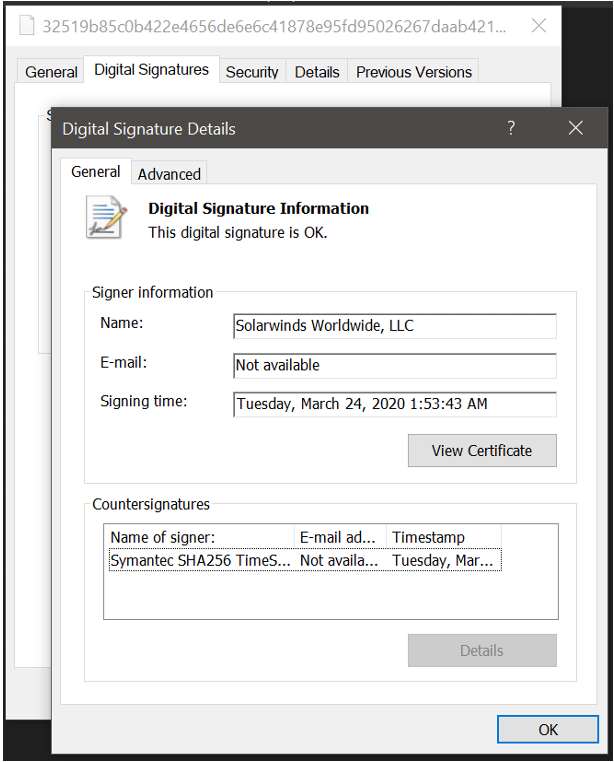
The main purpose of the attacks is to infiltrate government networks, as well as networks of private companies, such as FireEye, which has governments as customers and, with that, mount a sophisticated supply chain attack.
SolarWinds reports that the attack targets 2019.4 through 2020.2 versions of its IT management software. “We were told that this attack was probably led by a nation-state external and destined to be a narrow attack, extremely targeted and executed manually, as opposed to a system-wide attack, ”writes the company in a security statement, published on Saturday (12).
The US Infrastructure Security and Cybersecurity Agency (CISA) has asked companies and organizations linked to the US government and SolarWinds customers to review their networks for suspicious activity.
THE SolarWinds is a developer of IT solutions which also offers infrastructure services. Based in Texas, USA, it has more than 300 thousand customers worldwide all, which includes multinationals mentioned in the Fortune 500 ranking, government agency and institutions, as well as universities and educational institutions.
In the United States alone, SolarWinds works closely with several telecommunications companies, all five branches of the army, Pentagon, State Department, NASA, National Security Agency (NSA), postal service, National Oceanic and Atmospheric Administration (NOAA), Department of Justice and the office of the President of the USA.
FireEye, which is investigating the case with SolarWinds and the FBI, reports that this complex campaign may have started between March, April and May 2020 and is still ongoing. “The campaign is the work of a highly qualified actor and the operation was conducted with significant operational security”, Informs the company in a report on the backdoor.
“SolarWinds.Orion.Core.BusinessLayer.dll is a digitally signed component of SolarWinds’ Orion software, which contains a backdoor that communicates via HTTP with third party servers. We are tracking the trojanized version of this SolarWinds Orion plug-in as SUNBURST, ”write the researchers in the FireEye report.
Sources: The Washington Post; SolarWinds; FireEye.
See the original post at: https://thehack.com.br/agencias-dos-eua-sao-atacadas-pelo-mesmo-grupo-que-invadiu-a-fireeye/?rand=48873











